CrowdStrike 2026 Global Threat Report: The Evasive Adversary Wields AI
To defend themselves, security leaders need clarity on which adversaries to watch, the details of their…
To defend themselves, security leaders need clarity on which adversaries to watch, the details of their…
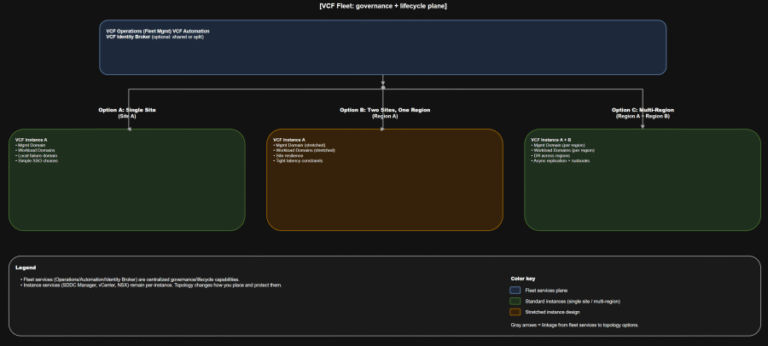
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
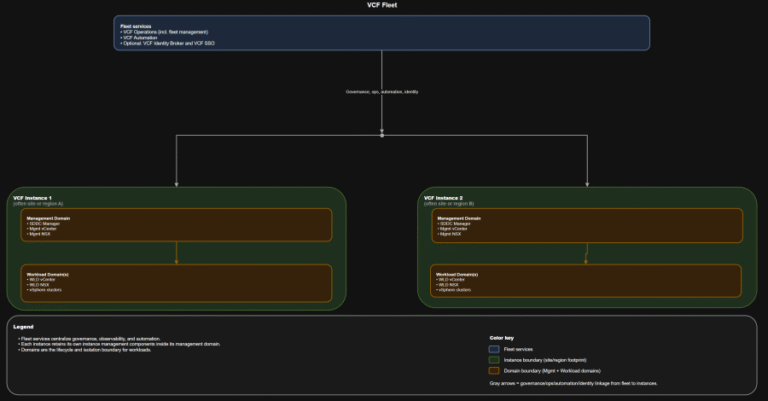
TL;DR Identity is not a “later” decision. It is a boundary decision. The hierarchy you should…
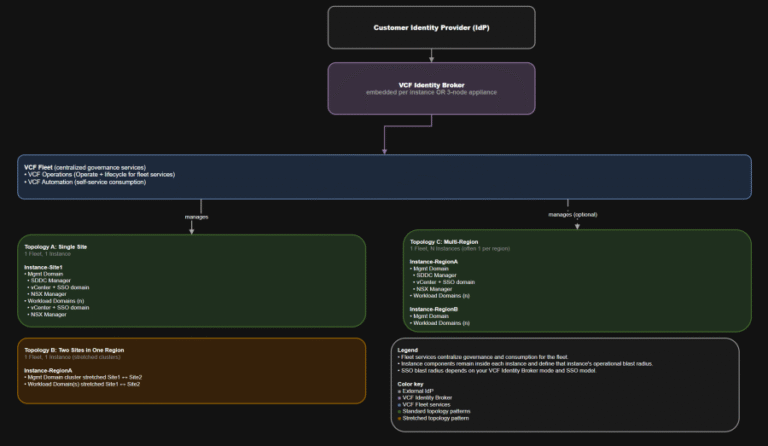
TL;DR This post targets VCF 9.0 GA only: VCF 9.0 (17 JUN 2025) build 24755599, with…
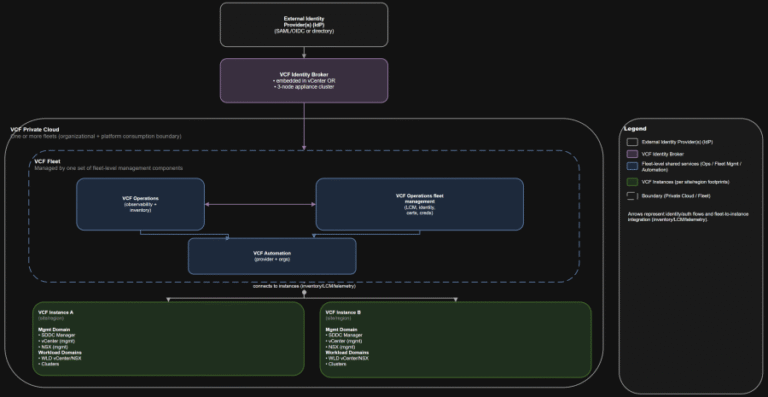
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…

In this article, you will learn how to list, configure, enable, disable, and troubleshoot network interfaces…
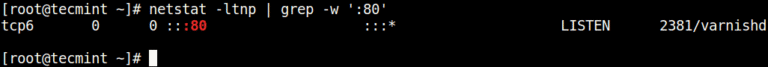
In this article, you will learn how to find which process or service is listening on…
Actively Exploited Zero-Day Vulnerability in Windows Remote Desktop The vulnerability allows local attackers with no privileges…

– System Engineer, IT Services “Overall, it’s been a valuable and eye-opening experience. The tool has helped…
Indirect prompt injection significantly amplifies this risk by allowing adversaries to influence OpenClaw’s behavior through data…

SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…
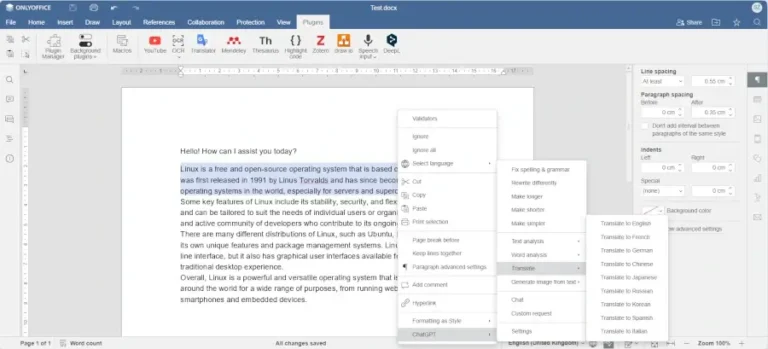
In this article, you will discover the best software tools powered by AI that you can…
As AI adoption accelerated, WEX® — a global commerce platform that supports business operations primarily for…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
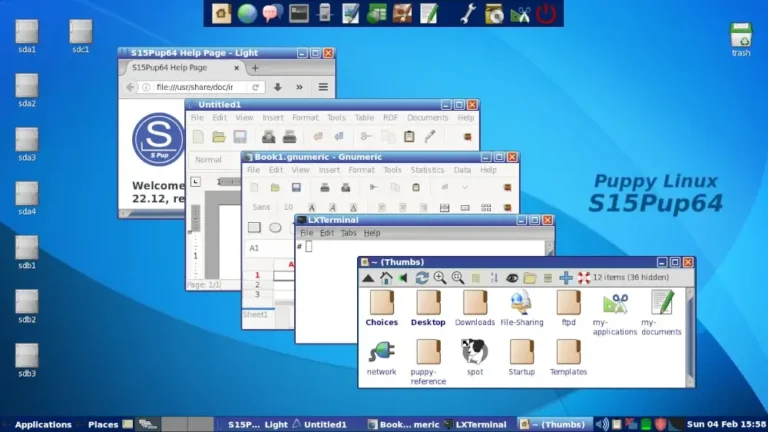
In this guide, we feature some of the best Linux distributions that you can install on…