April 2025 Patch Tuesday: One Zero-Day and 11 Critical Vulnerabilities Among 121 CVEs
Actively Exploited Zero-Day Vulnerability in Windows Common Log File System CVE-2025-27491 is a Critical RCE vulnerability…
Actively Exploited Zero-Day Vulnerability in Windows Common Log File System CVE-2025-27491 is a Critical RCE vulnerability…
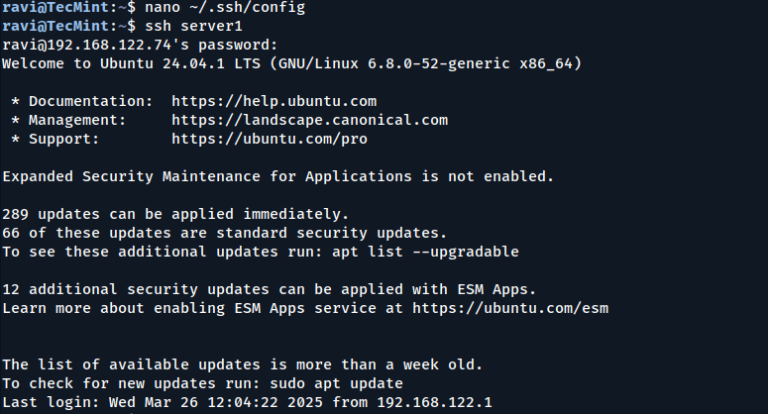
If you use Linux or manage remote servers (like cloud servers on AWS, DigitalOcean, or even…
For over a decade, CrowdStrike has leveraged AI to enhance cloud security. CrowdStrike Falcon Cloud Security…
Notepad++ is a completely free source code editor created as a replacement for Notepad on Windows…
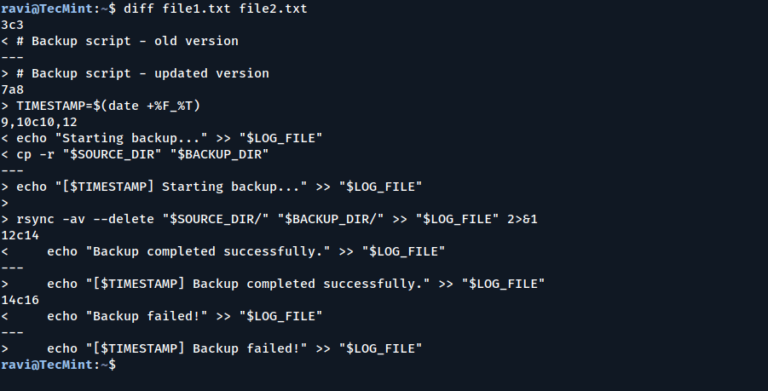
In the world of Linux system administration and development, comparing files is an essential task when…
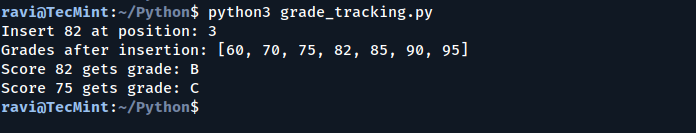
As developers, we often stick to our favorite built-in Python functions and sometimes even write custom…

As Linux users, we often rely on our go-to commands ls, grep, awk, sed, and find…
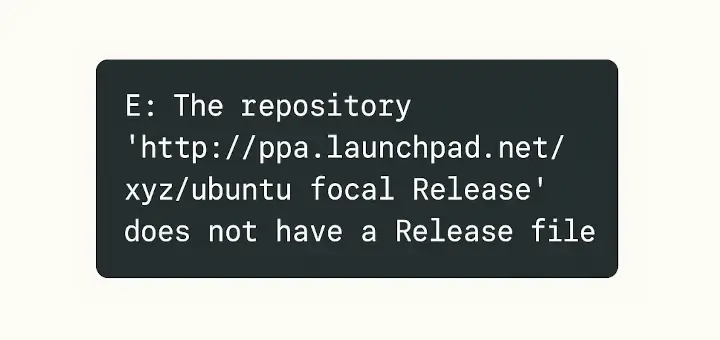
When managing software packages on Debian/Ubuntu-based systems, it’s common to add external repositories or Personal Package…
The CrowdStrike 2025 Global Threat Report illustrates the urgent need for strong identity protection as adversaries…
Patching as soon as possible is highly recommended. Alternatively, removing the ValidatingWebhook can be used as…
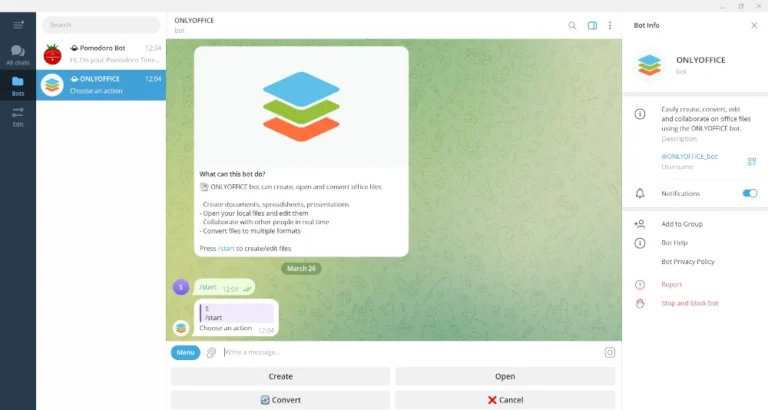
Telegram has eventually become something more than a mere messaging app since its official release in…
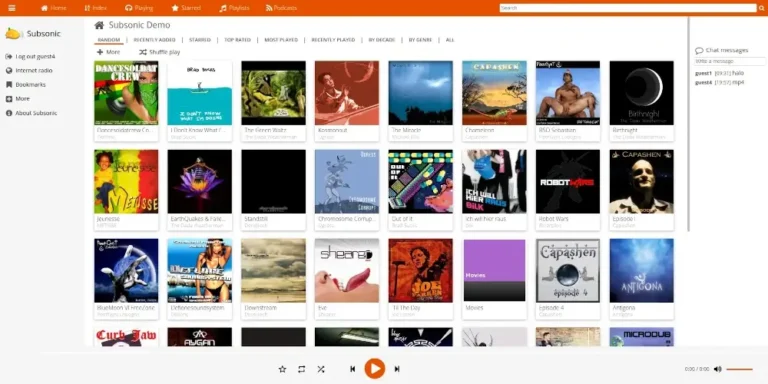
If you’re looking for a powerful and easy-to-use media streaming solution, Subsonic is an excellent choice…
OpenRC is a fast and lightweight init system used by many Linux distributions like Alpine, Gentoo,…
pCloud is a most secure popular cloud storage service that offers a range of features to…

In our previous article, we explored the top 5 command line archive tools, including tar, shar,…