VCF 9.0 GA Mental Model Part 6: Topology and Identity Boundaries for Single Site, Dual Site, and Multi-Region
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
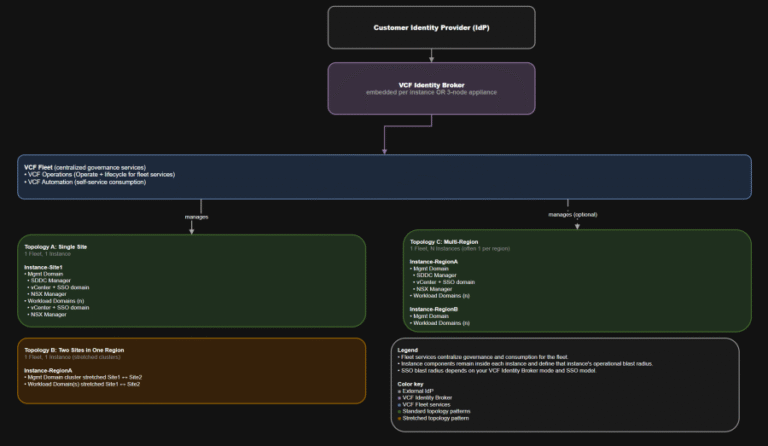
TL;DR Identity is not a “later” decision. It is a boundary decision. The hierarchy you should…
TL;DR This post targets VCF 9.0 GA only: VCF 9.0 (17 JUN 2025) build 24755599, with…
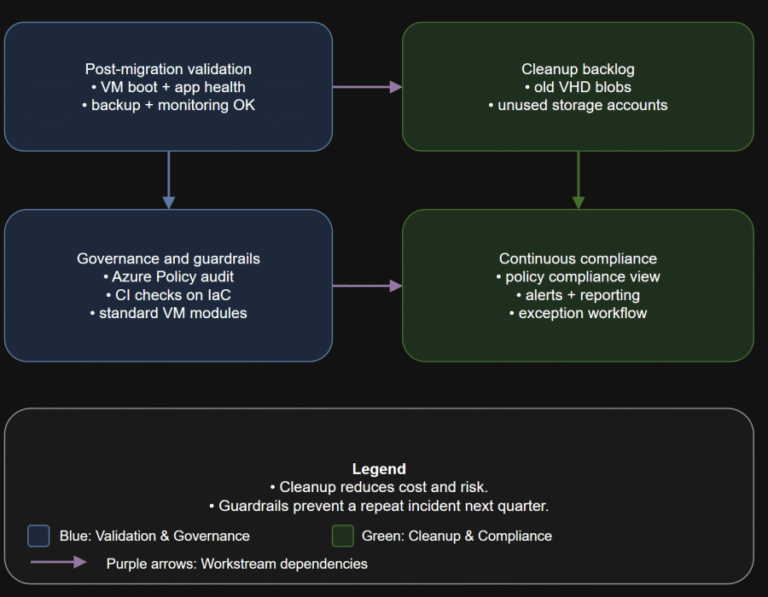
TL;DR Converting disks is not the finish line. Your real goal is a new steady state:…
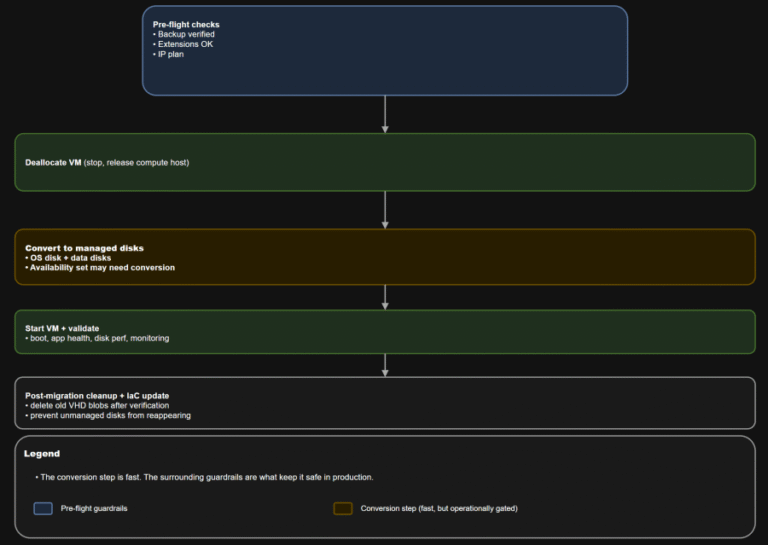
TL;DR Converting a VM to managed disks is usually operationally straightforward: deallocate, convert, start, validate. The…
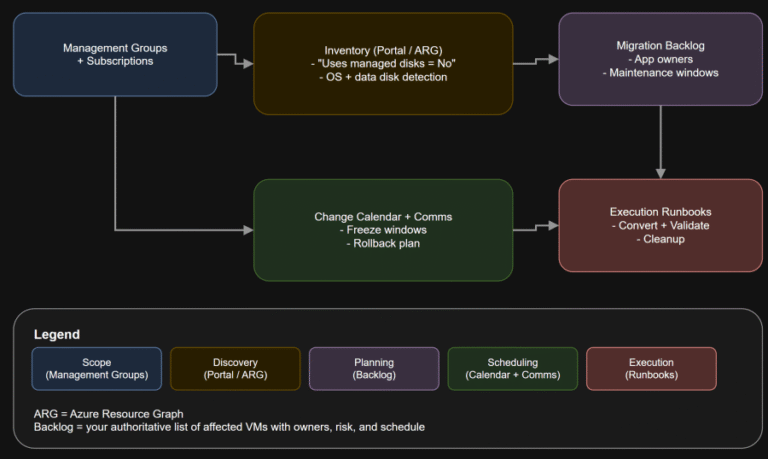
TL;DR If any Azure IaaS VM in your estate still uses unmanaged disks, it is on…
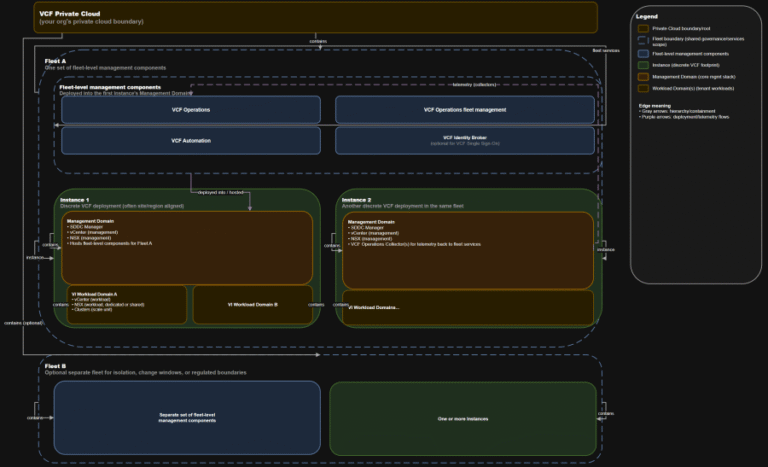
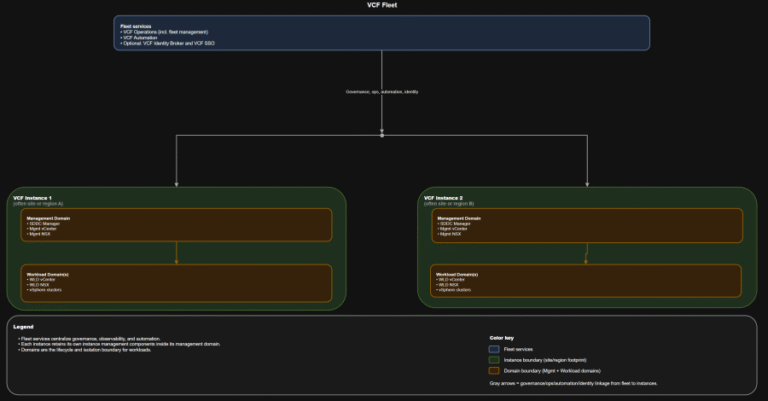
TL;DR A) One fleet, one instance, stretched where justified In VCF 9.0, identity is not a…
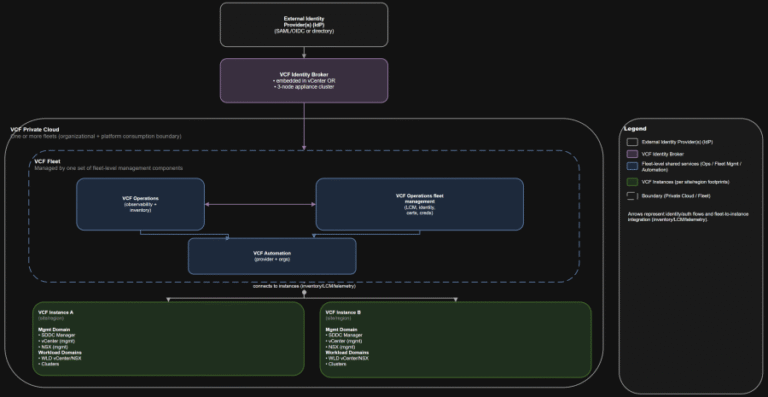
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…
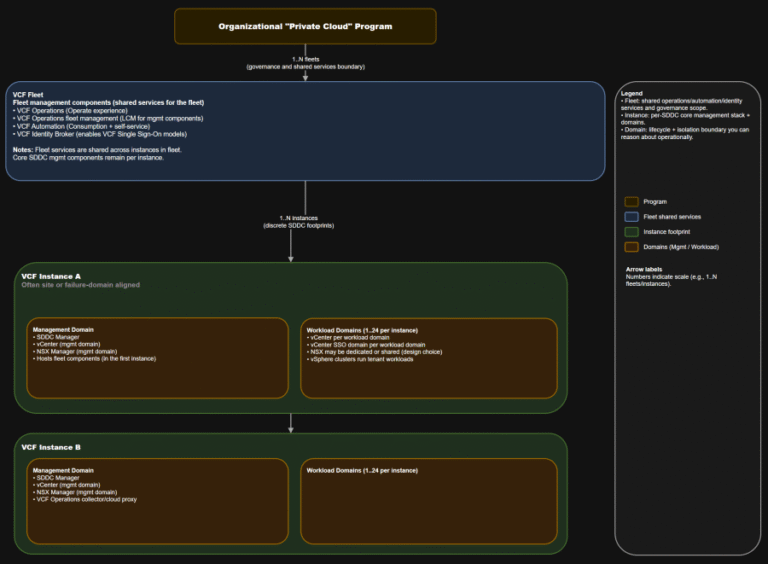
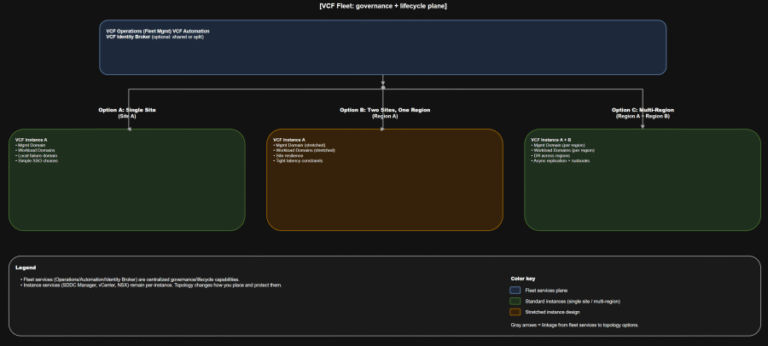
TL;DR This is the “where do we do the thing” map you want in every runbook….
Actively Exploited Zero-Day Vulnerability in Windows Remote Desktop The vulnerability allows local attackers with no privileges…

SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…
In this article, you will discover the best software tools powered by AI that you can…
GOLDEN CHOLLIMA Shared infrastructure elements and tool cross-pollination indicate these units maintain close coordination. All three…
In this guide, we feature some of the best Linux distributions that you can install on…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…