When it comes to protecting your Linux system from unwanted network connections, having a good firewall is essential. While most Linux users rely on traditional firewalls like iptables, firewalls, or ufw, these usually work at the network level and don’t give detailed control over which applications can connect to the internet.
This is where OpenSnitch comes in, a GNU/Linux application firewall designed to give you control over your outgoing connections on a per-application basis.
In this article, we will explore what OpenSnitch is, how it helps secure your Linux machine, and guide you through simple installation and usage steps.
What is OpenSnitch?
OpenSnitch is an open-source application firewall for Linux, inspired by the popular Little Snitch on macOS. It monitors outgoing network connections and alerts you whenever a program tries to connect to the internet. You can then decide whether to allow or block the connection.
Why Use OpenSnitch?
- Manage outgoing network requests on an app-by-app basis.
- See which apps connect to which servers, IPs, and domains.
- Completely free, with code available on GitHub.
- Comes with a graphical interface for easy rule management.
- Blocks suspicious apps from sending data out without your knowledge.
Unlike traditional firewalls that focus on incoming traffic or broad rules, OpenSnitch focuses on outgoing connections and the apps generating them, making it ideal for users wanting better control over what leaves their system.
Installing OpenSnitch on Linux
OpenSnitch is officially available in package form for many Linux distributions like Ubuntu, Debian, Fedora, Arch Linux, and more.
First, head to the official GitHub release page to download the latest package files for your distribution:
- For Debian/Ubuntu →
.debfiles. - For Fedora/CentOS/RHEL →
.rpmfiles. - For Arch Linux → use
sudo pacman -S opensnitch.
OpenSnitch comes in two packages:
- The main firewall daemon (opensnitch).
- The optional graphical interface (python3-opensnitch-ui or opensnitch-ui).
Let’s break it down by distro:
Install OpenSnitch on Debian & Ubuntu
After downloading the .deb packages (both daemon and UI), open a terminal in your Downloads folder and run:
sudo apt install ./opensnitch*.deb ./python3-opensnitch-ui*.deb
Alternatively, you can just double-click the files to install them with your system’s software installer, which will install and set up both the firewall daemon and its GUI.
Install OpenSnitch on Fedora / CentOS / RHEL
If you downloaded the .rpm files, you have two options depending on your package manager (yum or dnf).
sudo yum localinstall opensnitch-*.rpm opensnitch-ui*.rpm OR sudo dnf install ./opensnitch-*.rpm ./opensnitch-ui*.rpm
After installation, start the firewall daemon and enable it to launch at boot.
sudo systemctl enable --now opensnitchd OR sudo systemctl enable --now opensnitch
To start the GUI, just type:
opensnitch-ui
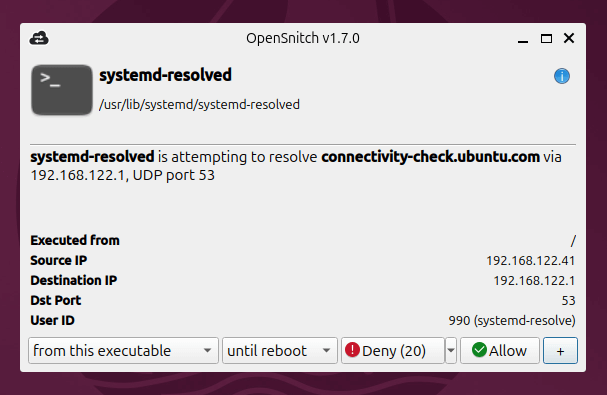
How OpenSnitch Works
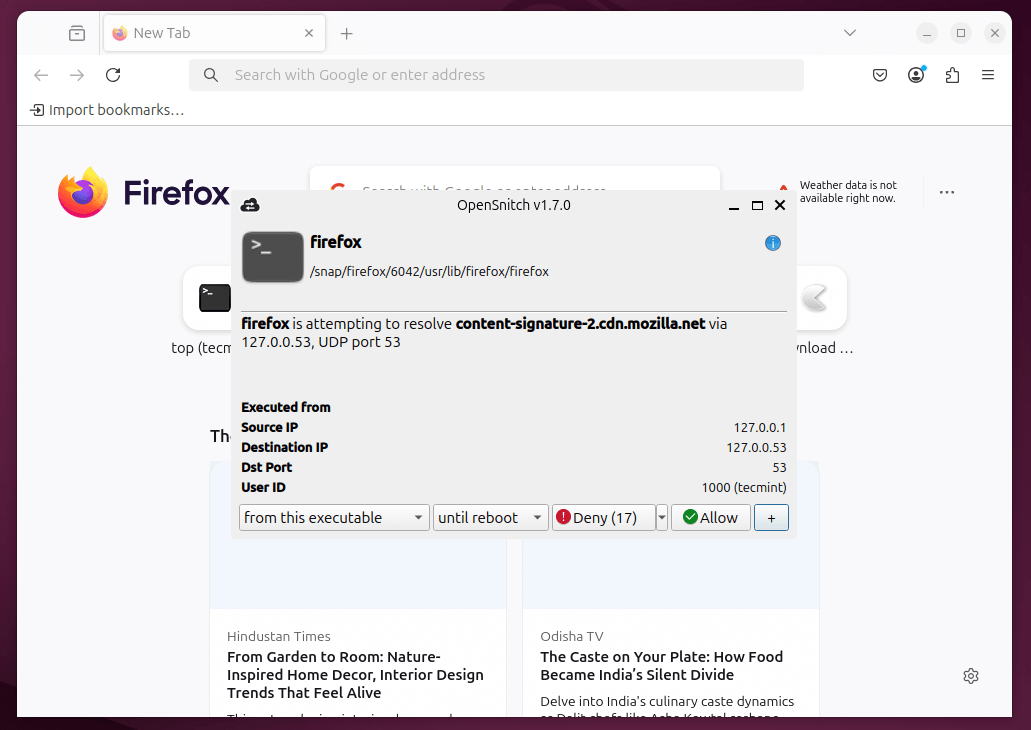
Once installed and running, OpenSnitch monitors every outgoing connection made by your applications. The first time a new app tries to access the internet, OpenSnitch will prompt you with a pop-up asking what to do.
You will see:
- The application name and its path.
- The IP address or domain it’s trying to connect to.
- The port being used.
Then you can choose to:
- Allow once
- Block once
- Always allow
- Always block
This makes it very easy to control network access based on both application and destination.
Example Use Case: Firefox
Suppose you open Firefox, and it tries to connect to the internet.
OpenSnitch will show a prompt like:
- App:
/usr/lib/firefox/firefox - Destination: 93.184.216.34 (example.com)
- Port: 443 (HTTPS)
You might choose “Always allow” so that Firefox can access the web without future prompts. If you were unsure about the app or destination, you could select “Block once” or “Always block” instead.
Managing Rules
Rules are created each time you approve or deny a connection.
You can manage them easily in the GUI:
- View existing rules.
- Edit or delete them.
- Organize by application or domain.
- Temporarily disable rules or the firewall entirely.
OpenSnitch stores these rules in plain text files, so you can even edit them manually if needed (usually found in /etc/opensnitch/rules/).
Conclusion
OpenSnitch is a powerful tool that brings a missing piece of security to Linux — the ability to control outgoing traffic at the application level. It’s open source, actively developed, and works across multiple Linux distributions with minimal setup.
With the latest package-based installation, getting started is easier than ever. Whether you’re a privacy advocate or just want to keep your system secure, OpenSnitch gives you the visibility and control you need.