Introducing "AI Unlocked: Decoding Prompt Injection," a New Interactive Challenge
AI Unlocked: Decoding Prompt Injection begins in the Command Center room, where players have to use…
AI Unlocked: Decoding Prompt Injection begins in the Command Center room, where players have to use…
Insider threats pose a growing risk to organizations. Whether insiders take malicious actions, exhibit negligent behavior,…
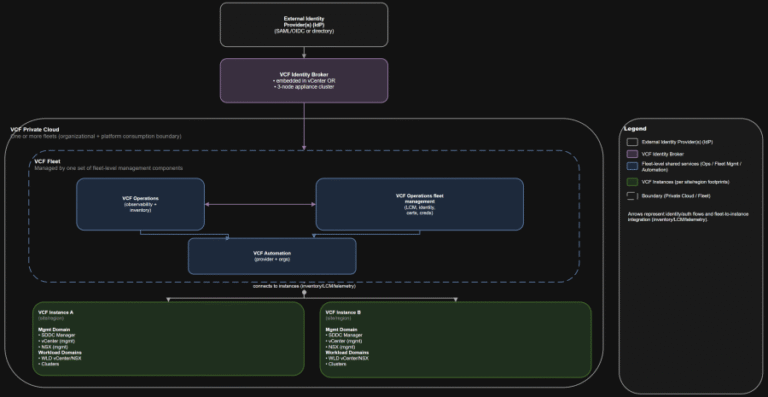
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…

In this article, you will learn how to list, configure, enable, disable, and troubleshoot network interfaces…
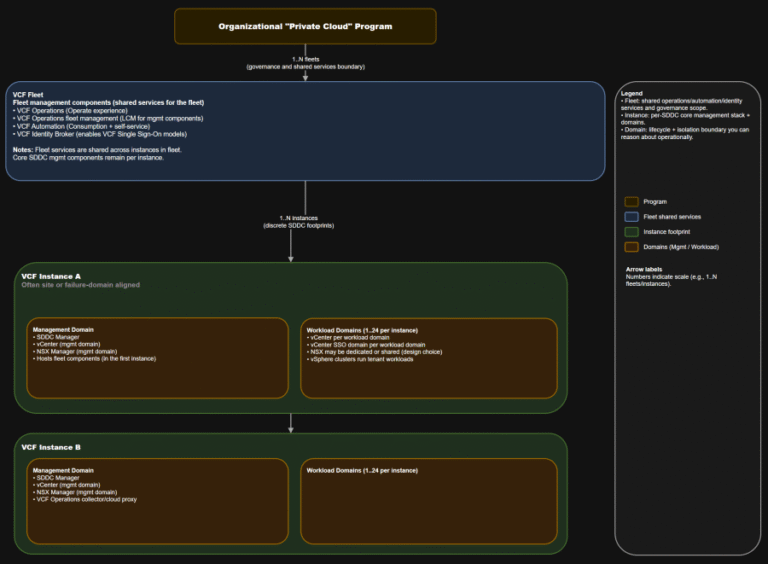
TL;DR This is the “where do we do the thing” map you want in every runbook….

About Volusion A redesign allows your store to align with your current brand identity and tell…
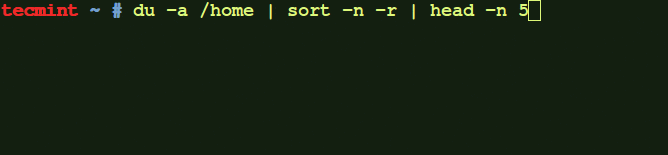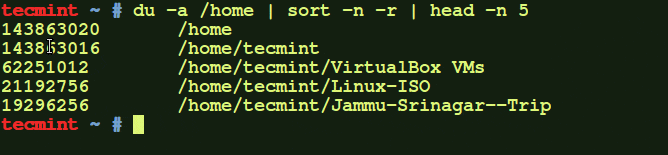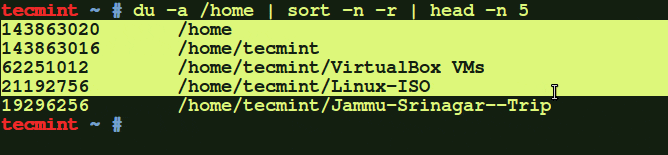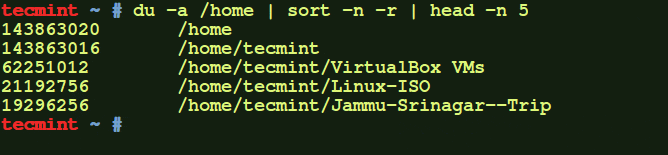
As a Linux administrator, you must periodically check which files and folders are consuming more disk…
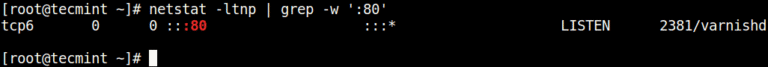
In this article, you will learn how to find which process or service is listening on…
CrowdStrike Falcon Identity Protection — A Great Tool to Gain Visibility We remain committed to innovating…

Whether you’re building your first automation workflow or exploring how AI can simplify everyday SOC tasks,…
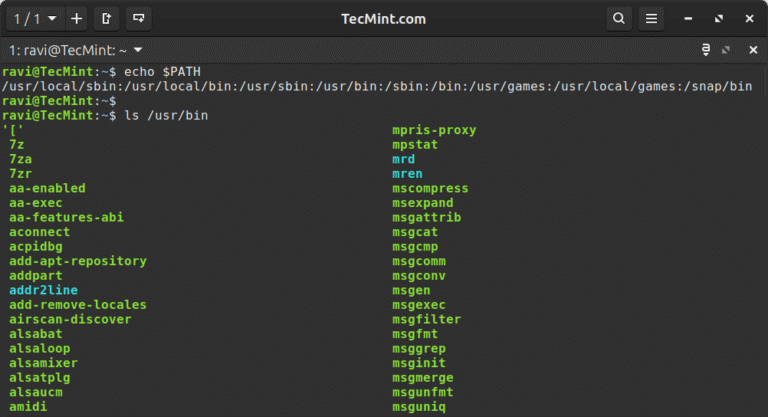
In this guide, you’ll learn five practical commands for discovering quick information about any binary command:…
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…
Actively Exploited Zero-Day Vulnerability in Windows Remote Desktop The vulnerability allows local attackers with no privileges…
In this article, you will learn how to use the Linux column command to format text…

– System Engineer, IT Services “Overall, it’s been a valuable and eye-opening experience. The tool has helped…