CrowdStrike 2025 APJ eCrime Landscape Report: A New Era of Threats Emerges
The eCrime threat landscape in the Asia Pacific and Japan (APJ) region is quickly evolving, driven…
The eCrime threat landscape in the Asia Pacific and Japan (APJ) region is quickly evolving, driven…
ExPRT.AI is trained to rank vulnerabilities based on how likely they are to be exploited in…
We believe our placement as a Visionary, coupled with our groundbreaking AI innovations and the acquisition…
The observed activity appears to begin with an HTTP POST request to /OA_HTML/SyncServlet, which initiates the…

These new innovations are the essential pillars that define the agentic security platform. We are living…
The fundamental shift we’re seeing is moving security professionals from operators to orchestrators. Today, we have…
Strengths Recognized in the Frost Radar Read the full report: 2025 Frost Radar™: Cloud Workload Protection…

Many security teams struggle with threat hunting because they don’t know where to start or what…
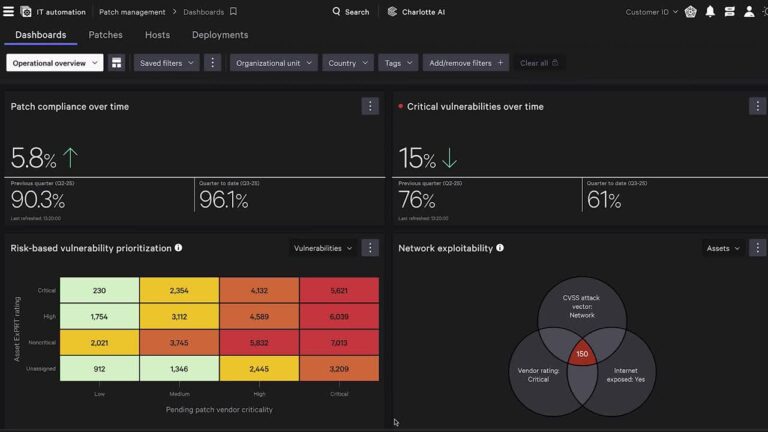
Traditional vulnerability management is broken. Security teams rely on one set of tools to find vulnerabilities;…
The Falcon platform’s console unifies fragmented data, bridges silos, and translates complex queries into natural-language conversations….
Core Technology that Powers Security for AI Data remains the primary target for adversaries, but traditional…
Stopping Breaches with Platform-Native Speed and Expertise With over 100,000 hours of IR casework annually, CrowdStrike…
Security teams today face a data crisis: Exploding volumes of security and IT telemetry are difficult…
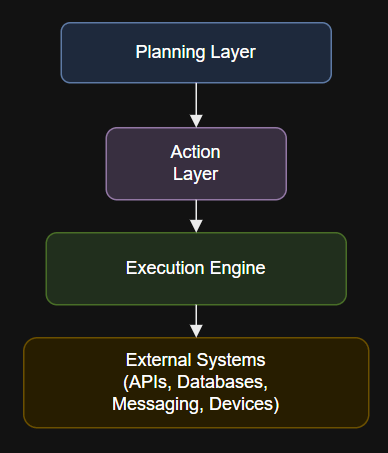
Introduction @app.task(bind=True, max_retries=3)def execute_api_action(self, endpoint, payload):try:response = requests.post(endpoint, json=payload, timeout=10)response.raise_for_status()return {“status”: “success”, “response”: response.json()}except Exception as…
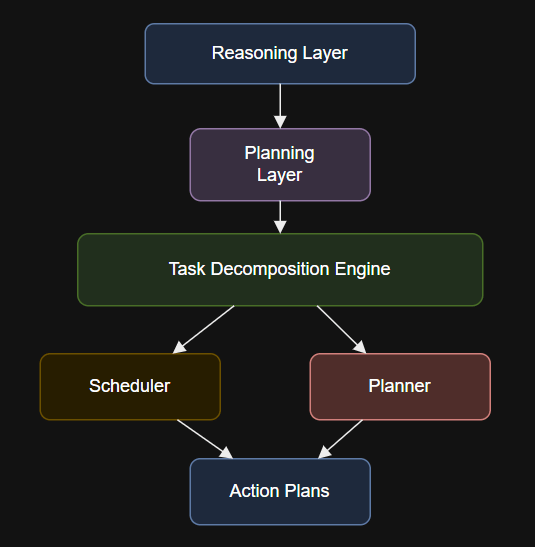
Introduction def notify_team(**kwargs):print(“Notifying team…”) What This Layer Is and Why It Matters Explore workflow planning and…