VCF 9.0 GA Mental Model Part 6: Topology and Identity Boundaries for Single Site, Dual Site, and Multi-Region
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
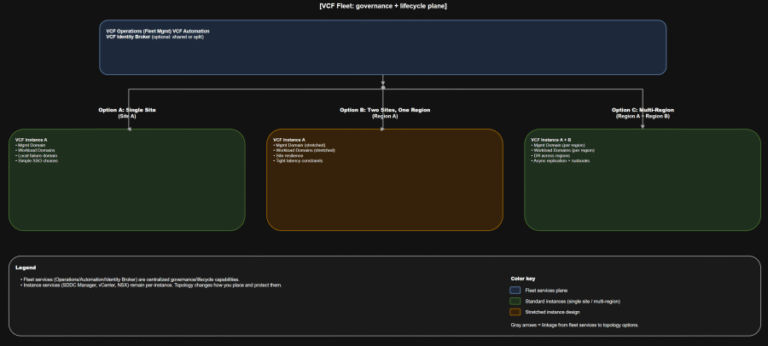
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
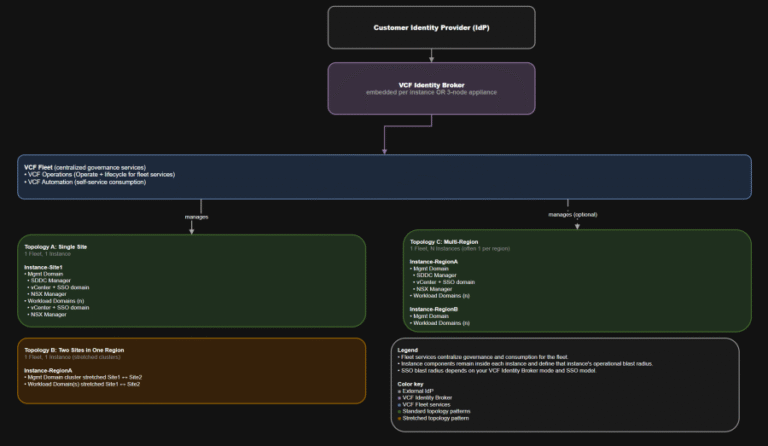
TL;DR This post targets VCF 9.0 GA only: VCF 9.0 (17 JUN 2025) build 24755599, with…
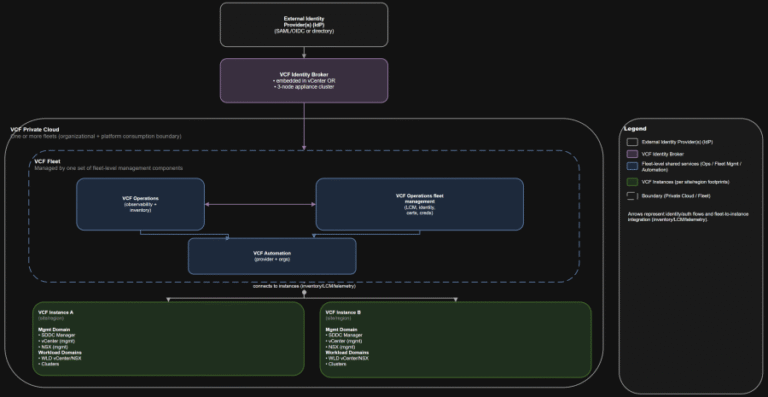
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…

SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…

In this article, we show you how to encrypt files with GPG in Linux, generate key…
These content packs span multiple categories including application resilience, file discovery, Linux device control, and asset…
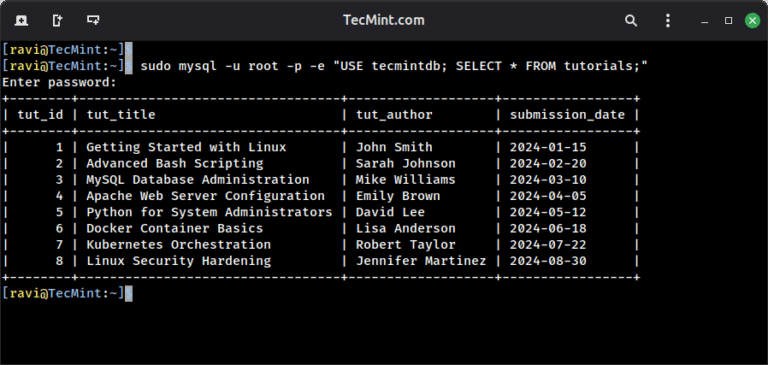
If you are in charge of managing a database server, from time to time you may…
Here, we examine a case study in which CrowdStrike OverWatch threat hunters identified and disrupted BLOCKADE…

The “404 Not Found” error during upgrade occurs when your system attempts to download packages from…
AI-enhanced social engineering poses particular challenges. Attackers use generative AI to craft contextually appropriate phishing emails…
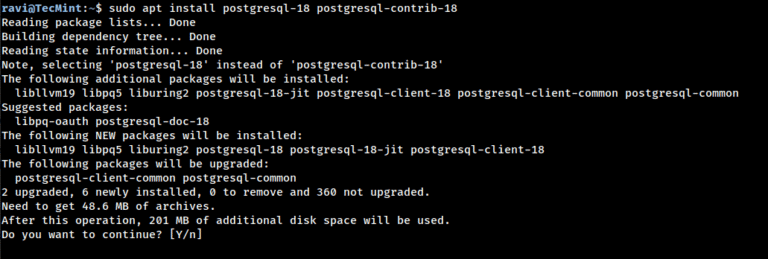
PostgreSQL (Postgres in short) is an open source, powerful, advanced, high-performance, and stable relational-document database system,…
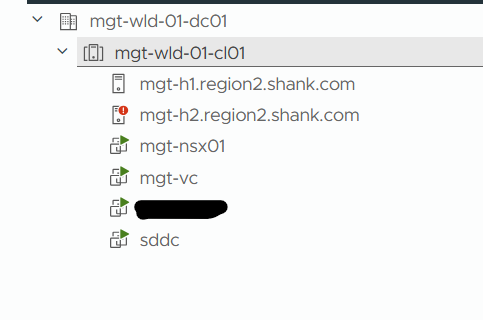
October 13, 2025 VCF 9 Fleet Deployment Task Fails The Issue? As with any failed deployment,…
In our previous articles, we’ve covered MySQL interview questions for beginners and intermediate users, and the…
Linux is an open-source operating system whose use is increasing these days as a result of…
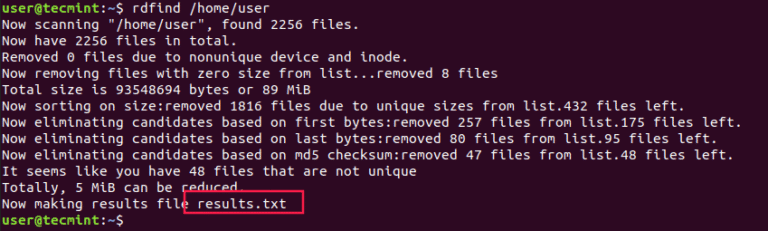
Organizing your home directory or even system can be particularly hard if you have the habit…