16 Lightweight Linux Distributions for Older Machines in 2026
In this guide, we feature some of the best Linux distributions that you can install on…
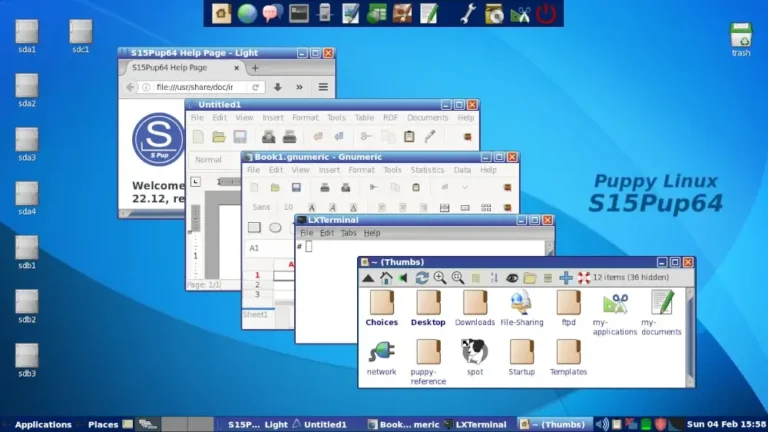
In this guide, we feature some of the best Linux distributions that you can install on…
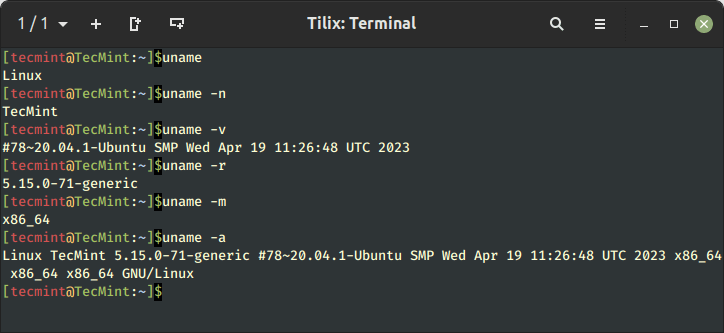
Learn 11 essential Linux commands to check hardware info including CPU, RAM, disk, USB, and PCI…
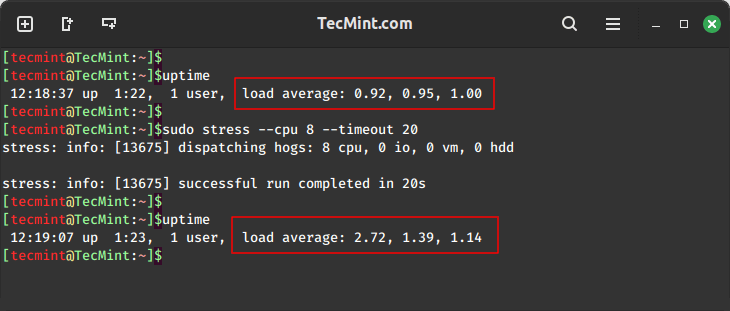
In this guide, we will explore two important tools, stress and stress-ng, for conducting comprehensive stress…
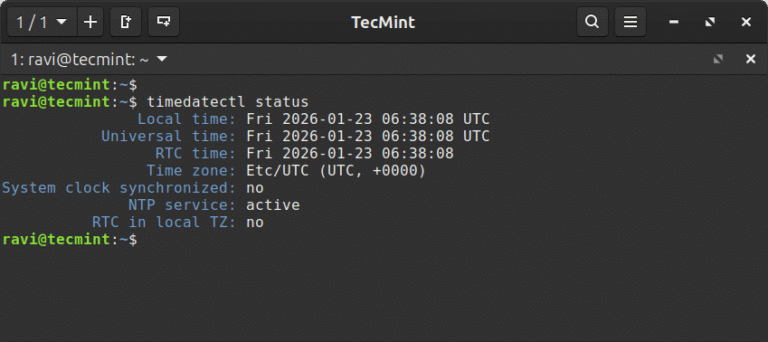
In this article, learn how to set time, timezone, and synchronize your Linux system clock with…

In this article, we show you how to encrypt files with GPG in Linux, generate key…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
ARM (Advanced RISC Machine) is a RISC (Reduced Instruction Set Computing) instruction-set architecture developed by ARM…
Updated: This article has been refreshed to cover the latest ways to edit documents on Ubuntu…

As the name implies, the 5C model focuses around 5 key “C’s.” Each C represents a…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…
Actively Exploited Zero-Day Vulnerability in Windows Desktop Window Manager CVE-2026-20955 and CVE-2026-20957 are Critical remote code…
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
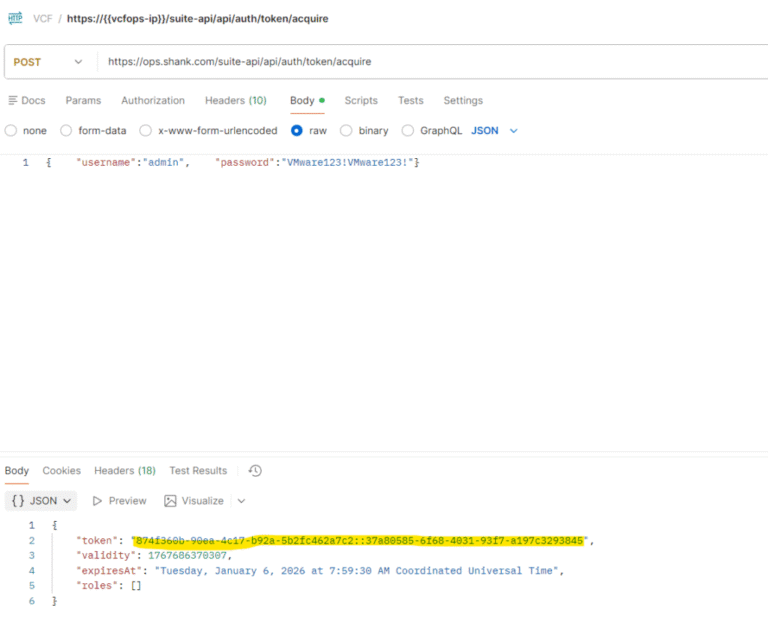
January 7, 2026 Authentication Failure: VCF SSO Broken vCenter vIDB Service Unavailable The Issue? It is…
With the cluster infrastructure in place through the Vertex Training Cluster, we configured Slurm, the industry-standard…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…