CrowdStrike Named a Customers’ Choice in 2026 Gartner® Peer Insights™ Voice of the Customer for User Authentication
CrowdStrike Falcon Identity Protection — A Great Tool to Gain Visibility We remain committed to innovating…
CrowdStrike Falcon Identity Protection — A Great Tool to Gain Visibility We remain committed to innovating…
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…
Indirect prompt injection significantly amplifies this risk by allowing adversaries to influence OpenClaw’s behavior through data…
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
In this article, you will discover the best software tools powered by AI that you can…
As AI adoption accelerated, WEX® — a global commerce platform that supports business operations primarily for…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
Rather than manually annotating thousands of queries (an expensive and time-consuming process), we leveraged NVIDIA NeMo…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
Traditional security tools were never built to protect AI assets across domains or the new AI…
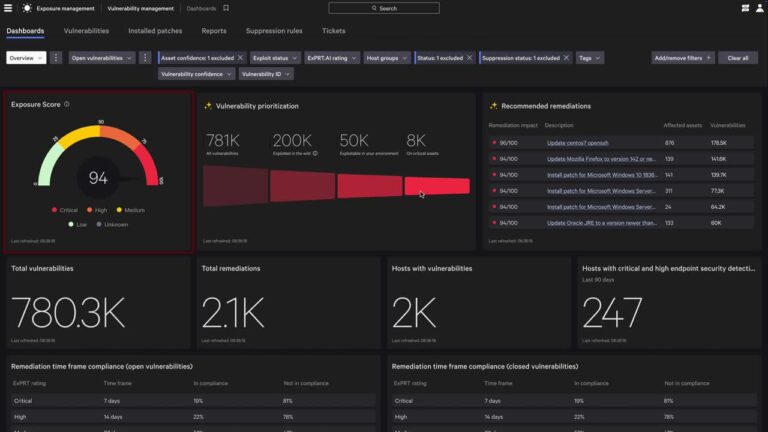
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…