Introduction
– name: Convert expiry date to epoch
set_fact:
cert_expiry_date: “{{ cert_expiry_raw.stdout | trim }}”
cert_expiry_epoch: “{{ cert_expiry_date | to_datetime(‘%b %d %H:%M:%S %Y %Z’) | to_timestamp }}”
My Personal Repository on GitHub
– name: Fail if certificate is expiring soon
fail:
msg: “❌ Nutanix Prism certificate will expire in {{ days_left }} days!”
when: days_left < warn_days
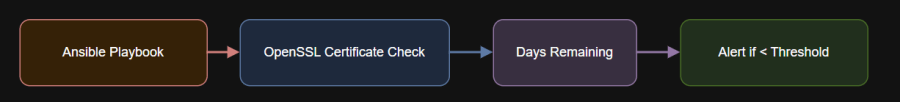
Diagram: Certificate Monitoring Workflow
Use Case
- Prevent expired Prism Central or Element SSL certs
- Integrate checks into daily Ansible runs
- Schedule automated email alerts for SecOps
Prerequisites
opensslinstalled on Ansible control host- Prism hostname or IP address
- Optional: SMTP or Slack alert configured
Sample Playbook: check_cert_expiry.yml
– name: Get current date in epoch
set_fact:
now_epoch: “{{ ansible_date_time.epoch | int }}”
days_left: “{{ (cert_expiry_epoch – now_epoch) // 86400 }}”ansible-playbook check_cert_expiry.yml -i localhost,
Optional Enhancements
- Send
mailxalert whendays_left< threshold - Push Slack webhook on expiry detection
- Store historical expiry data in a log file or dashboard
Schedule It
– name: Print result
debug:
msg: “SSL certificate expires in {{ days_left }} days on {{ cert_expiry_date }}”- name: Check SSL certificate expiry for Nutanix Prism
hosts: localhost
gather_facts: false
vars:
prism_host: "prism.example.com"
warn_days: 30
tasks:An expired SSL certificate in Nutanix Prism Central can cause major disruptions to GUI access and API integrations. This article shows how to automate Prism certificate checks using Ansible, alerting your ops team before certificates reach expiration. No more last-minute fire drills.
Run It
Nutanix Repository on GitHub
External Documentation:
30 7 * * * ansible-playbook /opt/playbooks/check_cert_expiry.yml
Summary
Automating certificate expiry checks with Ansible improves uptime and strengthens your security posture. Use this lightweight task as part of your daily automation suite or integrate into alerting pipelines.