AI vs. AI: The Race Between Adversarial and Defensive Intelligence
But while AI empowers analysts to operate with greater speed and precision, this evolution is forging…
But while AI empowers analysts to operate with greater speed and precision, this evolution is forging…
Falcon Identity Protection is built for modern enterprises that demand comprehensive, unified, and automated identity security….
Why Falcon Exposure Management Stands Out Partner Ecosystem: Our strong ecosystem and extensibility make it easier…
Envisioning the Future of Endpoint Protection Gartner has positioned CrowdStrike furthest right in Completeness of Vision…
The 2025 GigaOm Radar for SIEM highlights the notable shift to vendors offering full platforms for…
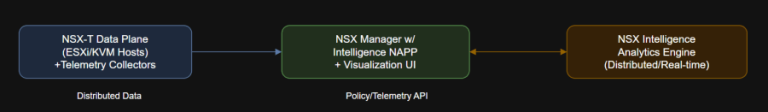
Table of Contents Introduction NSX Intelligence NAPP Architecture Deep Dive Real-World Deployment Patterns Microsegmentation with NSX…

What’s New in VCF 9 (with NSX) GUI steps and automation for these features follow similar…
Over the past year, we’ve expanded and strengthened the digital operations capabilities that have long supported…

OCR stands for optical character recognition, and software of this type is designed to convert images,…
The Germany-Singapore team was composed of experts from the German Bundeswehr, Singapore’s Digital and Intelligence Service…

The real-world assessments conducted by respected testing authorities such as AV-Comparatives help ensure the Falcon platform…
According to the IDC MarketScape: Strengths Recognized in the IDC MarketScape We believe CrowdStrike’s inclusion as…
Customers need both Falcon Exposure Management and Falcon Next-Gen SIEM to use this capability. AI-powered Asset…

Today, I’m going to show you a simple but effective way to automatically block suspicious IPs…
Today’s adversaries have their sights set on identities. They’re using stolen credentials and social engineering techniques…