CrowdStrike Named a Customers’ Choice in 2026 Gartner® Voice of the Customer for Endpoint Protection Platforms
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
Updated: This article has been refreshed to cover the latest ways to edit documents on Ubuntu…
Expert Agents: Native AI Reasoning Across the Falcon Platform Effective threat triage requires correlating evidence across…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
Rather than manually annotating thousands of queries (an expensive and time-consuming process), we leveraged NVIDIA NeMo…
With the cluster infrastructure in place through the Vertex Training Cluster, we configured Slurm, the industry-standard…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
The AI era is here — and it’s redefining cybersecurity. Organizations around the globe are adopting…
Organizations are under pressure to protect more devices, users, and distributed workloads than ever — while…
Traditional security tools were never built to protect AI assets across domains or the new AI…
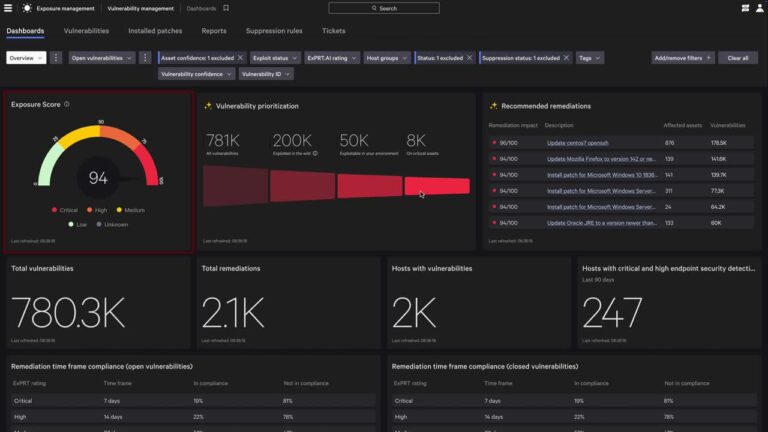
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…

In the MUSTANG PANDA scenario, the adversary embedded encoded shellcode within their malware in an attempt…