Feel free to check in on this series:
Prior to Software Defined Networking solutions, physical datacenters were limited to broadcast domains with up to 4096 on each device.
Multi-Tenancy infrastructure is a game-changer in the world of cloud computing and onprem Software Defined Networking. It allows multiple tenants to share the same computing and networking resources within a data center, which greatly reduces the physical footprint of these architectures. This, in turn, lowers the total cost of ownership as dedicated hardware is unnecessary. With Multi-Tenancy infrastructure, businesses can save money without sacrificing performance.
Within Azure SDN you have the ability to have multiple types of gateways even though above, I discuss the L3 GW the most. You could have multiple Gateway Pools with different types of gateways, for example, one pool dedicated to L3, or another to S2S, or you could have a mixed pool dedicated to Customer A if you really need this. All in all, though, they are multi-tenant GW pools with separation.
Apologies in advance for the length of this one but it is a heavy topic 🙂
GW Architecture Deployment types:
RAS Gateway for Software Defined Networking – Azure Stack HCI | Microsoft Learn [learn.microsoft.com]
VRF Lite configuration that is independent of the parent T0 GW
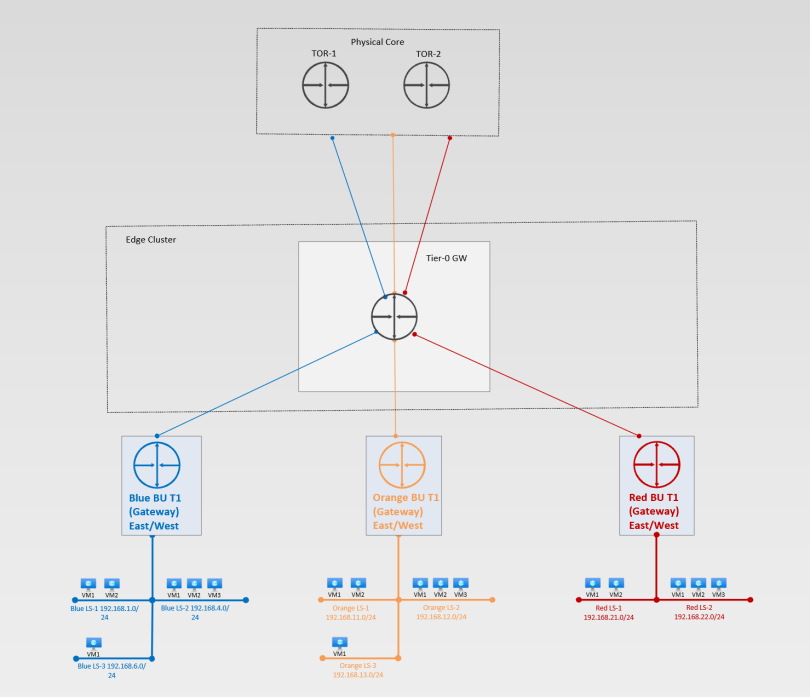
Tier-1 router becomes the first hop router and separates tenants via dedicated Tier-1 GW. This is where the tenants are separated. This is the preferred architecture when the desire is to have ease of management, resource overhead, and least complex design/
What is Multitenancy in a Software Defined Networking world?
In the above design, we would have a single vNET with a dedicated subnet per tenant. This would closely model the
- Tenant isolation at T1 GW level
- Can have up to 1k T1s GW per T0 GW
- Eliminates dependency from physical network when a new tenant is provisioned in NSX
- Does not require additional compute resources
In the above design, we would have a single vNET with a dedicated subnet per tenant. This would closely model the
- Allows for isolated logical networks at T0 GW level
- Allows for overlapping IP to be used in each dedicated T0 level without conflicts
- Enables CSP architecture
- Great design for merges and acquisitions
In the above design, we would have a single vNET with a dedicated subnet per tenant. This would closely model the
- Tenant isolation at subnet level
- Multiple scaling options depending on how you carve up the Virtual Network CIDR
- Eliminates dependency from physical network when a new /subnet tenant is provisioned in SDN
- Does not require additional compute resources
In the above design, we would have a single vNET with a dedicated subnet per tenant. This would closely model the
- Allows for isolated logical networks at Virtual Network level
- Allows for overlapping IP to be used in each dedicated Virtual Network level without conflicts
- Enables CSP architecture
- Great design for merges and acquisitions
- Does not require additional compute resources to create a new Virtual Network
As this journey continues, I figured it was time to address the scary ghost in the room, multitenancy. If I am being honest, this is where is pend the mass majority of my design hours. From these design decisions it has massive impacts on component design, for example, how many edges, how many T0/T1, how many L3 GWs, how many vNETs, etc. In this article, I will compare and contrast the different multitenant design options and impacts of VMware NSX and Azure Stack SDN.
Downsides:
Azure Stack SDN Virtual network per Tenant
At this point in time I have not discovered a downside to vNETs. They do not require additional compute resources or threaten bottle necks on NICs no matter how many you generate. They offer full Cloud Service Provider (CSP) capabilities onprem. Even though this series is based on Azure Stack HCI underneath, SDN also runs in windows 2025.
Downsides:
Additional design considerations:
Inside Azure Stack SDN you have the concept of a Virtual Network leveraging VXLAN for your encapsulation layer to isolate your networks. Inside the vNET is the concept of a Virtual Subnet, which enables you to segment the virtual network into one or more subnetworks and allocate a portion of the virtual network’s address space to each subnet.
Dedicated Tier-0 Gateways per Tenant
Downside
Each tenant is given their own dedicated Tier-0 GW allowing for full isolation from other overlay networks in the environment. This is how one would build out a Cloud Service Provider (CSP) architecture onprem leveraging NSX. This would effectively allow you to run the same CIDR ranges in each environment on top of the same shared hardware.
Benefits:
Layer 3 Forwarding Gateway:
Downsides: