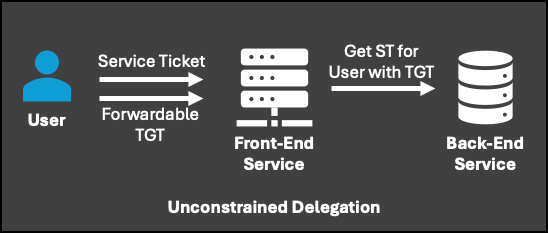
Automatically piecing together an adversary’s full path enables security teams to investigate and respond more swiftly, strengthening security posture and providing better protection for critical assets.
CrowdStrike Achieves AWS AI Competencies
AWS Security Competency — AI Security: CrowdStrike has achieved the AWS Security Competency in the AI Data Security Category, highlighting our expertise in safeguarding AI workloads across critical security environments. This competency recognizes CrowdStrike’s advanced capabilities in ensuring AI data privacy, maintaining AI model integrity and availability, preventing generative AI abuse, and detecting and mitigating AI-specific threats.
Managing EKS security across multiple accounts and regions typically requires separate deployment efforts, reducing agility and time-to-value. CrowdStrike’s built-in solution streamlines deployments with a single, configurable CloudFormation template, simplifying security management and unifying the customer experience by eliminating the complexities of combining separate software and data sources.
New CrowdStrike and AWS Integrations Secure Code Before Deployment
EC2 Image Builder
Falcon Cloud Security is now available as a software component within AWS EC2 Image Builder console, a fully managed service that simplifies the customization, testing, distribution and lifecycle management of Amazon Machine Images (AMIs) and container images. With this integration, customers can seamlessly add Falcon Cloud Security runtime protection to their EC2 Image Builder recipes to create golden images.
Businesses expanding on AWS need security that operates at cloud speed. CrowdStrike uses AWS Built-in multi-account integration to automate deployment and use the cloud’s event-driven architecture. Today, we’re excited to announce we have extended support to Amazon EKS, enabling automatic deployment of Falcon Cloud Security runtime and cluster protection on EKS clusters.
AWS Built-in EKS Support
This feature boosts reliability and reduces maintenance, highlighting CrowdStrike’s commitment to providing trusted solutions that drive security from the very beginning. Identifying risks early can help prevent the deployment of compromised or unsecure images, ensuring consistent protection across all workloads from the moment they are created.
Additionally, Falcon Cloud Security container protection fully supports the newly announced Amazon EKS Auto Mode, which simplifies EKS cluster operations by automating provisioning, scaling and management of cloud infrastructure for Kubernetes applications.
As identity-related threats grow in volume and complexity, Falcon Identity Protection empowers businesses to proactively detect and respond to potential risks, securing permissions and preventing lateral movement attacks to strengthen their AWS security posture.
AWS IAM Identity Center
We are expanding the security coverage of CrowdStrike Falcon® Identity Protection to include AWS IAM Identity Center, extending the existing protection for on-premises Active Directory and cloud identity providers like Entra ID, Ping and Okta. This integration provides organizations with unified visibility and protection across identity providers, including AWS IAM Identity Center users, enabling security teams to efficiently track permissions, monitor authentication patterns, identify high-risk users and consolidate identity data within the CrowdStrike Falcon® platform for simplified compliance and auditing. Read more in this blog post: CrowdStrike Falcon Identity Protection for AWS IAM Identity Center Bolsters AWS Security Posture.
Our attack path analysis supports a host of AWS resources. We continue to grow the number of cloud and identity resources we support for AWS, as well as GCP and Azure, to provide complete visibility. New resources include AWS IAM User, AWS DynamoDB, AWS RDS instance, Azure AD User, Azure Disk, Azure Storage account, GCP IAM role and GCP Cloud Storage.
Enhancing Cloud Detection and Response Across AWS
In response to adversaries’ growing speed, CrowdStrike has introduced innovations to help organizations detect and respond faster in the cloud. Organizations need robust capabilities to detect, investigate and respond to active threats while proactively eliminating weak points and potential attack pathways.
Accelerate Investigations with Complete Visibility
Together, these innovations deliver a unified, proactive approach to protecting cloud environments and providing the full context needed to stay ahead of emerging threats.
This race against the adversary starts with complete visibility into potential attack paths, including visibility from endpoint to cloud to identity. Adversaries can exploit weaknesses in assets along the attack path to move deeper into a target environment and achieve their objectives.
AWS GenAI Competency: CrowdStrike has achieved the AWS Generative AI Competency, distinguishing us as a leader in advancing generative AI solutions that drive innovation and efficiency. This competency reflects CrowdStrike’s expertise in leveraging AWS generative AI tools to build, train, deploy and scale foundational AI models to elevate the security analyst experience.