How CrowdStrike’s Malware Analysis Agent Detects Malware at Machine Speed
Under the Hood: How It Works Step 3: Dynamic behavioral analysis Step 5: Similar sample identification…
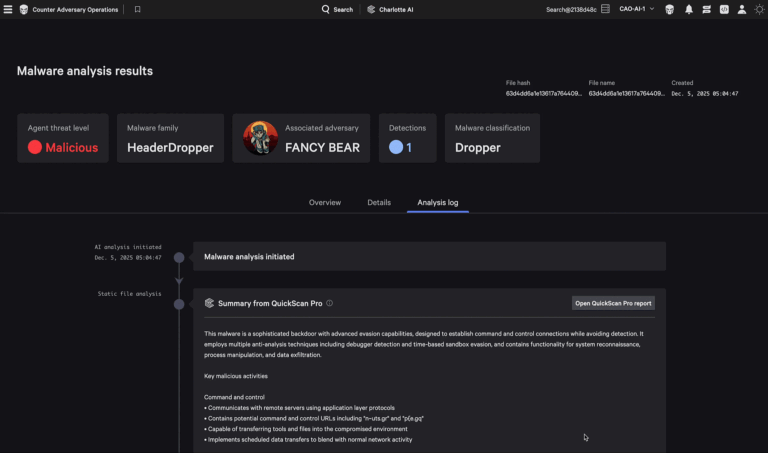
Under the Hood: How It Works Step 3: Dynamic behavioral analysis Step 5: Similar sample identification…
Rather than manually annotating thousands of queries (an expensive and time-consuming process), we leveraged NVIDIA NeMo…
With the cluster infrastructure in place through the Vertex Training Cluster, we configured Slurm, the industry-standard…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
Organizations are under pressure to protect more devices, users, and distributed workloads than ever — while…
Traditional security tools were never built to protect AI assets across domains or the new AI…
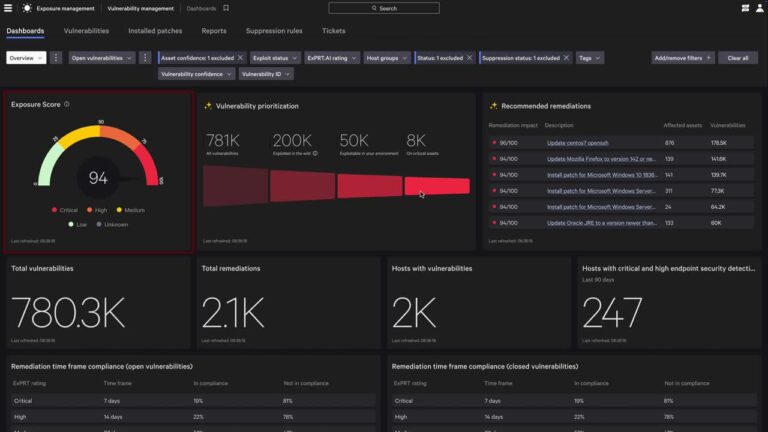
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…

In the MUSTANG PANDA scenario, the adversary embedded encoded shellcode within their malware in an attempt…
WARP PANDA demonstrates a high level of stealth and almost certainly focuses on maintaining persistent, long-term,…
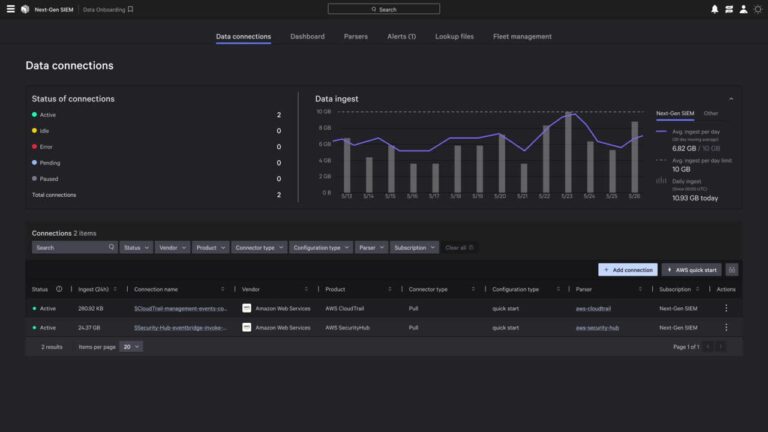
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….

ABOUT ENERGAGEAt Volusion, our dedicated team of developers, marketers, designers, and technical support experts are passionate…
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
The outcomes that matter most — speed, accuracy, cost, and real-time risk reduction — can only…