How Falcon Exposure Management’s ExPRT.AI Predicts What Attackers Will Exploit
ExPRT.AI is trained to rank vulnerabilities based on how likely they are to be exploited in…
ExPRT.AI is trained to rank vulnerabilities based on how likely they are to be exploited in…
An attacker can exploit this vulnerability by crafting a Git repository including a malicious .gitmodules file…
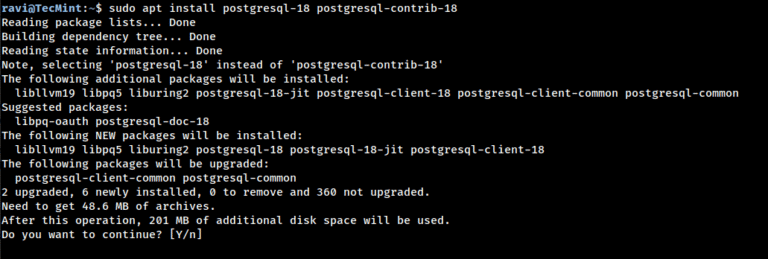
PostgreSQL (Postgres in short) is an open source, powerful, advanced, high-performance, and stable relational-document database system,…
Adversaries move fast, and so must defenders. CrowdStrike is raising the bar for ChromeOS security with…
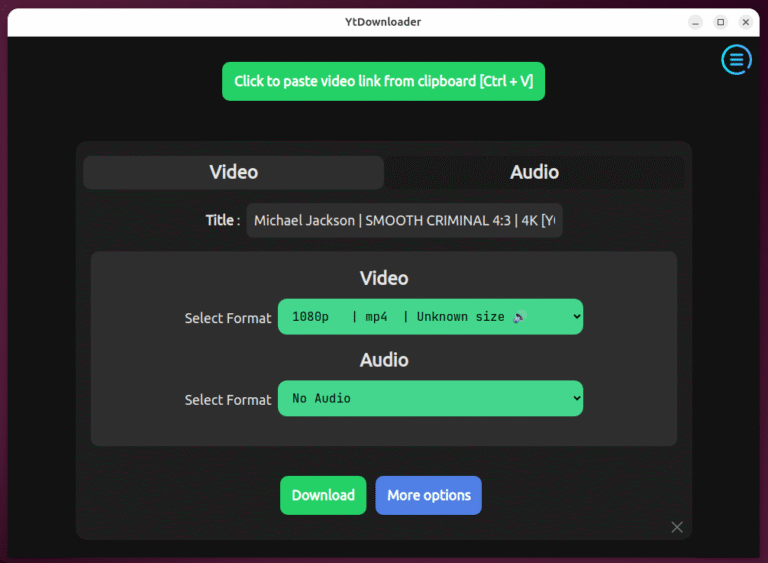
Earlier, I wrote about yt-dlp, the powerful command-line tool for downloading videos from hundreds of websites,…
Unsupported operating systems have historically become adversary targets. The longer a system remains unsupported, the more…

Unauthorized use of RMM tools has become especially dangerous: Throughout 2024, eCrime actors frequently used RMM…
Windows 10 End of Support Is Here There is evidence of active exploitation in the wild…
In Linux and other Unix-like operating systems, the init (initialization) process is the first process executed…
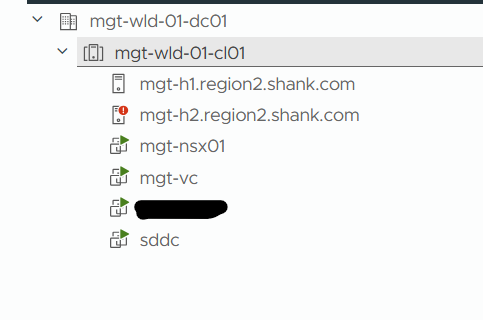
October 13, 2025 VCF 9 Fleet Deployment Task Fails The Issue? As with any failed deployment,…
We believe our placement as a Visionary, coupled with our groundbreaking AI innovations and the acquisition…
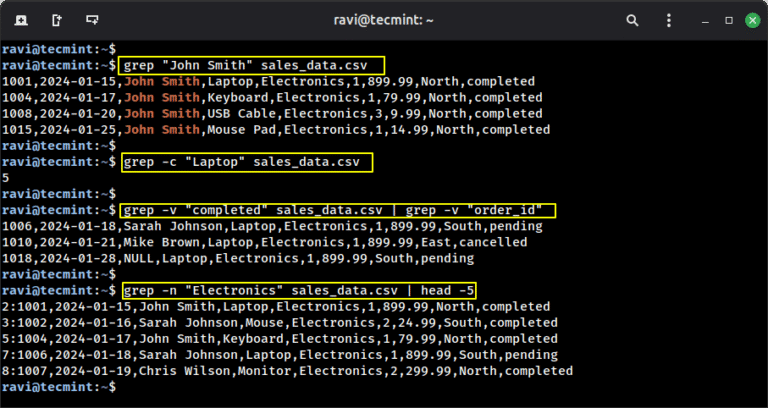
If you’re just starting your journey into data science, you might think it’s all about Python…
GNU Make is a development utility that determines which parts of a particular code base need…
In our previous articles, we’ve covered MySQL interview questions for beginners and intermediate users, and the…

After some investigation, via general log trawling and UI clicking, I found that on each host,…