How to Extend Root Partition in Linux
As a Linux user, you may eventually run into a situation where your root partition (/)…

As a Linux user, you may eventually run into a situation where your root partition (/)…
The Hub doesn’t just display what’s happening — it tells teams what to do about it…

Want to play Windows games on your Linux system but not sure where to begin? Heard…
Do you feel like your Ubuntu desktop turns messy the moment you open more than a…
Publicly Disclosed Zero-Day Vulnerability in Windows SMB CVE-2025-55226 is a Critical remote code execution vulnerability affecting…

Make the process as simple as possible by offering guest checkout options, enabling auto-fill for payment…
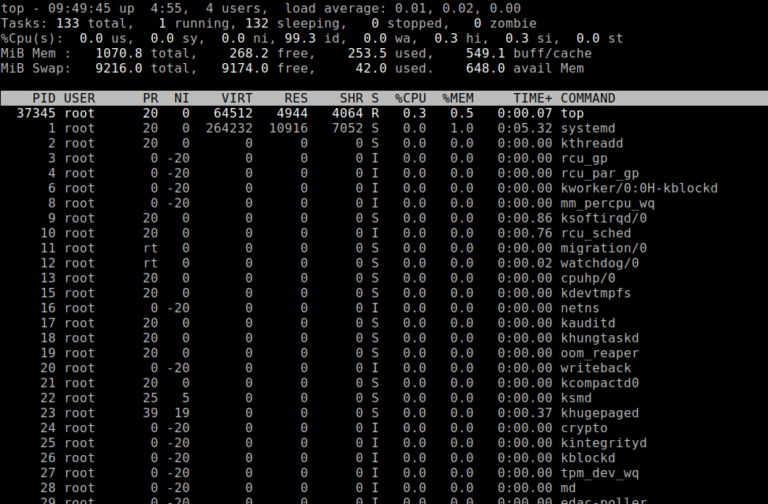
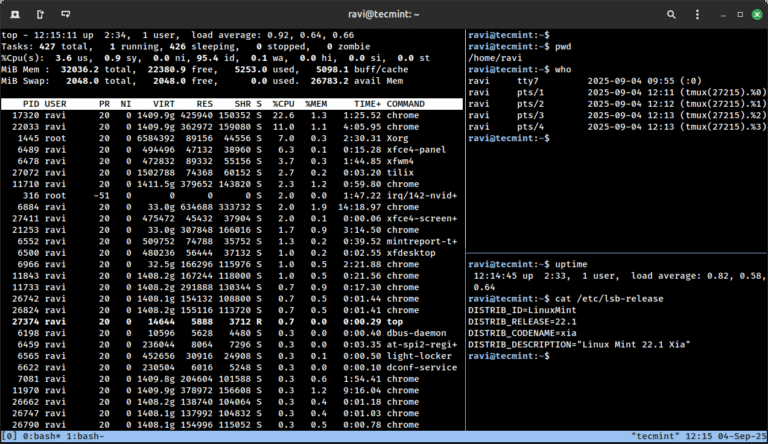
Being a System or Network administrator tasked with monitoring and debugging Linux system performance problems on…
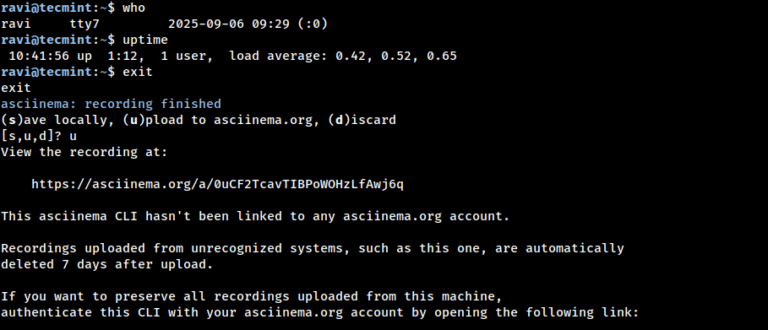
Asciinema is an open-source terminal recording tool that makes it super easy to share your command-line…
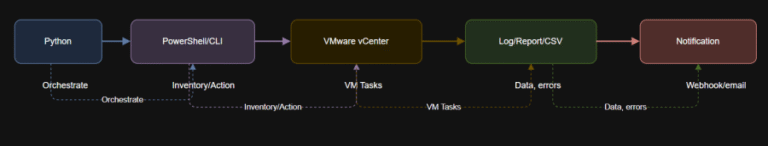
Learning Objectives VMware Repository on GitHub See how a single Python script can orchestrate inventory, lifecycle,…
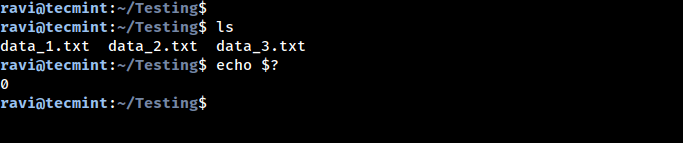
When working on a Linux system, every command you run returns a status code (also called…

DNS (Domain Name System) is a fundamental facilitator of several networking technologies such as mail servers,…
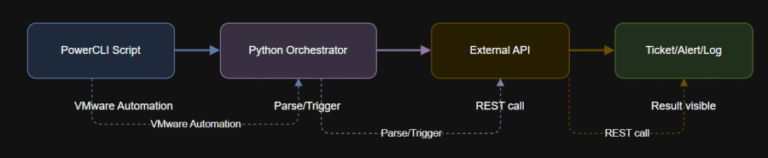
Learning Objectives $message = @{text = “VM $vmName has been powered off via automation.”} | ConvertTo-Json…
It is time once again to share a list of the best free and open-source software…
As someone who has been using Linux for more than 12 years, I’ve often come across…
A Visionary Leader in MDR See what other industry analysts are saying about CrowdStrike on our…