After You Migrate: Cleanup, Governance, and Preventing Unmanaged Disks from Coming Back
TL;DR Converting disks is not the finish line. Your real goal is a new steady state:…
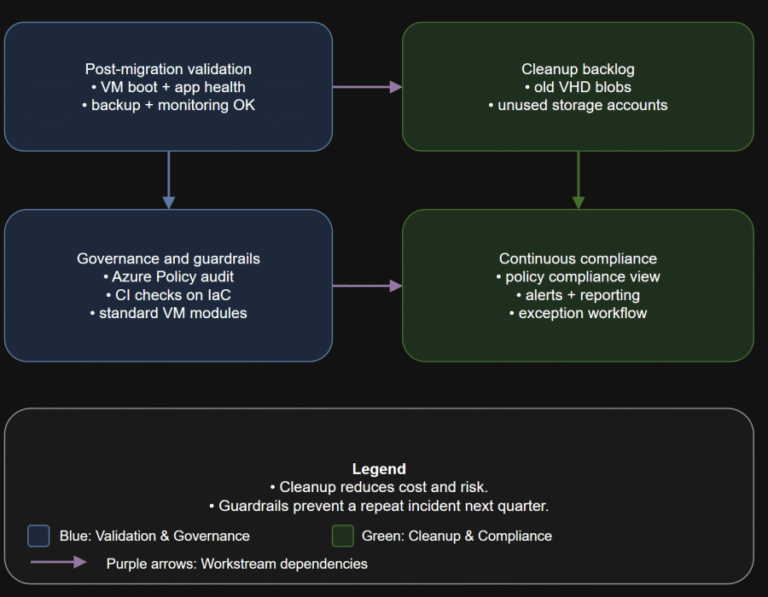
TL;DR Converting disks is not the finish line. Your real goal is a new steady state:…
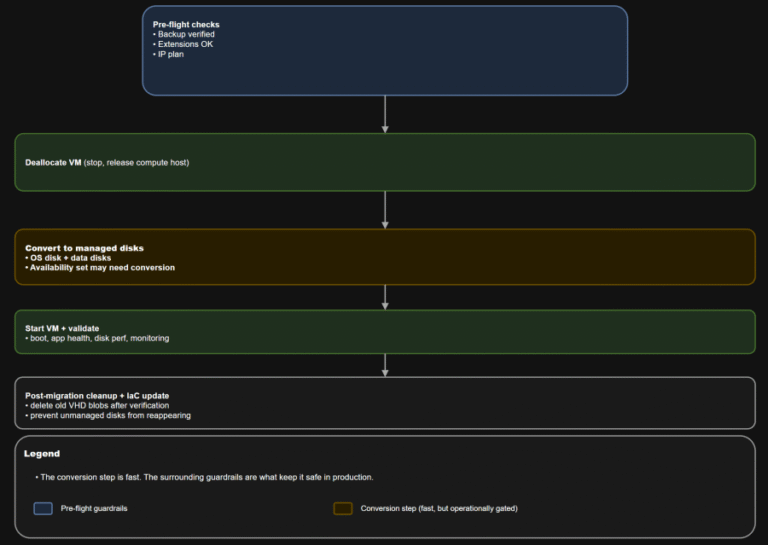
TL;DR Converting a VM to managed disks is usually operationally straightforward: deallocate, convert, start, validate. The…
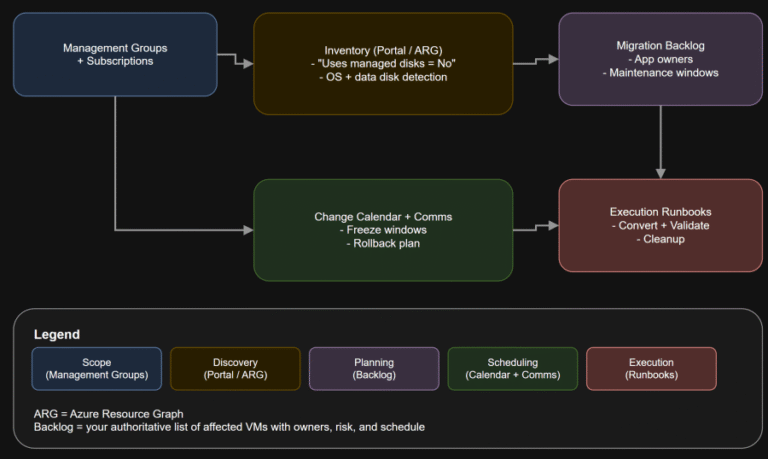
TL;DR If any Azure IaaS VM in your estate still uses unmanaged disks, it is on…
Actively Exploited Zero-Day Vulnerability in Windows Remote Desktop The vulnerability allows local attackers with no privileges…
As AI adoption accelerated, WEX® — a global commerce platform that supports business operations primarily for…
Unified classification: Apply consistent classifications for financial data, personally identifiable information (PII), protection health information (PHI),…

These reports include:With Falcon Cloud Security data correlated in Falcon Next-Gen SIEM, teams can detect cross-domain…
Windows 10 End of Support Is Here There is evidence of active exploitation in the wild…
For off-the-shelf capabilities like Bedrock or Vertex AI, Falcon Cloud Security identifies the APIs and services…
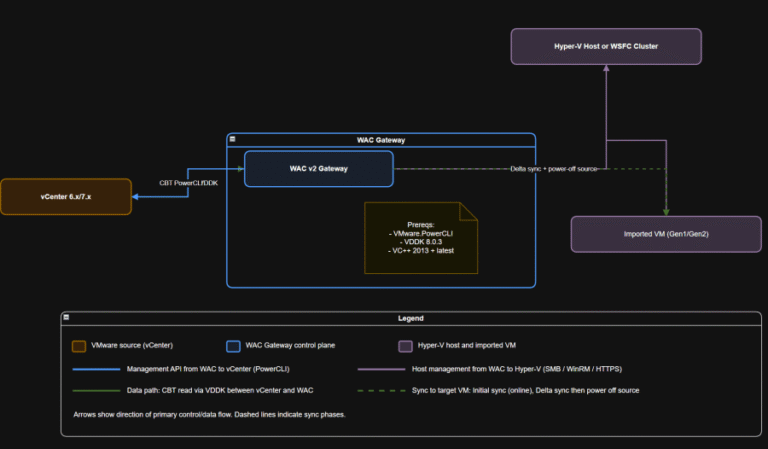
Compliance checkpoints (examples) Why this matters Bridge strategy: If you are standardizing on Windows Server and…
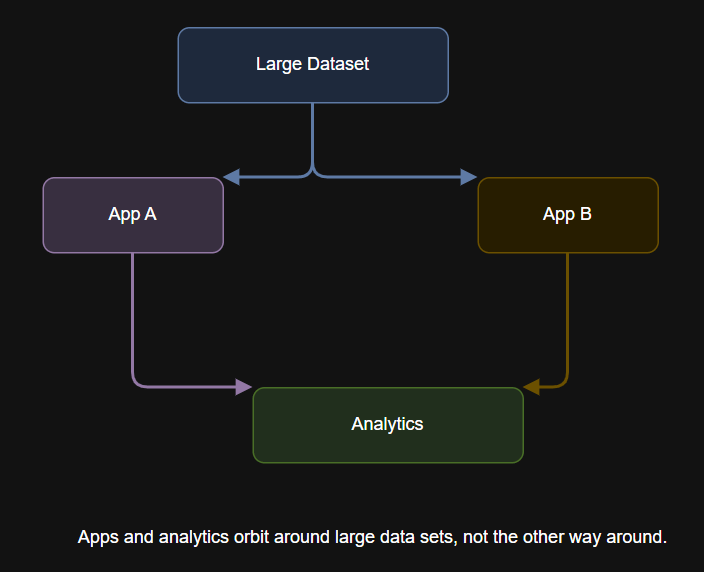
Table of Contents What Is Data Gravity? The History and Evolution of Data Gravity Why Data…
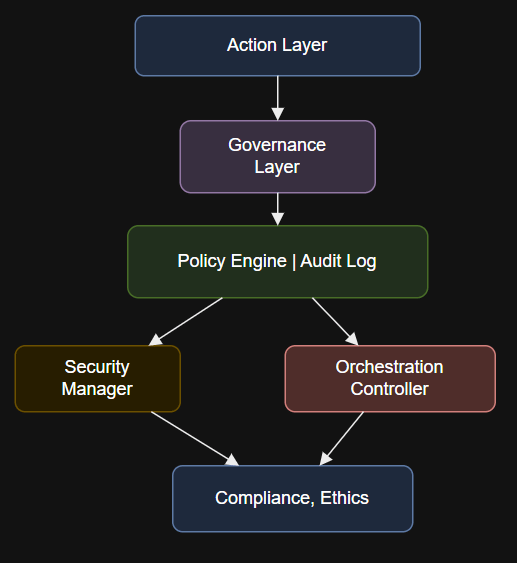
Introduction if __name__ == “__main__”:# Example: Validate if a user action is allowed by enterprise policyinput_payload…
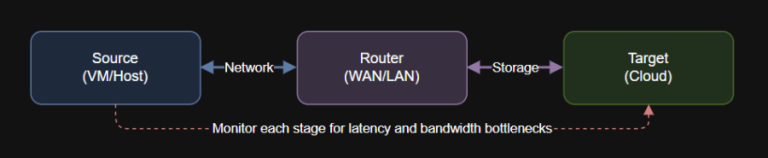
Introduction Data movement in cloud and hybrid architectures is only as fast as your slowest link….
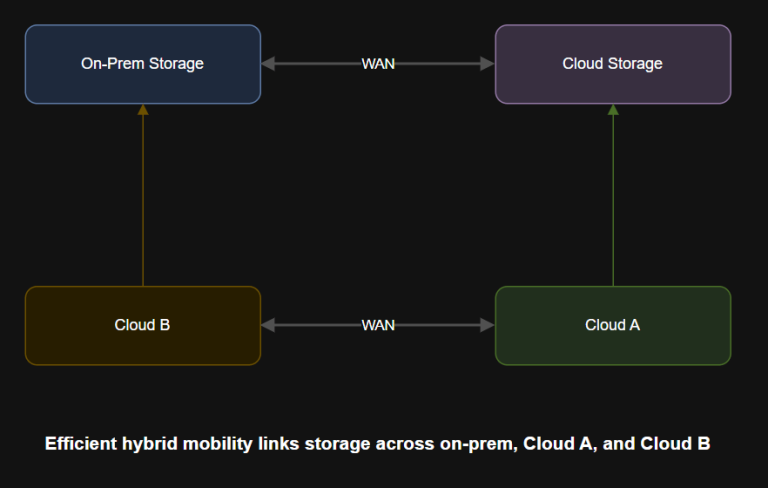
Introduction A media company needs to replicate video assets from on-prem storage to both Azure and…

Introduction A global retailer must store EU customer data within European borders to comply with GDPR….