Inside the Human-AI Feedback Loop Powering CrowdStrike’s Agentic Security
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…
The Human-AI Feedback Loop in Action Expert-Annotated Data Enables Analyst Grade AI 2 Time savings represents…
Indirect prompt injection significantly amplifies this risk by allowing adversaries to influence OpenClaw’s behavior through data…
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
Identity has become a key battleground of modern cybersecurity. In 2024, 79% of CrowdStrike detections were…
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
The fundamental shift we’re seeing is moving security professionals from operators to orchestrators. Today, we have…
It is time once again to share a list of the best free and open-source software…
Core Technology that Powers Security for AI Data remains the primary target for adversaries, but traditional…
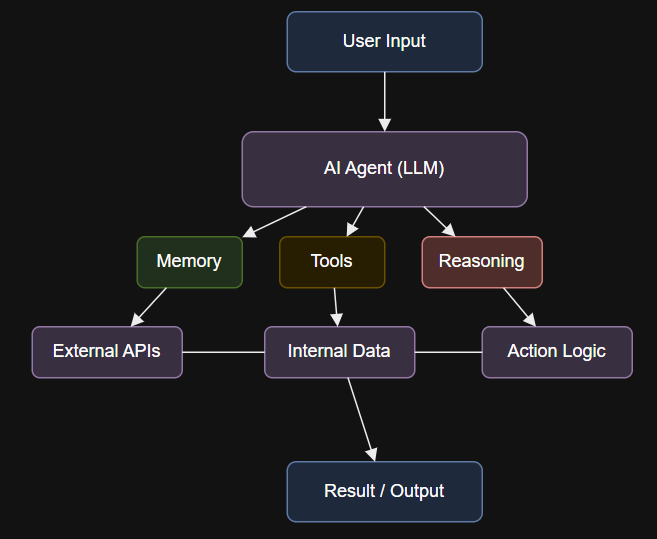
Introduction Run the agent, triggering the entire research and drafting process: What Sets AI Agents Apart?…