University of Sunderland Goes from Ransomware Recovery to Proactive Defense with CrowdStrike
Since its customer story was first published in 2023, the University of Sunderland has expanded its…
Since its customer story was first published in 2023, the University of Sunderland has expanded its…

SE Labs reports the Falcon platform detected all ransomware attacks, earning a 100% Detection Accuracy Rating….

The CrowdStrike Falcon® platform earns the AAA award in SE Labs Q3 2024 Enterprise Advanced Security…
Rate Companies (formerly Guaranteed Rate) is the second-largest retail mortgage lender in the U.S. With billions…
A comprehensive, unified approach to cloud security is more important than ever as adversaries increasingly target…
Over the last 18 months, bring your own vulnerable driver (BYOVD) attacks have escalated significantly as…
Solar’s chief information security officer is Frank Christensen, who took on the role in 2020. While…
LIMINAL PANDA’s known intrusion activity has typically abused trust relationships between telecommunications providers and gaps in…
Beyond performance issues, the company sought modern endpoint security to protect the company from attack. This…
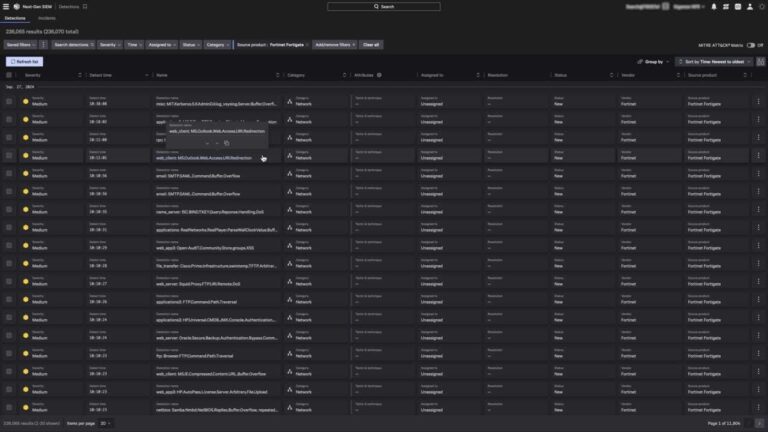
This collaboration brings together the strengths of two cybersecurity leaders — CrowdStrike in endpoint security and…
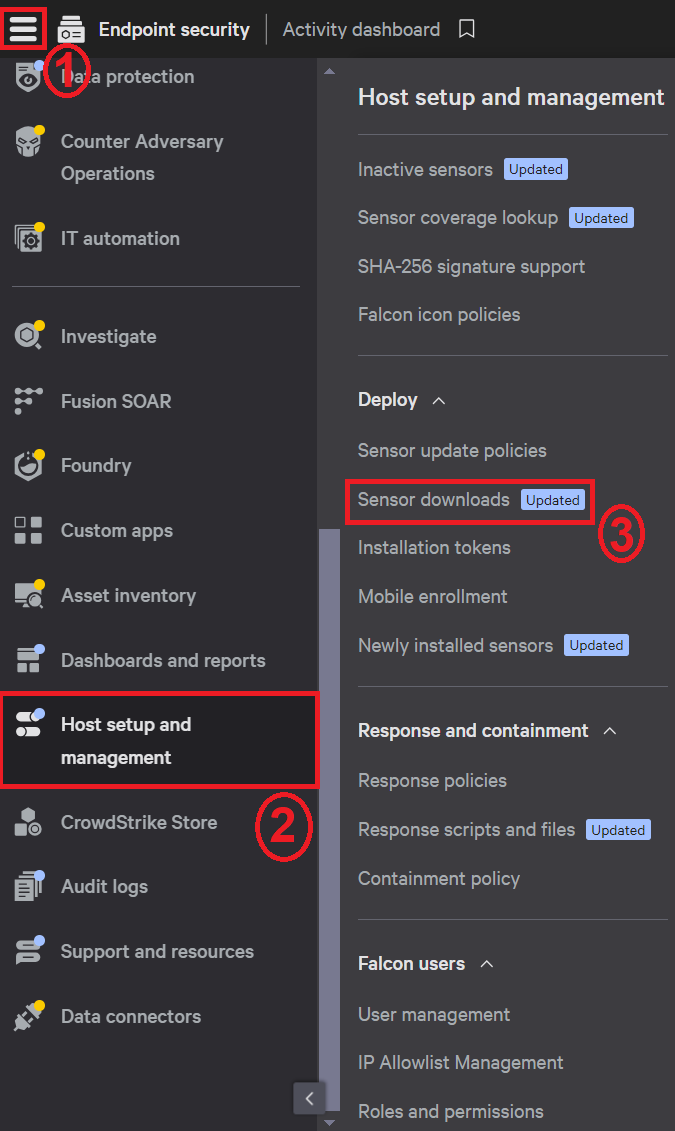
Confirming Installation Confirming Installation Installing the Sensor