Indirect Prompt Injection Attacks: A Lurking Risk to AI Systems
There are two basic types of prompt injection attacks: Understanding Prompt Injection Employee BYO AI adoption…
There are two basic types of prompt injection attacks: Understanding Prompt Injection Employee BYO AI adoption…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…

When someone visits your website, their browser and your server exchange information back and forth. Without…
CrowdStrike uses NVIDIA Nemotron open models in CrowdStrike Falcon® Fusion SOAR and CrowdStrike Charlotte AI™ AgentWorks….
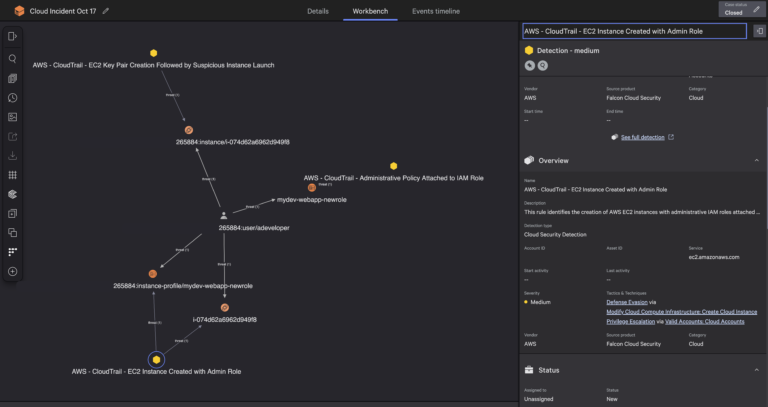
Falcon Cloud Security has implemented a new approach which processes cloud logs as they stream in…
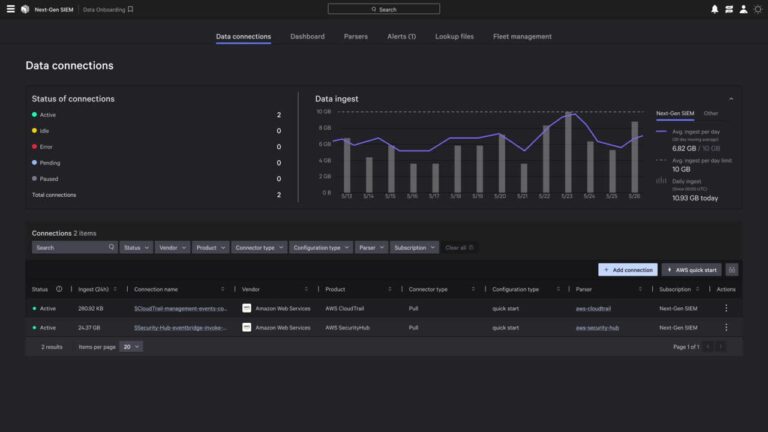
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…
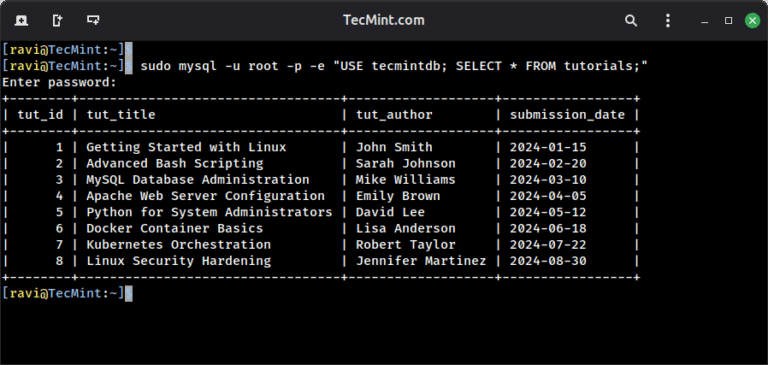
If you are in charge of managing a database server, from time to time you may…
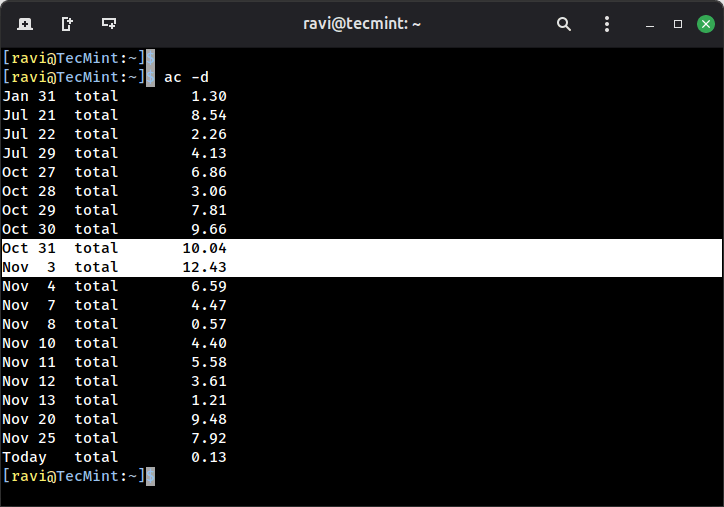
When you’re managing a Linux server, especially one with multiple users, you need visibility into what’s…
Managing a web server through command-line alone can feel like you’re juggling too many things at…
Unified classification: Apply consistent classifications for financial data, personally identifiable information (PII), protection health information (PHI),…
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….

Apple iWork is Apple’s suite of office applications, similar to Microsoft Office or Google Docs, consisting…
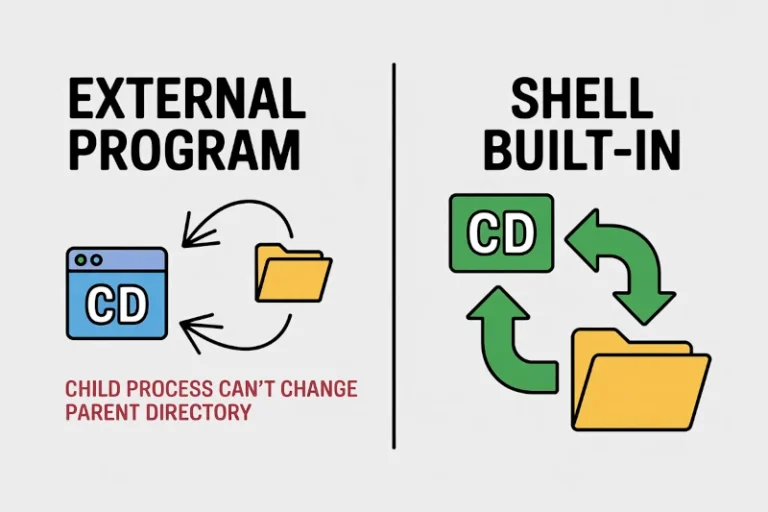
In Linux, the ‘cd‘ (Change Directory) command serves as a fundamental navigation tool for both newcomers…
Here, we examine a case study in which CrowdStrike OverWatch threat hunters identified and disrupted BLOCKADE…

ABOUT ENERGAGEAt Volusion, our dedicated team of developers, marketers, designers, and technical support experts are passionate…