CrowdStrike 2026 Global Threat Report: The Evasive Adversary Wields AI
To defend themselves, security leaders need clarity on which adversaries to watch, the details of their…
To defend themselves, security leaders need clarity on which adversaries to watch, the details of their…
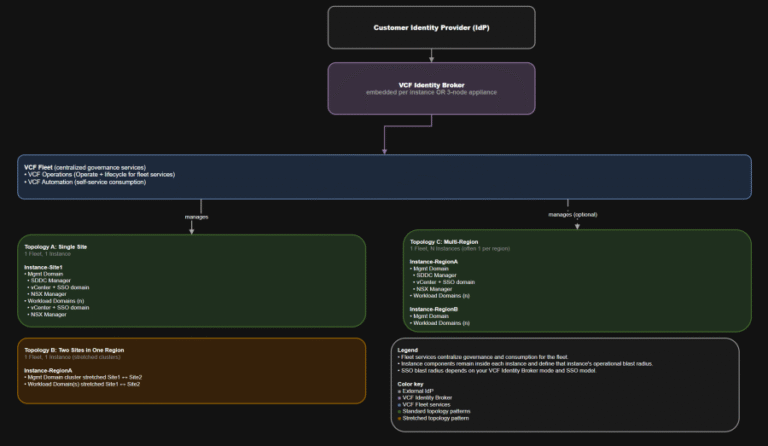
TL;DR This post targets VCF 9.0 GA only: VCF 9.0 (17 JUN 2025) build 24755599, with…
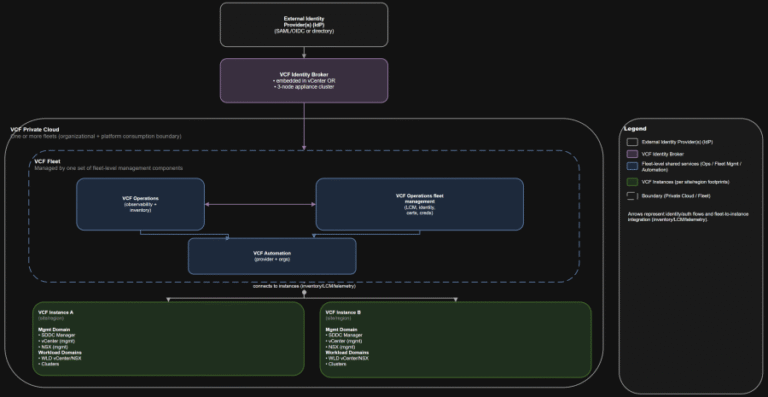
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…
CrowdStrike Falcon Identity Protection — A Great Tool to Gain Visibility We remain committed to innovating…
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…

SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
Christoph Bausewein is Assistant General Counsel for Data Protection and Policy at CrowdStrike.This creates a new…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
Expert Agents: Native AI Reasoning Across the Falcon Platform Effective threat triage requires correlating evidence across…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
The AI era is here — and it’s redefining cybersecurity. Organizations around the globe are adopting…