August 2025 Patch Tuesday: One Publicly Disclosed Zero-Day and 13 Critical Vulnerabilities Among 107 CVEs
Publicly Disclosed Zero-Day Vulnerability in Windows Kerberos As we have learned with other notable vulnerabilities, such…
Publicly Disclosed Zero-Day Vulnerability in Windows Kerberos As we have learned with other notable vulnerabilities, such…
“CrowdStrike’s cloud-native security platform employs an adversarial approach, consolidating telemetry from various security domains to deliver…
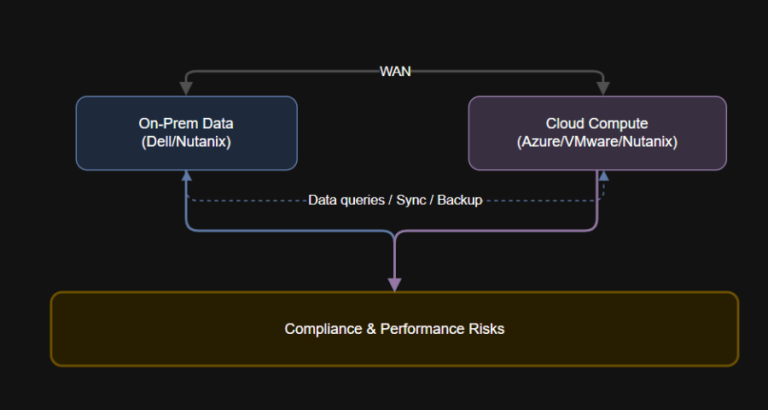
Introduction: What Is Data Gravity? Data gravity is a defining factor in successful cloud migration and…
“Leakage” in machine learning (ML) occurs when data that an ML model should not learn on…
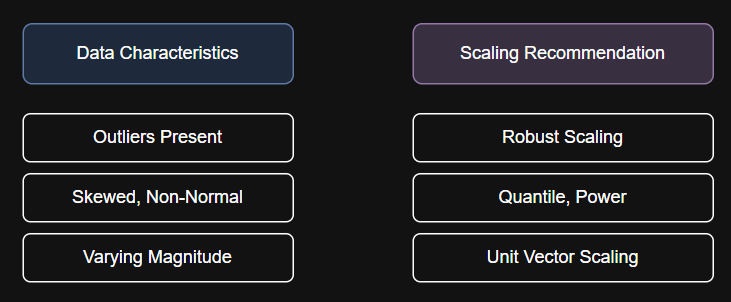
We will cover the following techniques, with step-by-step Python code for each: print(“Original Data:n”, X.ravel())print(“Robust Scaled:n”,…
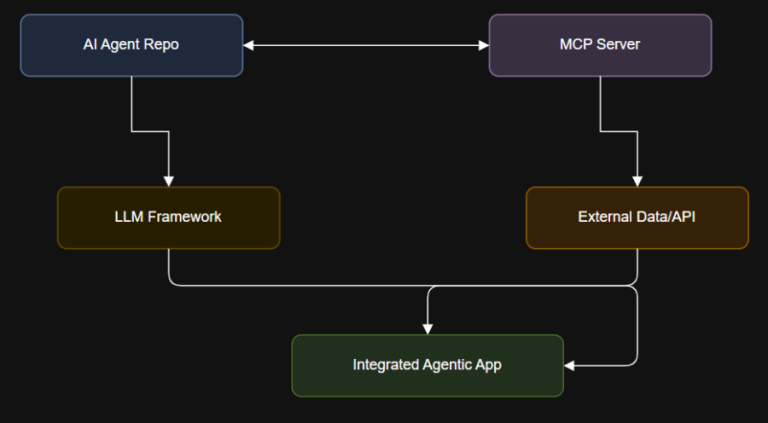
1. Learn AI and LLMs from Scratch Repo: coleam00/ai-agents-masterclassAll code and resources from the AI Agents…
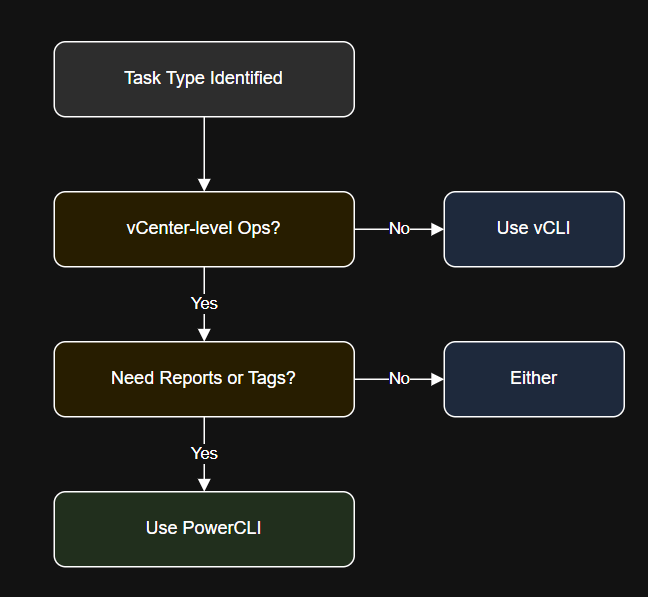
Introduction In this article, you’ll learn: Install using VMware downloads or use the VMA (vSphere Management…
These 15 free AI tools represent the best in practical productivity and innovation for 2025. From…
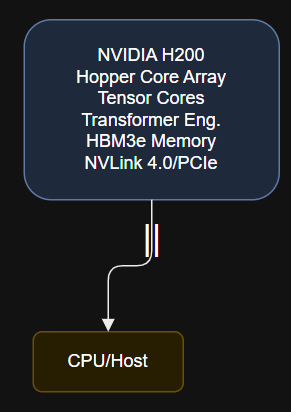
Why GPUs Matter in AI Workloads AMD’s Instinct MI300X, announced for production in 2025, is built…
AI must be deployed strategically in the SOC to outpace AI-savvy adversaries. The Threat Hunting Report…
Where these traditional tools stay silent, CrowdStrike Signal takes action. It identifies activity that deviates from…
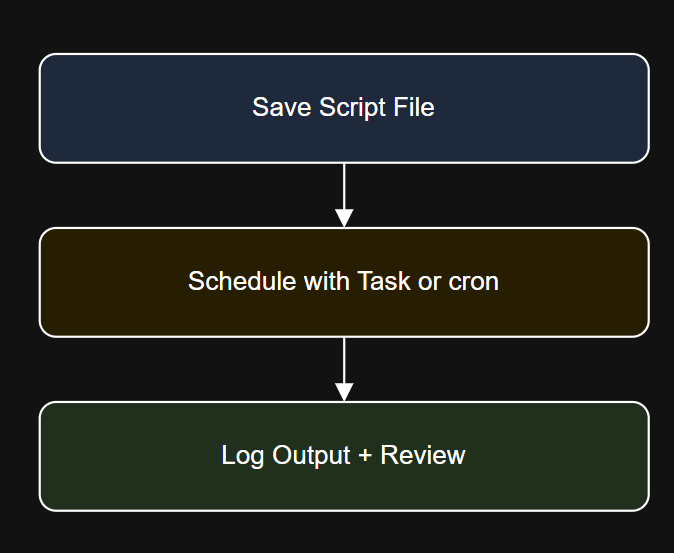
Introduction crontab -l Diagram: PowerCLI Scheduling Workflow Step 4: Use Credential Storage Securely Click OK, enter…
With Falcon Shield’s integration with OpenAI ChatGPT Enterprise Compliance API, IT and security teams gain added…

This enhanced workflow turns every indicator into actionable intelligence so teams can conduct smarter, faster investigations….
But with this integration comes risk. AI agents are often quickly deployed across SaaS environments by…