Introduction
Security-sensitive workloads often require encryption at rest and support for virtual TPM (vTPM) devices. These features are built into vSphere and can be automated using PowerCLI. This article shows how to encrypt virtual machines, manage encryption policies, configure vTPM devices, and validate encryption status programmatically.
You can also verify TPM status:
- Enabling VM encryption
- Assigning KMS-based storage policies
- Adding virtual TPM devices to VMs
- Auditing encryption and vTPM compliance
- Error handling and operational guidance
Prerequisites
Get-VM | Select Name, PowerState, @{N="Encrypted";E={$_.ExtensionData.Config.VmEncryptionInfo}}, VMHost | Export-Csv "C:ReportsVM_Encryption_Status.csv" -NoTypeInformation
Diagram: Encryption and TPM Workflow
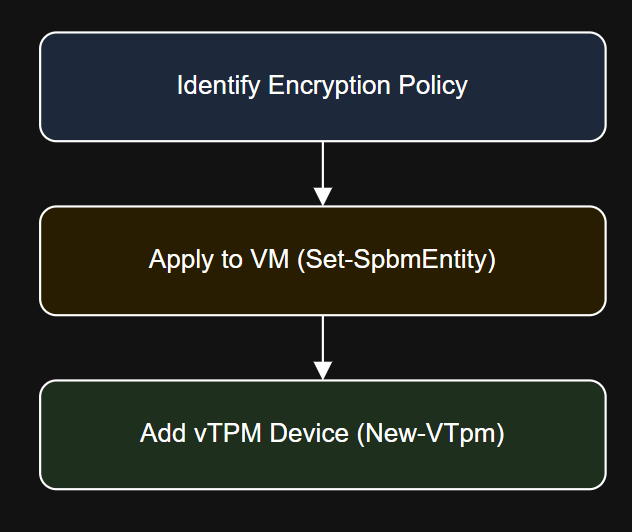
Use Case: Secure Workload Baseline for New App Tier
$vm.ExtensionData.Config.VAppConfig.Properties | Where-Object {$_.Label -eq "TPM Enabled"}
Step 5: Verify Encryption and TPM Status
$vm = Get-VM -Name "SQLSecure01"
$policy = Get-SpbmStoragePolicy -Name "VM Encryption Policy"$vm = Get-VM -Name "SecureApp01"PowerCLI automatically migrates the VM to an encrypted storage policy if supported.
Step 2: Encrypt an Existing VM
Topics include:
Get-SpbmStoragePolicy | Where-Object {$_.Name -like "*Encrypt*"}
Connect to vCenter:
- Hardware version 14 or newer
- Encrypted VM home files
New-VM -Name "SecureApp01" `
-Template "Win2019-Base" `
-Datastore "Encrypted-DS" `
-VMHost "esxi01.lab.local" `
-StoragePolicy $policy
Step 4: Add vTPM to a VM
If no policy exists, create one in vSphere Client that uses KMS-backed encryption rules.
New-VTpm -VM (Get-VM -Name "NewFinanceVM")
Troubleshooting
| Problem | Fix |
|---|---|
| Encryption fails with error | Ensure KMS is configured and policy is available |
| vTPM device not allowed | VM must use encrypted VM home and hardware version 14 or later |
| Set-SpbmEntityConfiguration fails | Confirm datastore supports encryption and policy is correct |
| Encryption compliance shows Unknown | Wait for sync or rescan policies via vCenter |
What’s Next
New-VM -Name "NewFinanceVM" `
-Template "Encrypted-Win2022-Base" `
-VMHost "esxi02.lab.local" `
-Datastore "SecureDS" `
-StoragePolicy (Get-SpbmStoragePolicy -Name "VM Encryption Policy")
Before automating encryption:
Connect-VIServer -Server "vcenter.lab.local"
Step 1: Identify or Create Encrypted Storage Policy
List available policies:
- Disaster recovery automation using PowerCLI
- Snapshots, exports, and failover preparation scripting