CrowdStrike Falcon Scores Perfect 100% in SE Labs’ Most Challenging Ransomware Test
SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…

SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
Under the Hood: How It Works Step 3: Dynamic behavioral analysis Step 5: Similar sample identification…
With the cluster infrastructure in place through the Vertex Training Cluster, we configured Slurm, the industry-standard…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
Unsupported operating systems have historically become adversary targets. The longer a system remains unsupported, the more…

Unauthorized use of RMM tools has become especially dangerous: Throughout 2024, eCrime actors frequently used RMM…
If you’re just starting your journey into data science, you might think it’s all about Python…
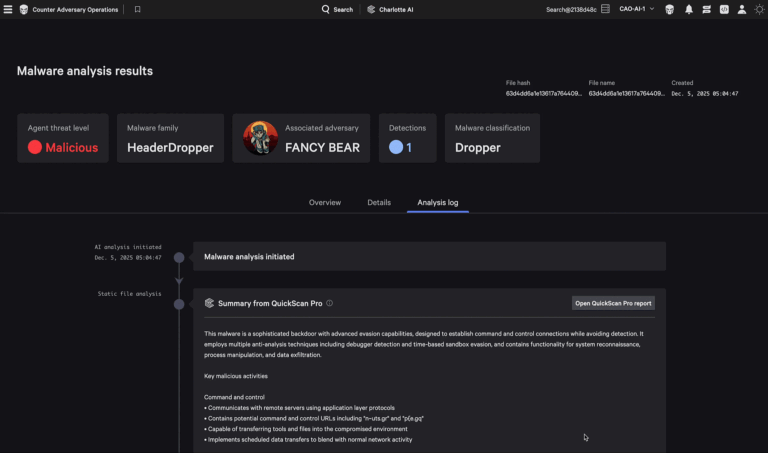
Charlotte AI is powered by a fully managed multi-agent architecture that orchestrates specialized agents across a…

Google Cloud Platform is a suite of cloud computing services that shares its running environment with…

Every now and then, we check Udemy out for the most rated courses in different niches…

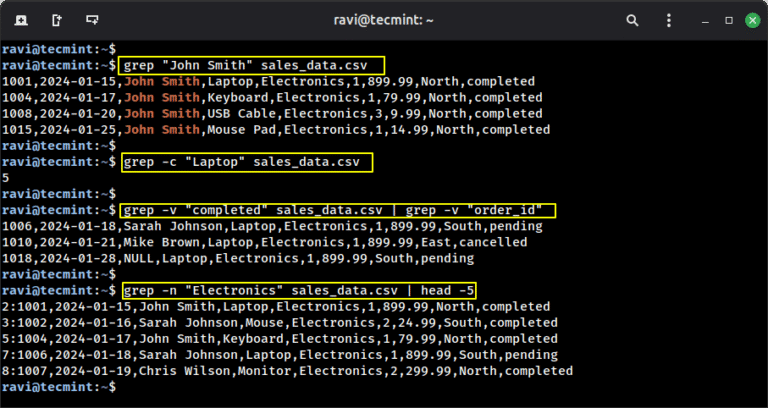
Python is often considered to be one of the most powerful, adaptable, and easy-to-learn high-level programming…

CrowdStrike is introducing real-time visibility and protection across browsers, local applications, shadow AI services, and cloud…
To solve this problem, the feature calculation code was updated to use the most recent version…
“Leakage” in machine learning (ML) occurs when data that an ML model should not learn on…