How Agentic Tool Chain Attacks Threaten AI Agent Security
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…
There are so many benefits of using a VPN (Virtual Private Network), some of which include…
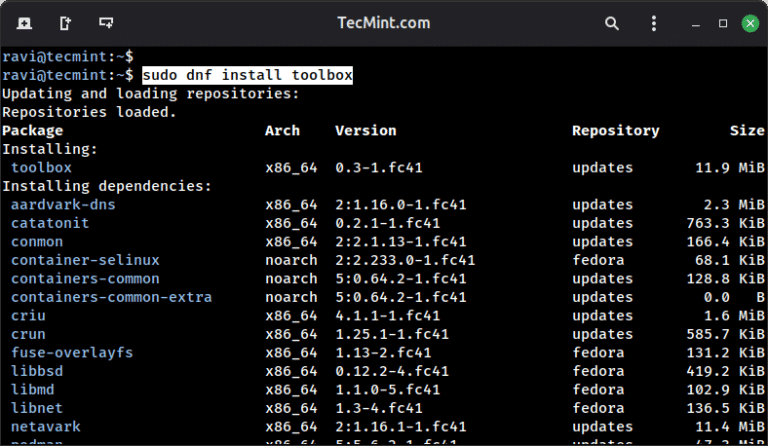
Modern Linux development has moved beyond the traditional approach of installing everything directly on your system….
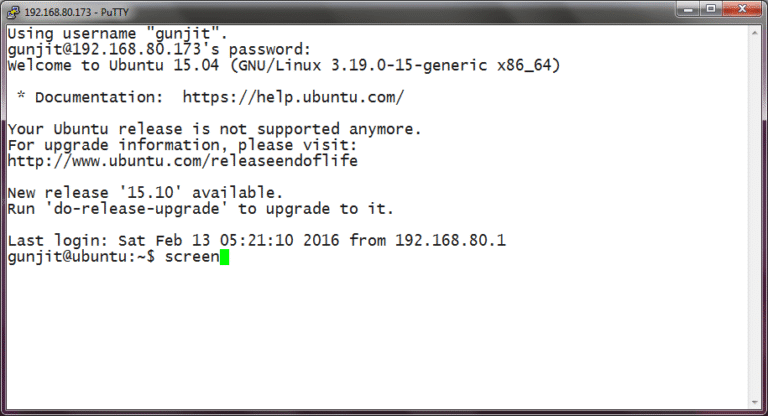
SSH or Secure Shell in simple terms is a way by which a person can remotely…
WARP PANDA demonstrates a high level of stealth and almost certainly focuses on maintaining persistent, long-term,…
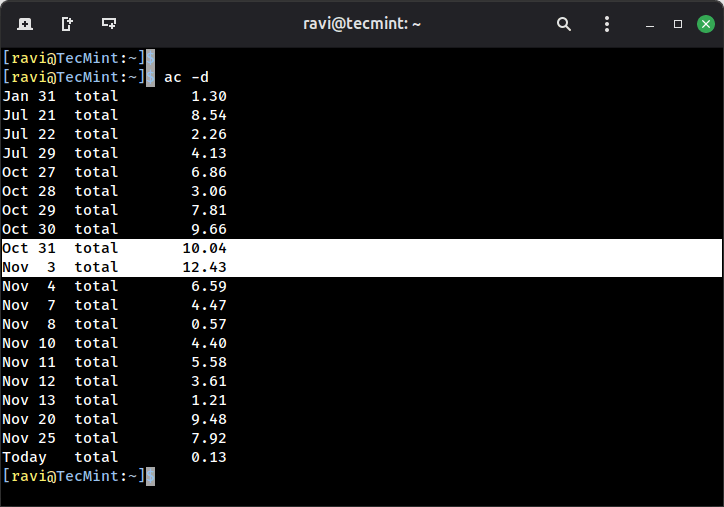
When you’re managing a Linux server, especially one with multiple users, you need visibility into what’s…
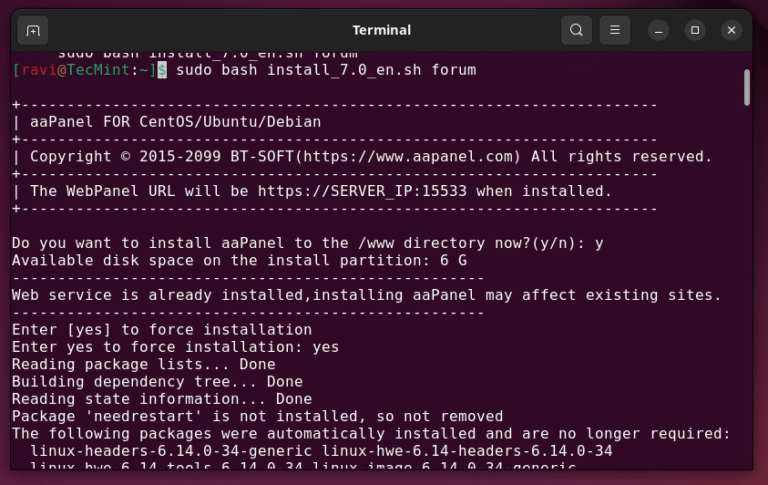
Managing a web server through command-line alone can feel like you’re juggling too many things at…
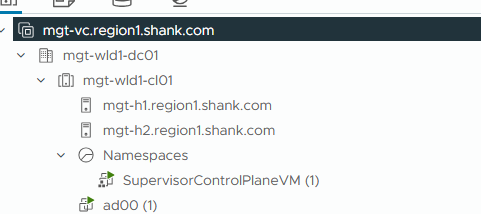
November 7, 2025 vCenter Supervisor Management is Blank Enabling / Disabling Supervisor Management Errors The Issue?…
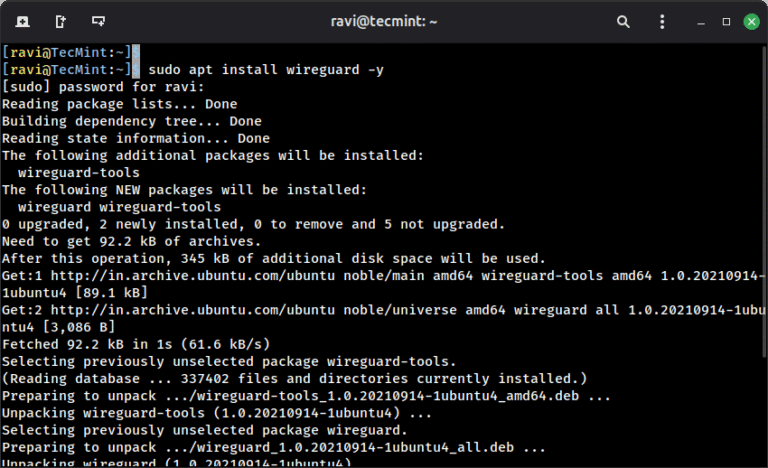
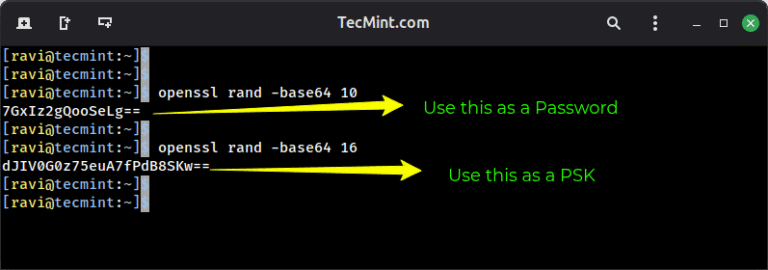
When you connect to a coffee shop’s WiFi or access the internet from any public network,…
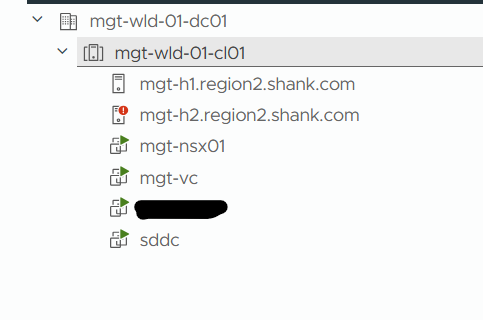
October 13, 2025 VCF 9 Fleet Deployment Task Fails The Issue? As with any failed deployment,…

SSH (Secure Shell) is one of the most important tools for Linux system administrators and developers,…

Keeping files in sync across multiple machines is a common task for Linux users. You might…
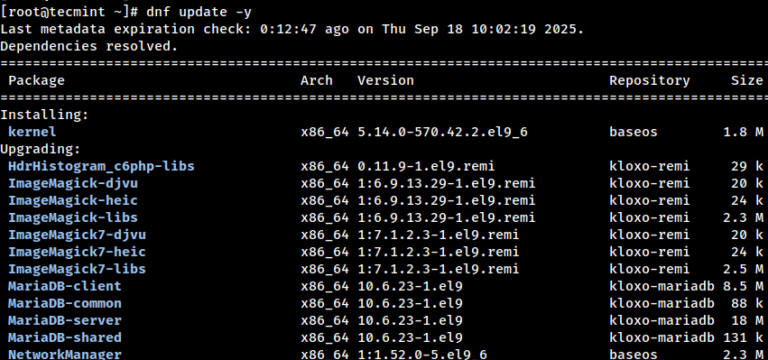
If you’ve ever managed a hosting server, you know that cPanel & WHM is one of…
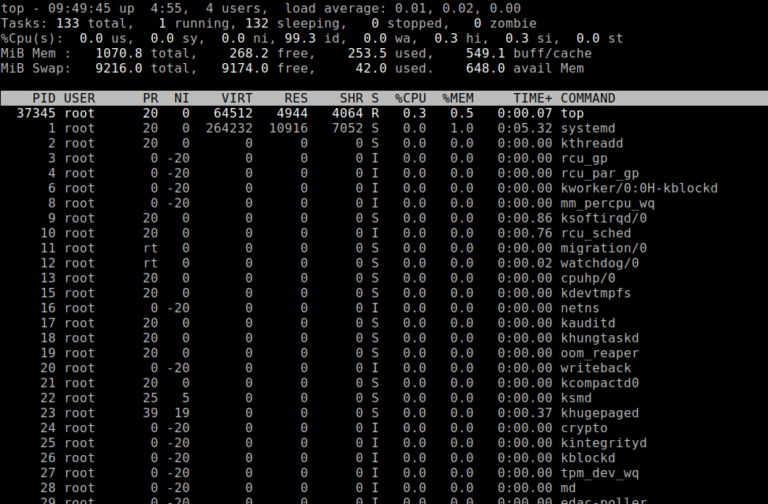
Being a System or Network administrator tasked with monitoring and debugging Linux system performance problems on…