VCF 9.0 GA Mental Model Part 6: Topology and Identity Boundaries for Single Site, Dual Site, and Multi-Region
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
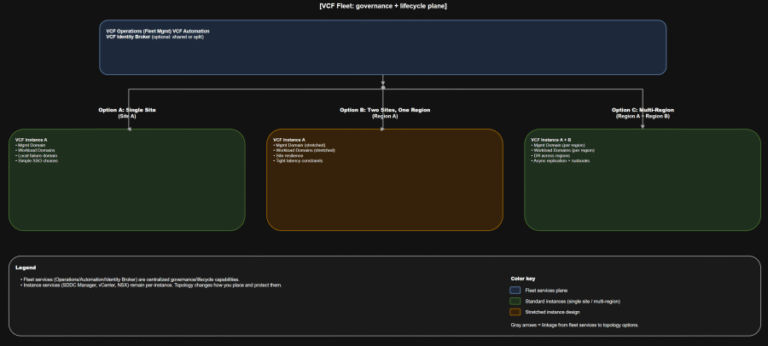
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
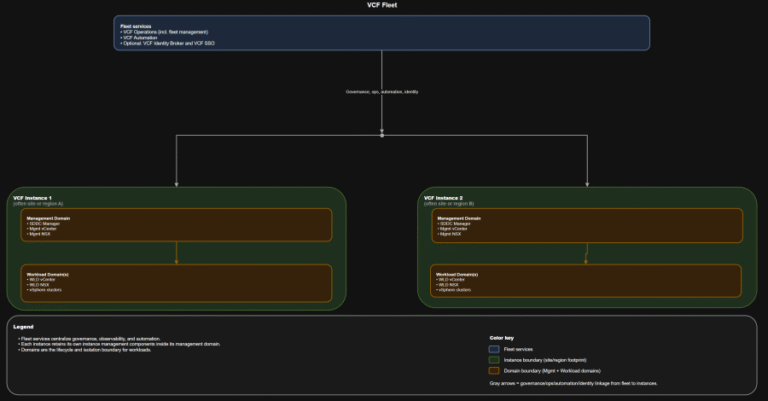
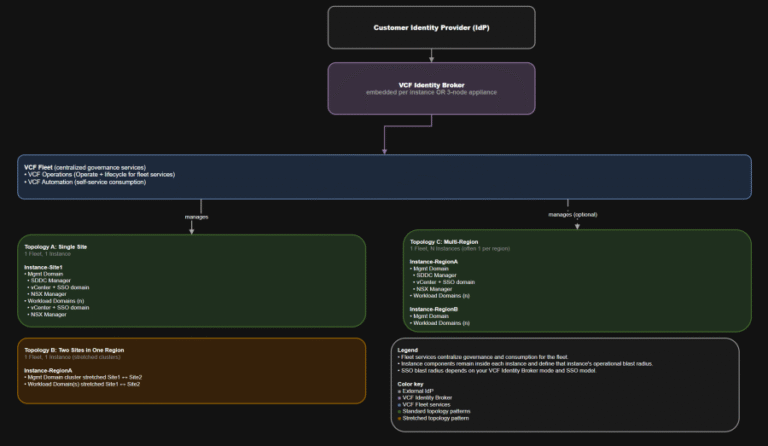
TL;DR Identity is not a “later” decision. It is a boundary decision. The hierarchy you should…
TL;DR This post targets VCF 9.0 GA only: VCF 9.0 (17 JUN 2025) build 24755599, with…
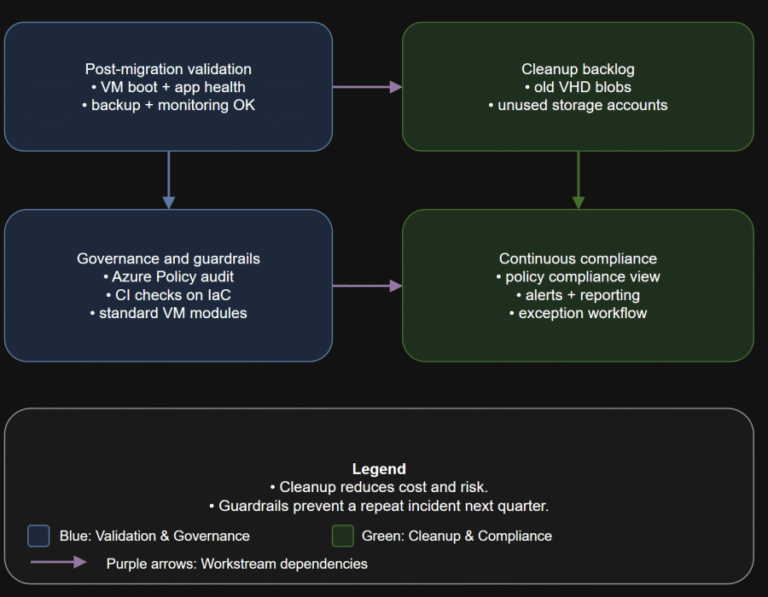
TL;DR Converting disks is not the finish line. Your real goal is a new steady state:…
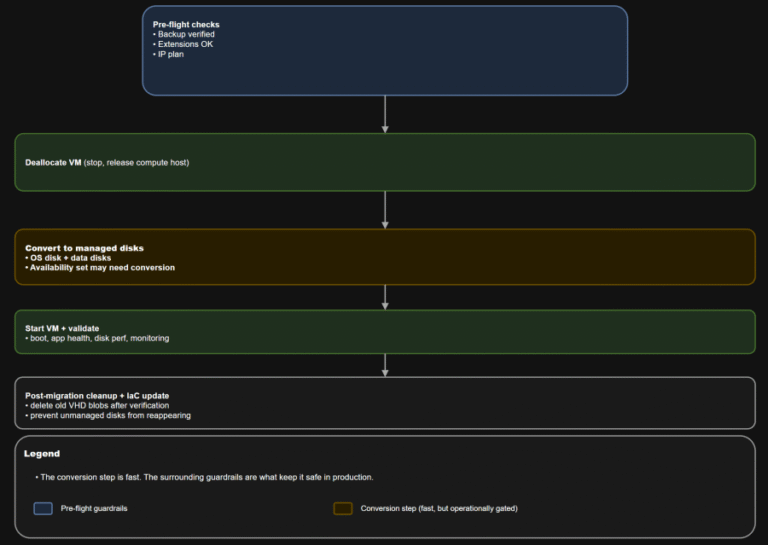
TL;DR Converting a VM to managed disks is usually operationally straightforward: deallocate, convert, start, validate. The…
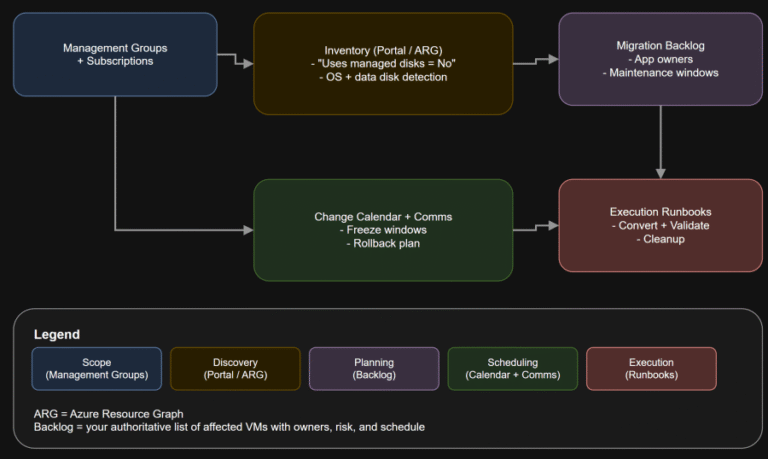
TL;DR If any Azure IaaS VM in your estate still uses unmanaged disks, it is on…
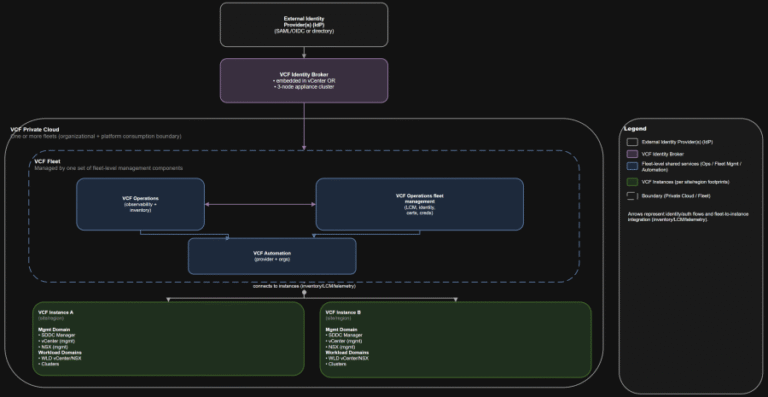
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…
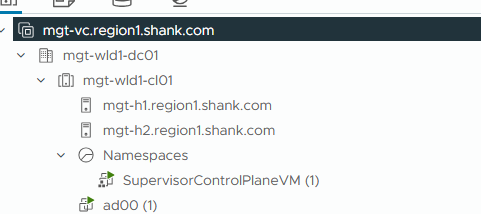
November 7, 2025 vCenter Supervisor Management is Blank Enabling / Disabling Supervisor Management Errors The Issue?…
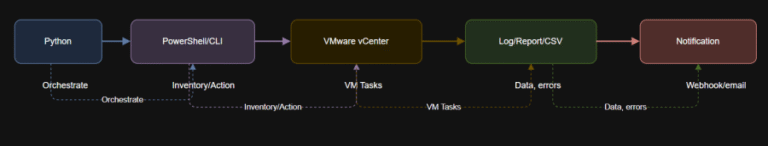
Learning Objectives VMware Repository on GitHub See how a single Python script can orchestrate inventory, lifecycle,…
Learning Objectives $message = @{text = “VM $vmName has been powered off via automation.”} | ConvertTo-Json…
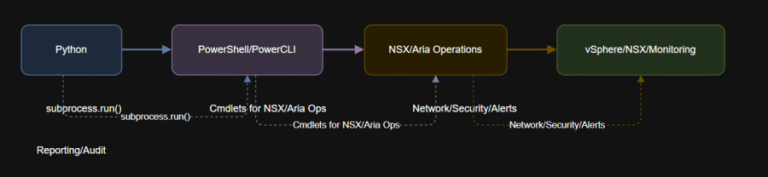
Learning Objectives $vmName = “<your-vm-name>”$outputFile = “C:Tempsnap_status.txt”if status == “FAILED”:url = “https://<your-jira-server>/rest/api/2/issue/”auth = (‘<jira-username>’, ‘<jira-api-token>’)headers =…
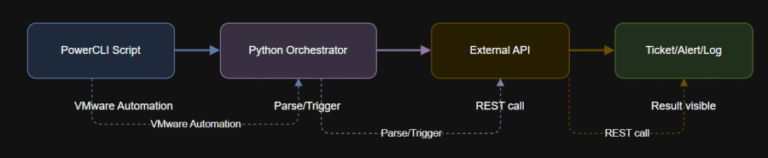
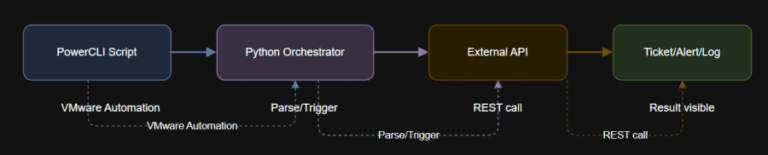
Learning Objectives Next up: In Article 9, you will learn to integrate PowerCLI with external APIs…
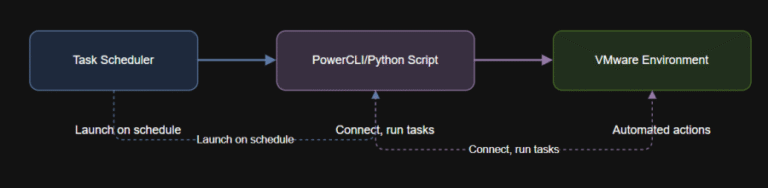
Learning Objectives By the end of this article, you will: Schedule PowerCLI and Python scripts for…
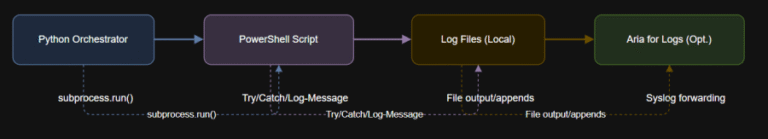
Learning Objectives Below is a PowerShell script that wraps key actions in error handling and logs…
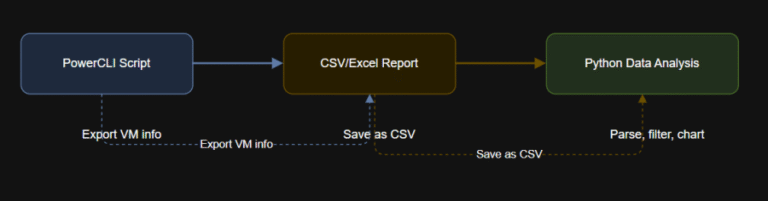
Learning Objectives # Print the first few rowsprint(df.head()) Automate export of VMware inventory and reports to…