Table of Contents
- Introduction
- NSX Intelligence NAPP Architecture Deep Dive
- Real-World Deployment Patterns
- Microsegmentation with NSX Intelligence
- Traffic Flow Analysis & Distributed Security Analytics
- Policy Automation and Operational Visibility
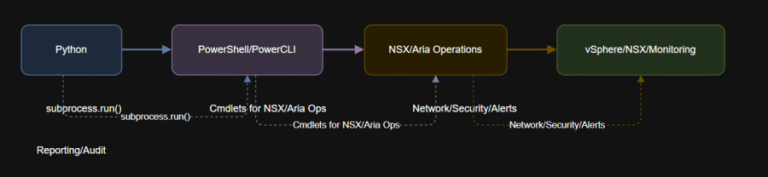
- Automation: PowerShell, Python, and API Workflows
- Troubleshooting & Best Practices
- Conclusion
Introduction
This article provides a technical deep dive into NSX Intelligence NAPP, focusing on architecture, operational workflows, advanced use cases, automation, and actionable troubleshooting for enterprise and hybrid deployments.
At its core, NSX Intelligence NAPP is an advanced analytics engine natively integrated into the NSX-T Data Center platform. It extends the NSX Manager by embedding security intelligence directly into the fabric, providing distributed, real-time analysis of network flows, policy evaluation, and automated segmentation recommendations.
NSX Intelligence NAPP Architecture Deep Dive
Automation Features:
NSX Intelligence NAPP is a transformative addition to the NSX-T platform, enabling real-time, distributed analytics and automated security policy lifecycle management. By leveraging advanced microsegmentation, contextual analytics, and seamless automation, organizations can achieve robust, operationally efficient, and auditable zero-trust security in both on-premises and hybrid cloud environments.
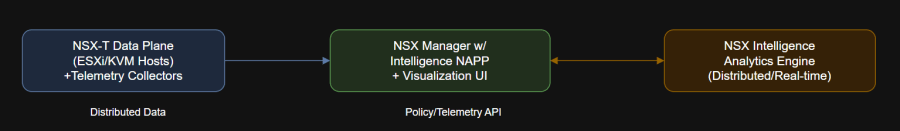
- NSX Manager with NAPP Module: Orchestrates policy, data collection, and analytics.
- Telemetry Collectors: Embedded in the NSX data plane, aggregating L2–L7 flow data.
- Analytics Engine: Processes telemetry, correlates with inventory, and generates policy recommendations.
- Visualization UI: Exposes dynamic maps, security overlays, and compliance dashboards within NSX Manager.
Key Architecture Components:
Real-World Deployment Patterns
Operational Dashboards:
- Single-site on-premises NSX-T clusters
- Stretched clusters with multi-site deployments
- Hybrid clouds: Integration with VMware Cloud (VMC) on AWS/Azure via NSX Federation
Topology Example:
- Pre-checks:
- Ensure NSX Manager is at required patch level
- Sizing: Allocate resources for analytics (CPU/RAM overhead is significant for large environments)
- Enable NAPP:
- In NSX Manager, navigate to System → Lifecycle Management → NAPPs
- Deploy and activate NSX Intelligence NAPP
- Telemetry Configuration:
- Validate that all transport nodes have collectors enabled
- Set telemetry interval to balance data granularity vs. resource impact
- Security Hardening:
- Restrict NAPP management to secure management segments
- Integrate with LDAP/AD for RBAC
- Monitoring:
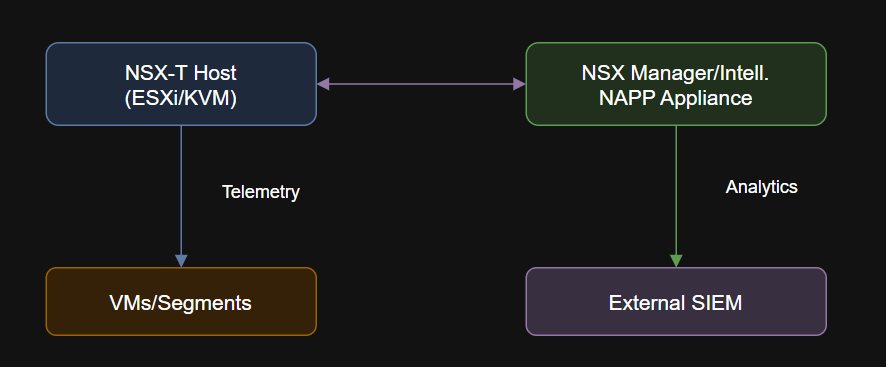
- Use NSX Manager and external SIEM (e.g., Splunk, Aria Operations for Logs) for operational monitoring
Advanced Capabilities:
Microsegmentation with NSX Intelligence
headers = {
“Authorization”: f”Bearer {token}”,
“Accept”: “application/json”
}
Best Practice Deployment Steps:
- Flow Mapping: Visualize all flows, with color-coded groupings (app tiers, tags, segments)
- Contextual Policy: Generate recommended rules based on observed traffic, user-defined labels, and dynamic security groups
- Automated Enforcement: One-click publishing of recommended policies to the Distributed Firewall (DFW)
Best Practices:
- Analyze application communications over a 7-day window
- NSX Intelligence groups flows by application, user, and workload tags
- Recommended segmentation rules are surfaced in the UI
- Admins review, customize, and publish to DFW
POST /policy/api/v1/intelligence/recommendations/{id}/publish
Authorization: Bearer <token>
Troubleshooting & Best Practices
Microsegmentation Flow:
- Real-Time Flow Visualization:
Dynamic, time-based maps of L2–L7 east-west traffic, including protocol, port, and user context. - Threat Detection:
Surface anomalous behavior and lateral movement using distributed analytics. - Compliance Tracking:
Visual dashboards for PCI, HIPAA, and custom regulatory frameworks.
Diagram:
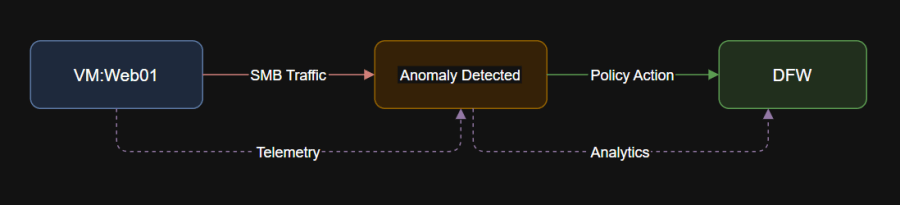
- Ransomware Containment:
Analytics identify unusual SMB/CIFS activity; auto-recommend DFW block rule with instant enforcement and audit logging.
Flow Analytics:
Policy Automation and Operational Visibility
Example Use Case:
- Scheduled policy assessments and drift detection
- Continuous compliance scans, with one-click remediation
- API-driven policy recommendation and deployment
- Export to Aria Operations, SIEM, or external compliance tools
response = requests.get(
f”{nsx_manager}/policy/api/v1/intelligence/flow-snapshots”,
headers=headers,
verify=False
)
print(response.json())
- Application dependency maps
- Unused rule identification
- “What-if” simulation for new security policies
Automation: PowerShell, Python, and API Workflows
PowerShell Example: Retrieve NSX Intelligence Recommendations
NSX Intelligence enables dynamic, context-driven microsegmentation by analyzing east-west flows in real time, visualizing app/service relationships, and automatically recommending DFW policies.Supported Topologies:Sample Workflow:
API Example: Publish Recommended DFW Policies
In today’s dynamic multi-cloud environments, network and security operations teams need more than just policy enforcement, they require continuous, granular, and automated visibility into every east-west flow. NSX Intelligence NAPP, integrated with NSX-T 4.x, delivers distributed analytics, contextual microsegmentation, and real-time policy recommendations, enabling true defense-in-depth and zero-trust security postures.
- NAPP Not Deploying: Validate resource allocation; check NSX Manager and appliance logs.
- Missing Flow Data: Ensure all hosts are properly licensed and telemetry services are enabled.
- Policy Recommendation Errors: Synchronize clocks; validate connectivity between NSX Manager and hosts.
- Performance Impact: For large-scale or hybrid deployments, consider dedicated appliances and staggered telemetry intervals.
# Authenticate and retrieve recommendations
$nsxManager = "https://nsx-manager.local"
$cred = Get-Credential
$headers = @{
"Accept" = "application/json"
"Content-Type" = "application/json"
}
$token = (Invoke-RestMethod -Method Post -Uri "$nsxManager/api/v1/login" -Credential $cred).token
$headers["Authorization"] = "Bearer $token"
$response = Invoke-RestMethod -Uri "$nsxManager/policy/api/v1/intelligence/recommendations" -Headers $headers
$response | ConvertTo-Json
Python Example: List All Flow Snapshots
Key Features: