How to Check Exit Status for Command in Linux
When working on a Linux system, every command you run returns a status code (also called…
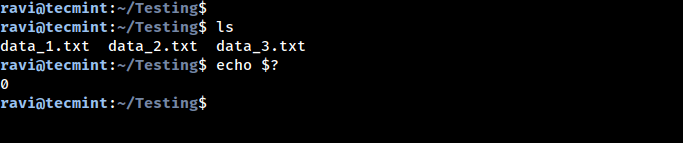
When working on a Linux system, every command you run returns a status code (also called…

DNS (Domain Name System) is a fundamental facilitator of several networking technologies such as mail servers,…
Learning Objectives $message = @{text = “VM $vmName has been powered off via automation.”} | ConvertTo-Json…
It is time once again to share a list of the best free and open-source software…
As someone who has been using Linux for more than 12 years, I’ve often come across…
A Visionary Leader in MDR See what other industry analysts are saying about CrowdStrike on our…
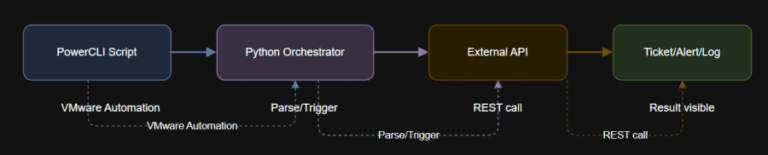
Learning Objectives $vmName = “<your-vm-name>”$outputFile = “C:Tempsnap_status.txt”if status == “FAILED”:url = “https://<your-jira-server>/rest/api/2/issue/”auth = (‘<jira-username>’, ‘<jira-api-token>’)headers =…
To solve this problem, the feature calculation code was updated to use the most recent version…
Since diagrams such as networks, organizational structures, system architectures, workflows, etc., have become an indispensable part…
With Volusion’s built-in marketing and discount tools, launching these campaigns has never been easier!Fall is full…
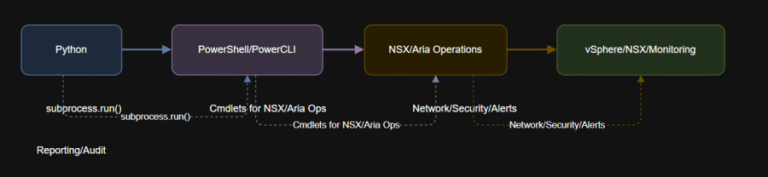
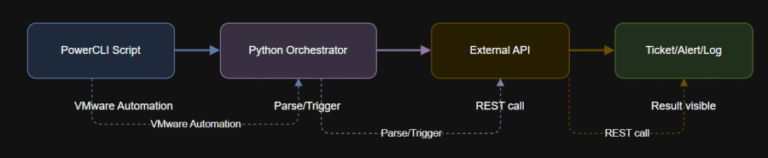
Learning Objectives Next up: In Article 9, you will learn to integrate PowerCLI with external APIs…
Core Technology that Powers Security for AI Data remains the primary target for adversaries, but traditional…

Zip is a command-line utility tool used for compressing files and folders. Compression of files &…
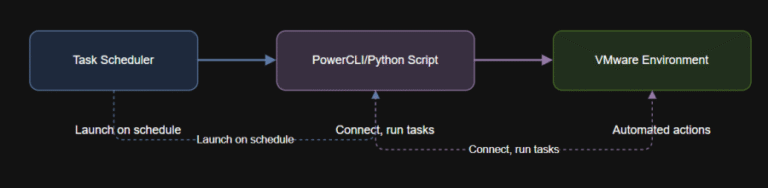
Learning Objectives By the end of this article, you will: Schedule PowerCLI and Python scripts for…
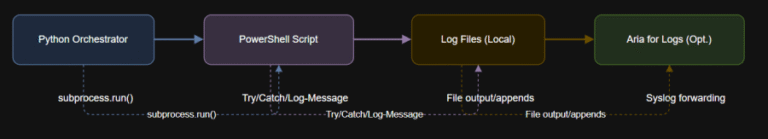
Learning Objectives Below is a PowerShell script that wraps key actions in error handling and logs…