50+ Best Free and Open-Source Software for Linux in 2025
It is time once again to share a list of the best free and open-source software…
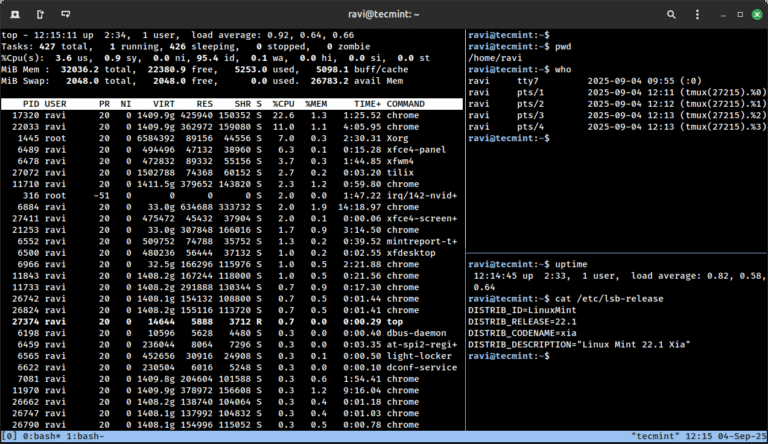
It is time once again to share a list of the best free and open-source software…
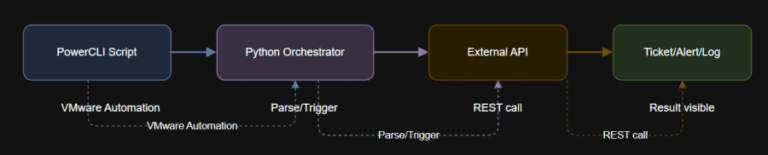
Learning Objectives $vmName = “<your-vm-name>”$outputFile = “C:Tempsnap_status.txt”if status == “FAILED”:url = “https://<your-jira-server>/rest/api/2/issue/”auth = (‘<jira-username>’, ‘<jira-api-token>’)headers =…
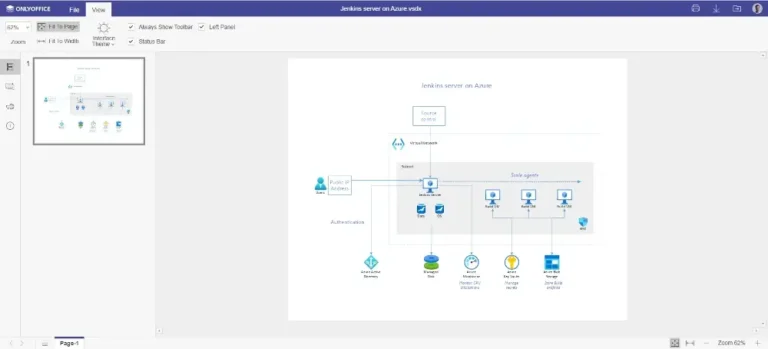
Since diagrams such as networks, organizational structures, system architectures, workflows, etc., have become an indispensable part…
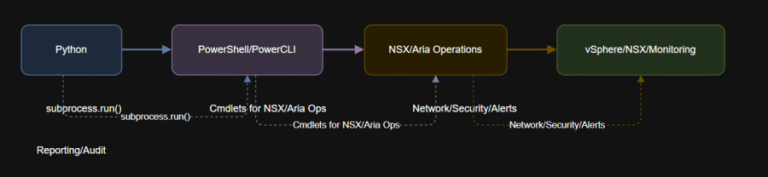
Learning Objectives Next up: In Article 9, you will learn to integrate PowerCLI with external APIs…
Core Technology that Powers Security for AI Data remains the primary target for adversaries, but traditional…
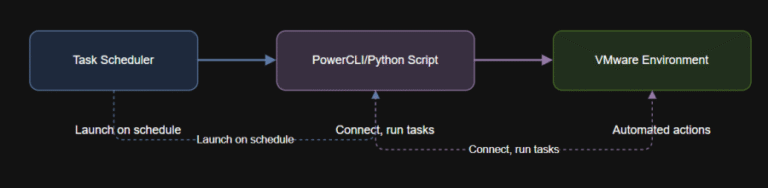
Learning Objectives By the end of this article, you will: Schedule PowerCLI and Python scripts for…
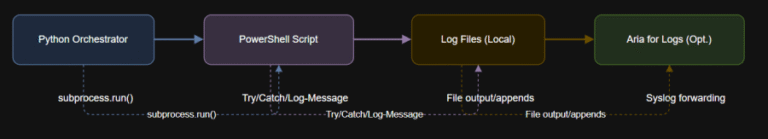
Learning Objectives Below is a PowerShell script that wraps key actions in error handling and logs…
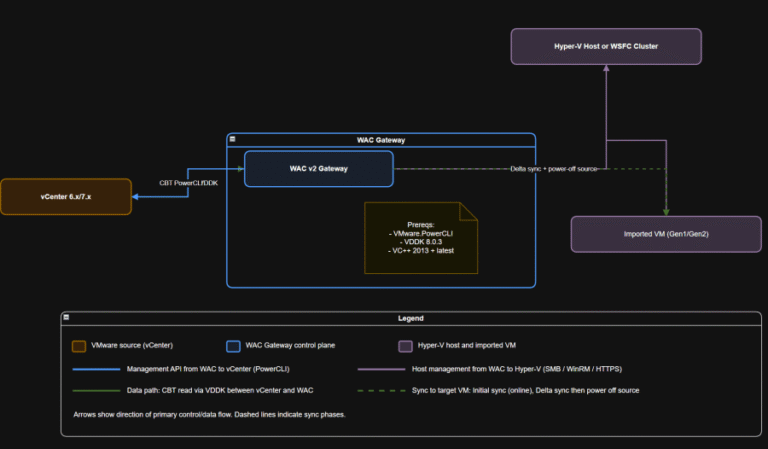
Compliance checkpoints (examples) Why this matters Bridge strategy: If you are standardizing on Windows Server and…
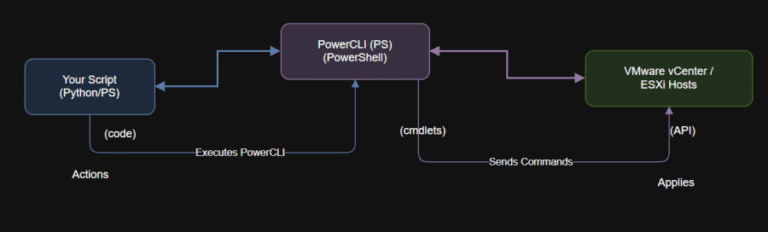
Set-PowerCLIConfiguration -InvalidCertificateAction Ignore -Scope Session VMware Repository on GitHub Step 1: Install PowerShellWindows 10/11 comes with…
A Leader in Exposure Management The report notes, “Network-based vulnerability scanning was recently added to the…
Since late 2024, CrowdStrike Counter Adversary Operations has observed significant activity conducted by MURKY PANDA, a…
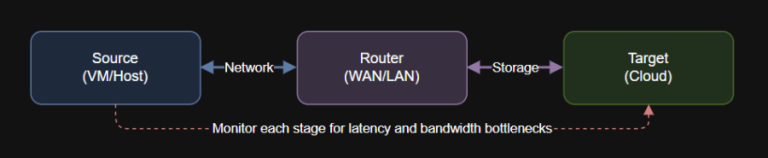
Introduction Data movement in cloud and hybrid architectures is only as fast as your slowest link….

Introduction A global retailer must store EU customer data within European borders to comply with GDPR….
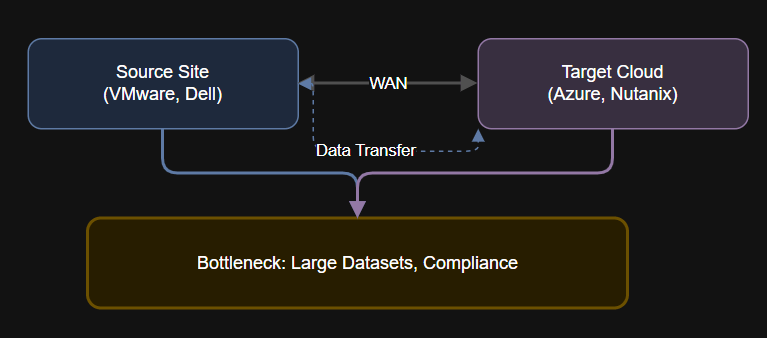
Introduction Even the best-planned cloud and hybrid migrations can be derailed by data gravity. When large…
Publicly Disclosed Zero-Day Vulnerability in Windows Kerberos As we have learned with other notable vulnerabilities, such…