Top 5 Linux Programs for Students in 2025
Linux is an open-source operating system whose use is increasing these days as a result of…
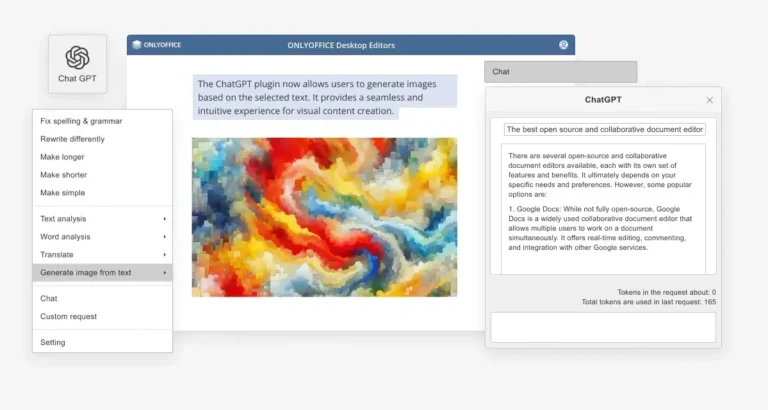
Linux is an open-source operating system whose use is increasing these days as a result of…
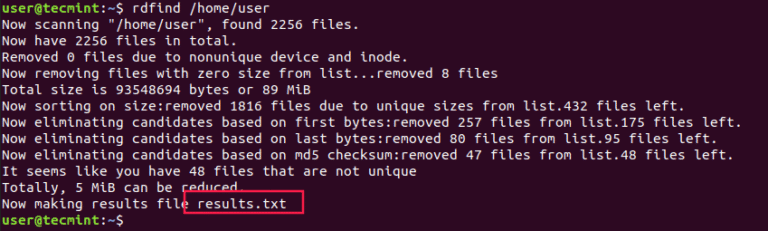
Organizing your home directory or even system can be particularly hard if you have the habit…
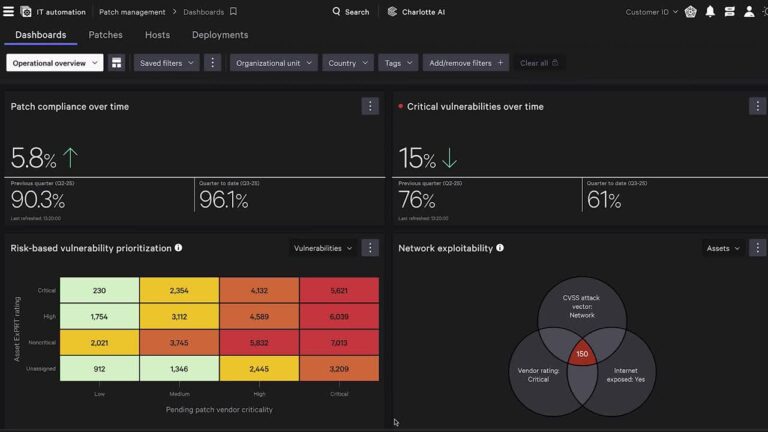
Traditional vulnerability management is broken. Security teams rely on one set of tools to find vulnerabilities;…

Want to play Windows games on your Linux system but not sure where to begin? Heard…
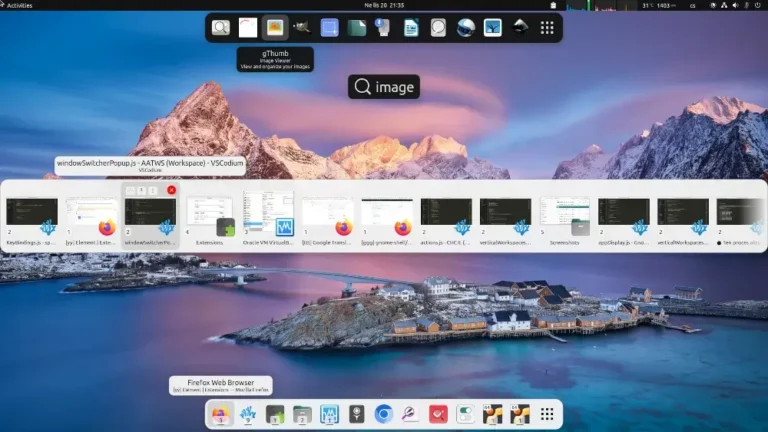
Do you feel like your Ubuntu desktop turns messy the moment you open more than a…
Publicly Disclosed Zero-Day Vulnerability in Windows SMB CVE-2025-55226 is a Critical remote code execution vulnerability affecting…
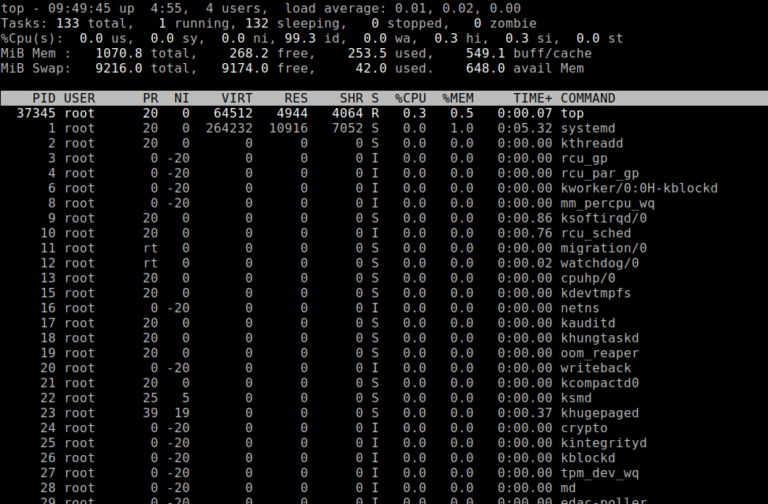
Being a System or Network administrator tasked with monitoring and debugging Linux system performance problems on…
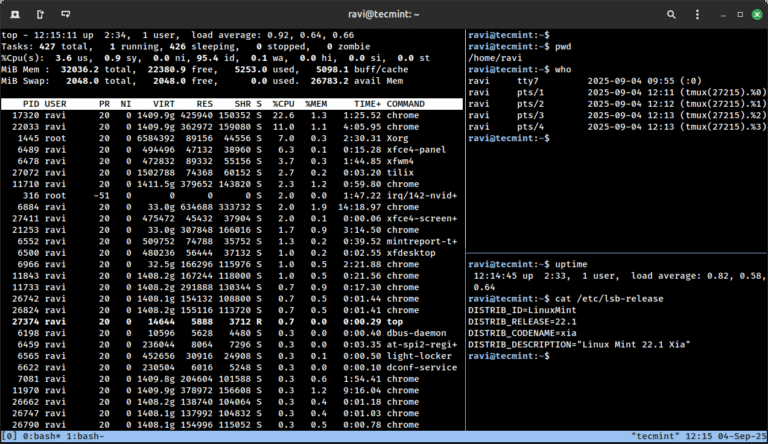
It is time once again to share a list of the best free and open-source software…
As someone who has been using Linux for more than 12 years, I’ve often come across…
To solve this problem, the feature calculation code was updated to use the most recent version…
Core Technology that Powers Security for AI Data remains the primary target for adversaries, but traditional…

Zip is a command-line utility tool used for compressing files and folders. Compression of files &…
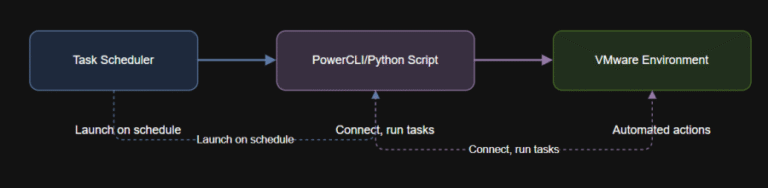
Learning Objectives By the end of this article, you will: Schedule PowerCLI and Python scripts for…
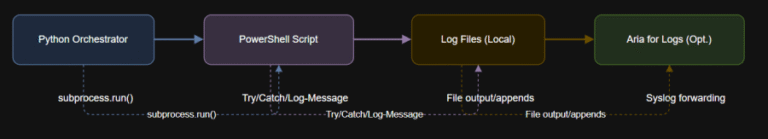
Learning Objectives Below is a PowerShell script that wraps key actions in error handling and logs…
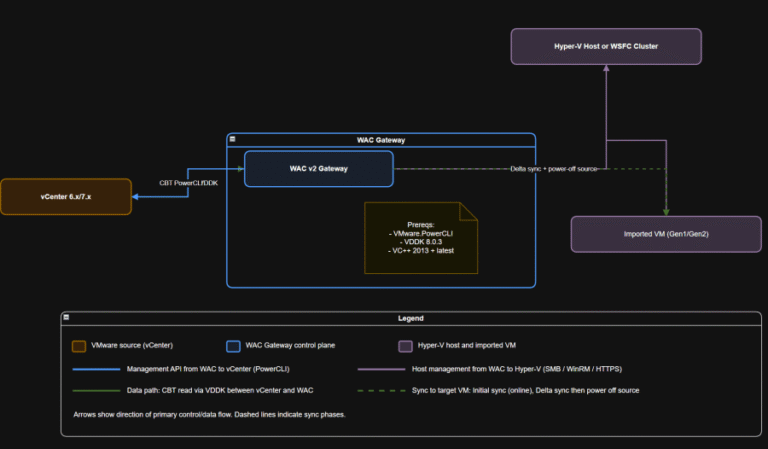
Compliance checkpoints (examples) Why this matters Bridge strategy: If you are standardizing on Windows Server and…