CrowdStrike Achieves NCSC CIR Assurance for Incident Response
This milestone comes as the UK places increased emphasis on cyber resilience, operational assurance, and incident…
This milestone comes as the UK places increased emphasis on cyber resilience, operational assurance, and incident…

Stopping compromised access at login is essential, but identity risk doesn’t end there. CrowdStrike acquired SGNL…
To defend themselves, security leaders need clarity on which adversaries to watch, the details of their…
Adversaries’ ability to easily establish seemingly legitimate infrastructure poses significant risks to organizations of all sizes….
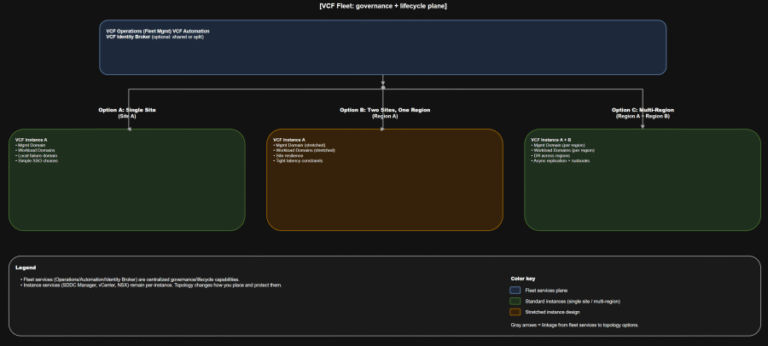
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
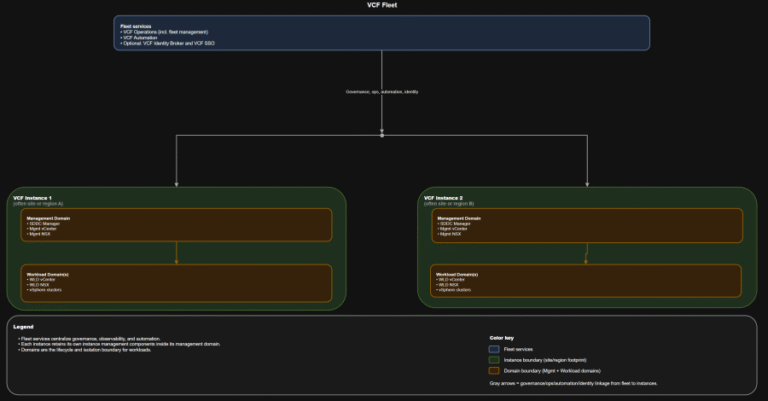
TL;DR Identity is not a “later” decision. It is a boundary decision. The hierarchy you should…
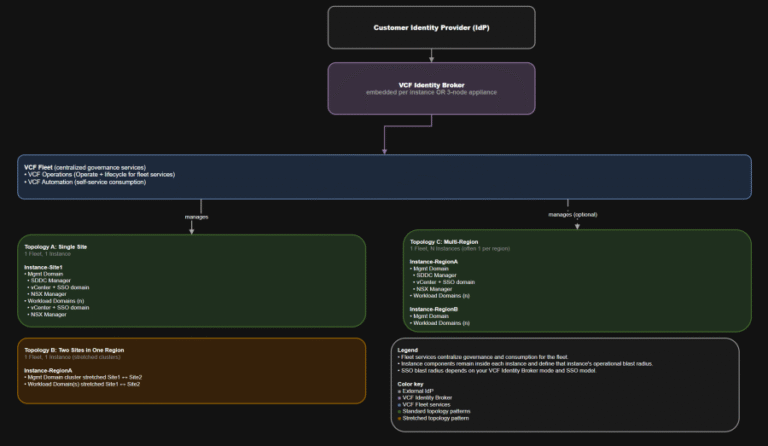
TL;DR This post targets VCF 9.0 GA only: VCF 9.0 (17 JUN 2025) build 24755599, with…
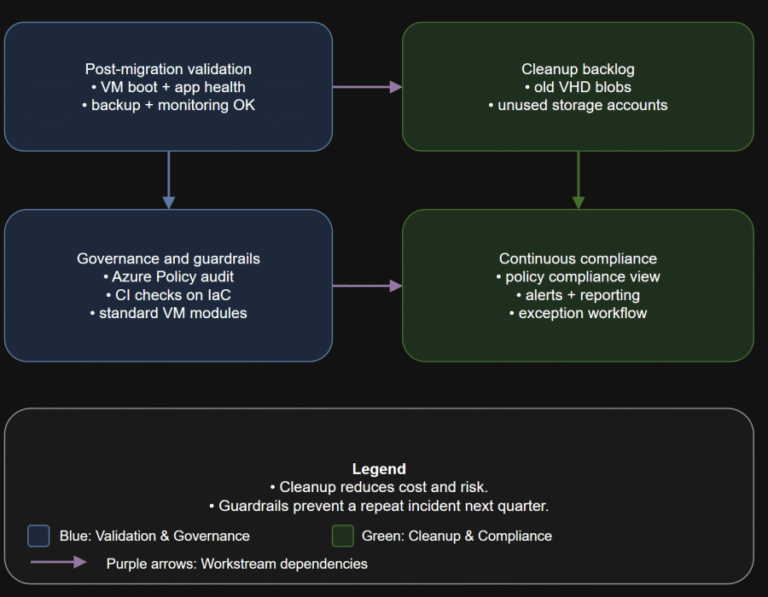
TL;DR Converting disks is not the finish line. Your real goal is a new steady state:…
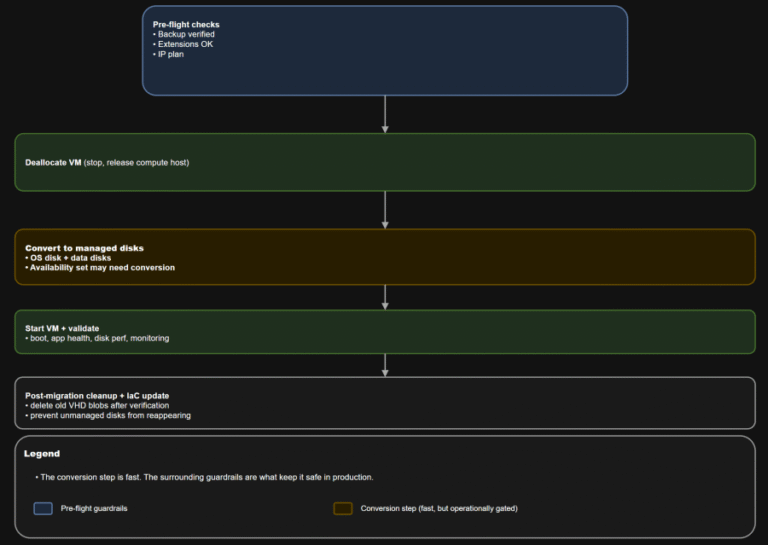
TL;DR Converting a VM to managed disks is usually operationally straightforward: deallocate, convert, start, validate. The…
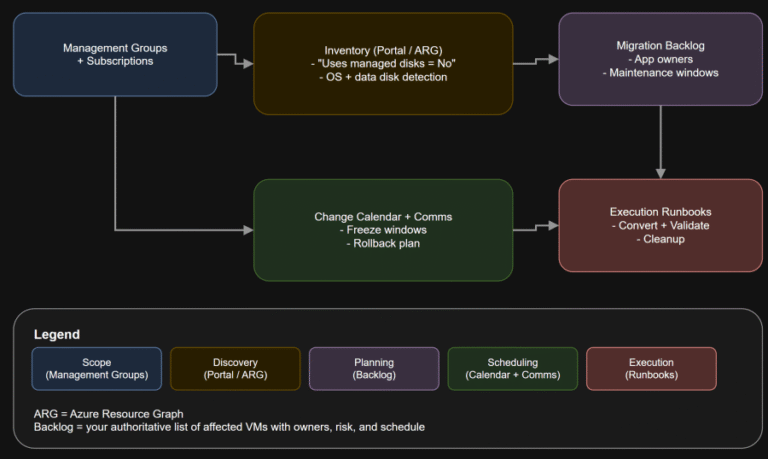
TL;DR If any Azure IaaS VM in your estate still uses unmanaged disks, it is on…
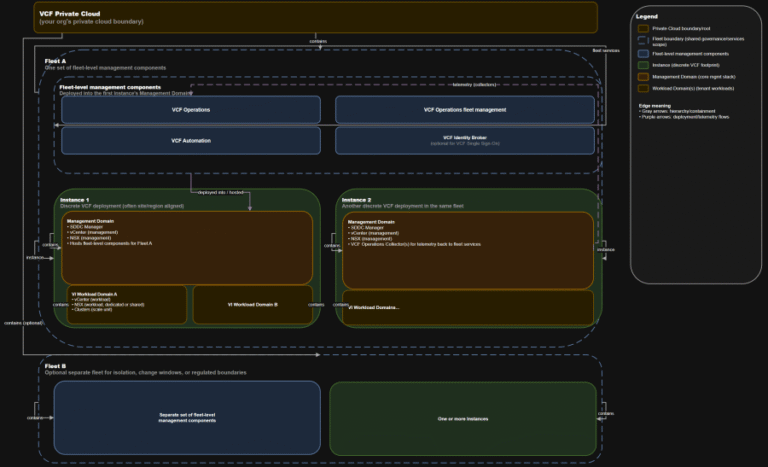
TL;DR A) One fleet, one instance, stretched where justified In VCF 9.0, identity is not a…
AI Unlocked: Decoding Prompt Injection begins in the Command Center room, where players have to use…
Insider threats pose a growing risk to organizations. Whether insiders take malicious actions, exhibit negligent behavior,…
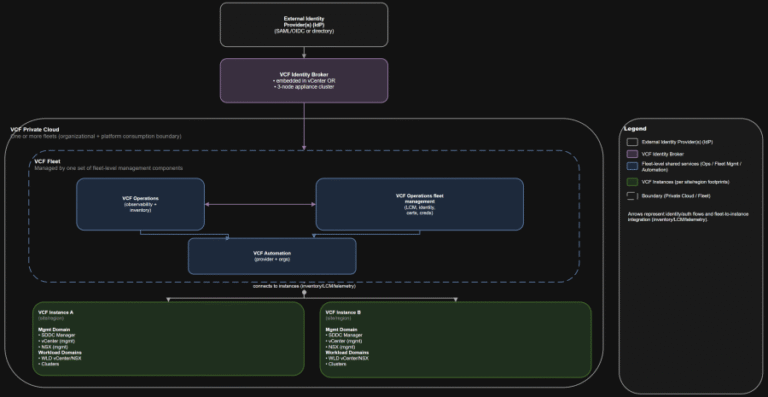
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…

In this article, you will learn how to list, configure, enable, disable, and troubleshoot network interfaces…