CrowdStrike 2026 Global Threat Report: The Evasive Adversary Wields AI
To defend themselves, security leaders need clarity on which adversaries to watch, the details of their…
To defend themselves, security leaders need clarity on which adversaries to watch, the details of their…
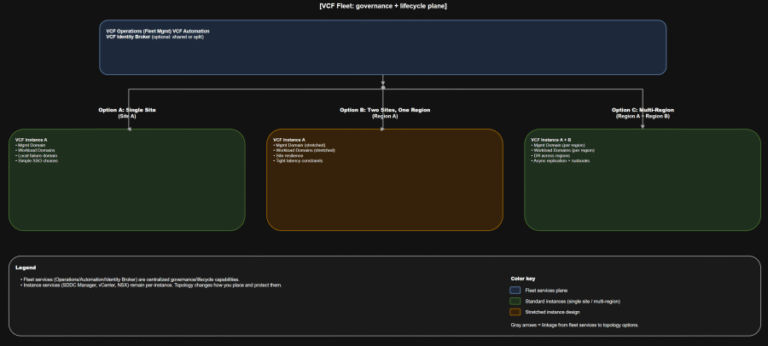
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
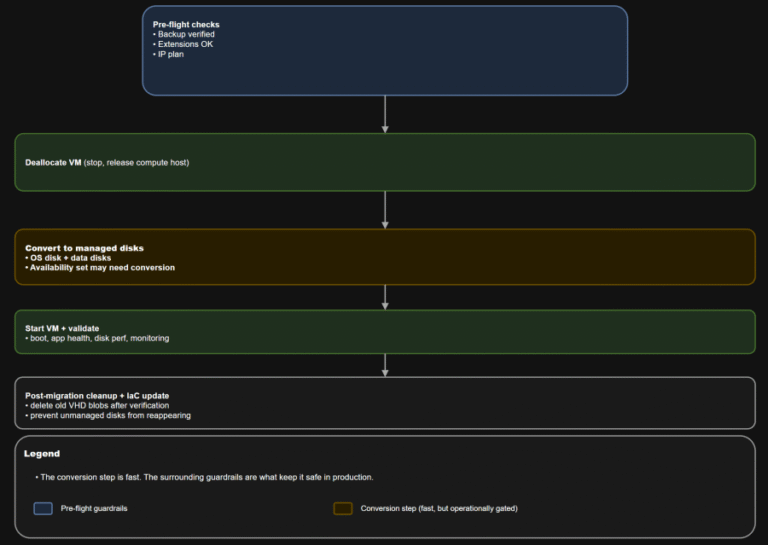
TL;DR Converting a VM to managed disks is usually operationally straightforward: deallocate, convert, start, validate. The…
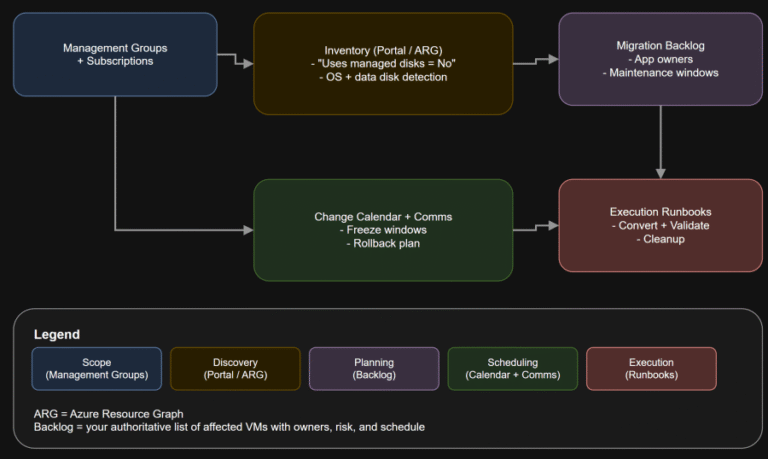
TL;DR If any Azure IaaS VM in your estate still uses unmanaged disks, it is on…
Insider threats pose a growing risk to organizations. Whether insiders take malicious actions, exhibit negligent behavior,…

In this article, you will learn how to list, configure, enable, disable, and troubleshoot network interfaces…
CrowdStrike Falcon Identity Protection — A Great Tool to Gain Visibility We remain committed to innovating…

– System Engineer, IT Services “Overall, it’s been a valuable and eye-opening experience. The tool has helped…
Indirect prompt injection significantly amplifies this risk by allowing adversaries to influence OpenClaw’s behavior through data…
As AI adoption accelerated, WEX® — a global commerce platform that supports business operations primarily for…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
Christoph Bausewein is Assistant General Counsel for Data Protection and Policy at CrowdStrike.This creates a new…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
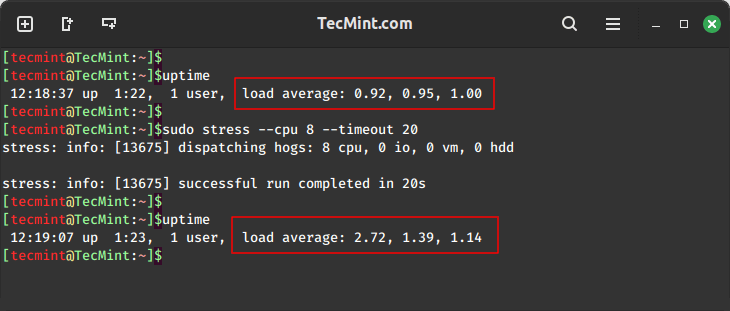
In this guide, we will explore two important tools, stress and stress-ng, for conducting comprehensive stress…
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…