CrowdStrike Named the Leader in 2025 Frost Radar for SaaS Security Posture Management
Frost & Sullivan also praised how CrowdStrike both secures AI agents and leverages agentic AI for…
Frost & Sullivan also praised how CrowdStrike both secures AI agents and leverages agentic AI for…
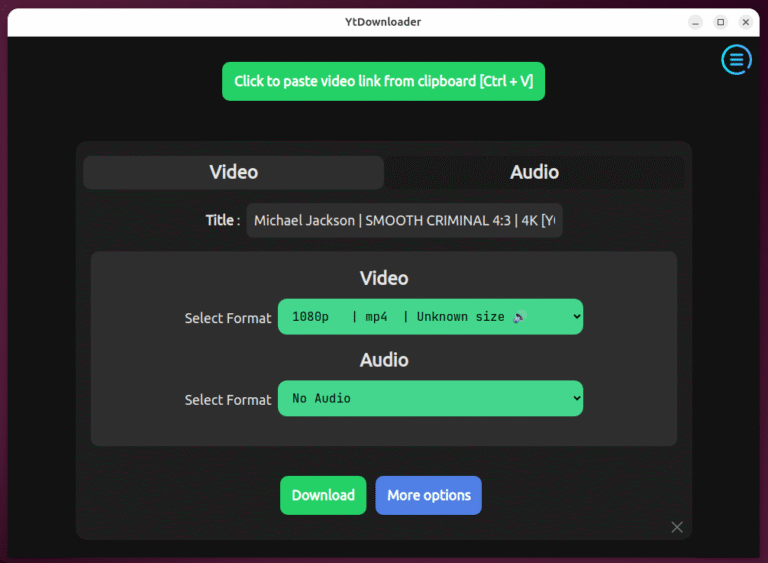
Earlier, I wrote about yt-dlp, the powerful command-line tool for downloading videos from hundreds of websites,…
We believe our placement as a Visionary, coupled with our groundbreaking AI innovations and the acquisition…
In our previous articles, we’ve covered MySQL interview questions for beginners and intermediate users, and the…
Charlotte AI is powered by a fully managed multi-agent architecture that orchestrates specialized agents across a…
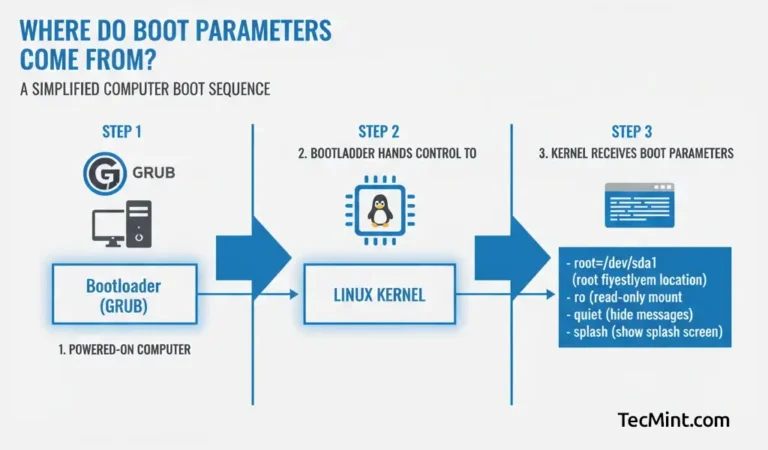
Linux booting is a complex process compared to other operating systems. The Linux Kernel accepts many…
The fundamental shift we’re seeing is moving security professionals from operators to orchestrators. Today, we have…
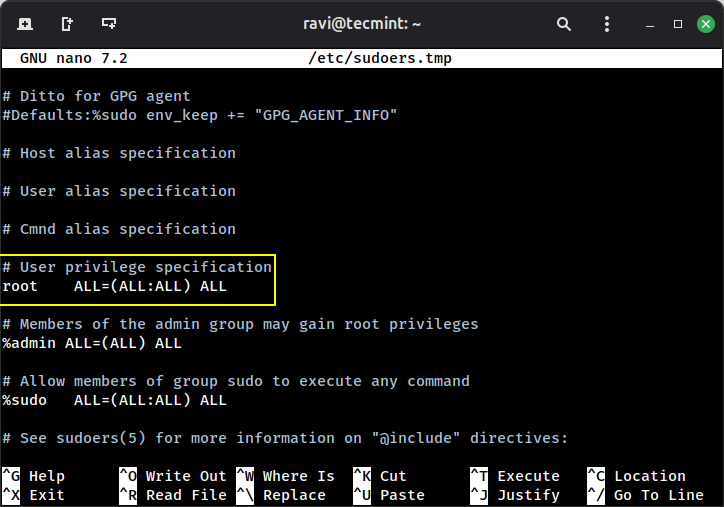
Linux is generally more secure than many other operating systems. A key part of this security…
As enterprises adopt AI agents and embed them into SaaS workflows, visibility and governance become essential….
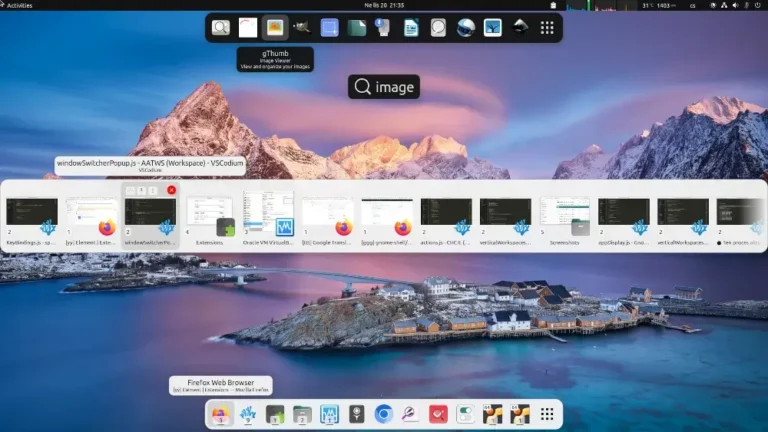
Do you feel like your Ubuntu desktop turns messy the moment you open more than a…
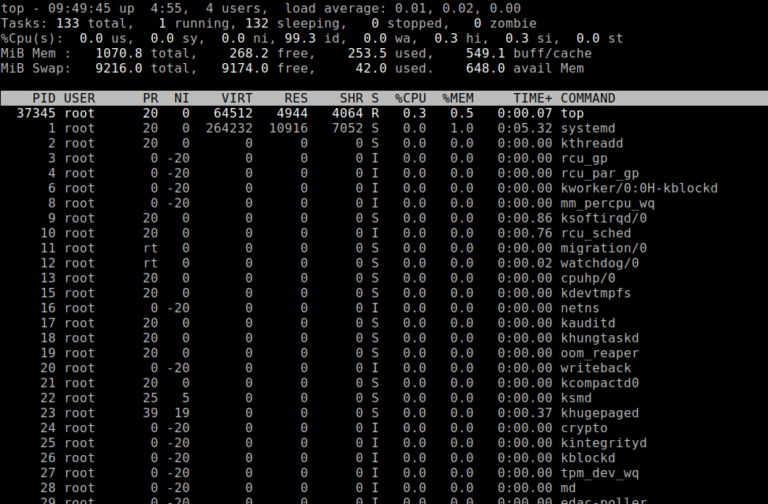
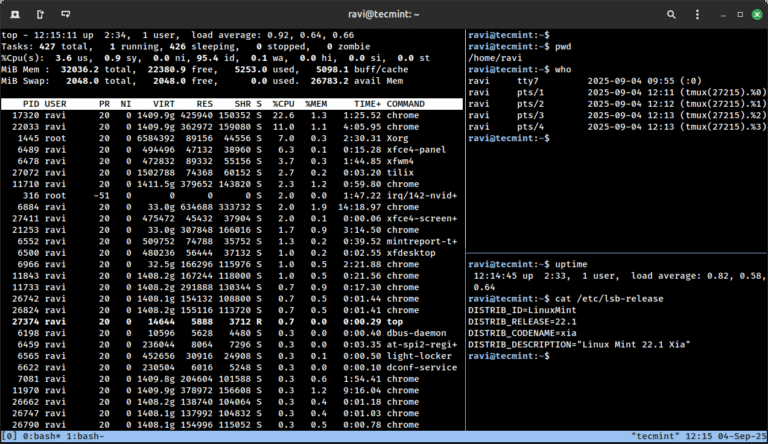
Being a System or Network administrator tasked with monitoring and debugging Linux system performance problems on…
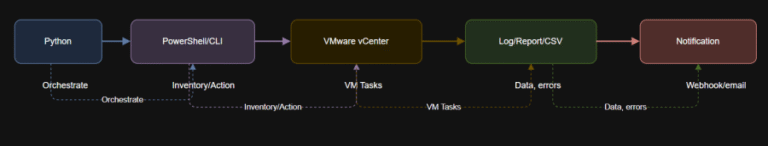
Learning Objectives VMware Repository on GitHub See how a single Python script can orchestrate inventory, lifecycle,…
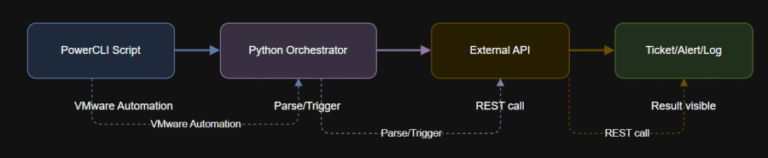
Learning Objectives $message = @{text = “VM $vmName has been powered off via automation.”} | ConvertTo-Json…
It is time once again to share a list of the best free and open-source software…
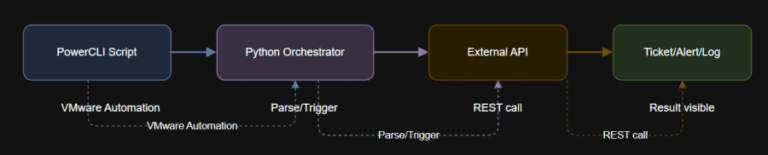
Learning Objectives $vmName = “<your-vm-name>”$outputFile = “C:Tempsnap_status.txt”if status == “FAILED”:url = “https://<your-jira-server>/rest/api/2/issue/”auth = (‘<jira-username>’, ‘<jira-api-token>’)headers =…