Essential Docker Commands Guide with Examples (2025)
If you’re looking to get started with Docker, understanding how to work with its command-line interface…
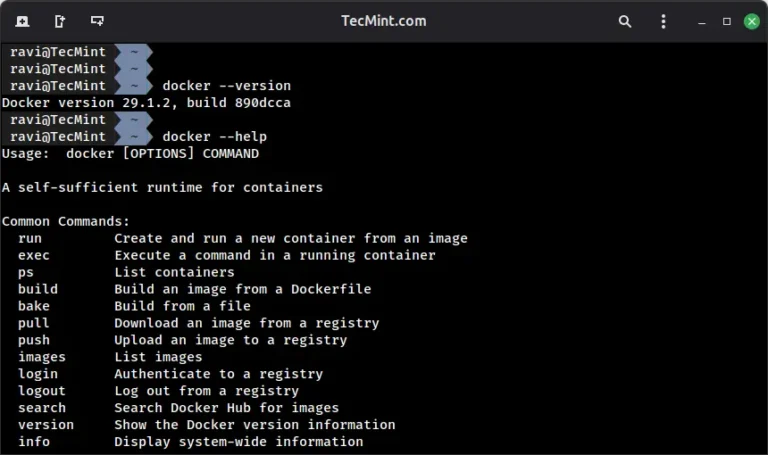
If you’re looking to get started with Docker, understanding how to work with its command-line interface…
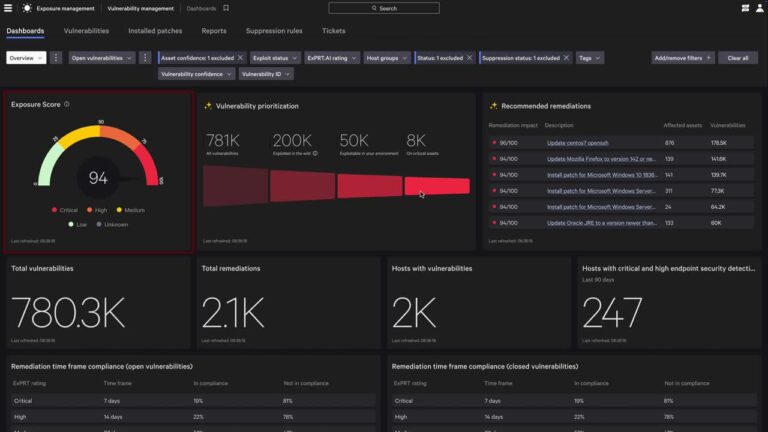
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…

In the MUSTANG PANDA scenario, the adversary embedded encoded shellcode within their malware in an attempt…
Zero-Day Vulnerability in Windows Cloud Files Mini Filter Driver The CrowdStrike Falcon platform regularly collects and…
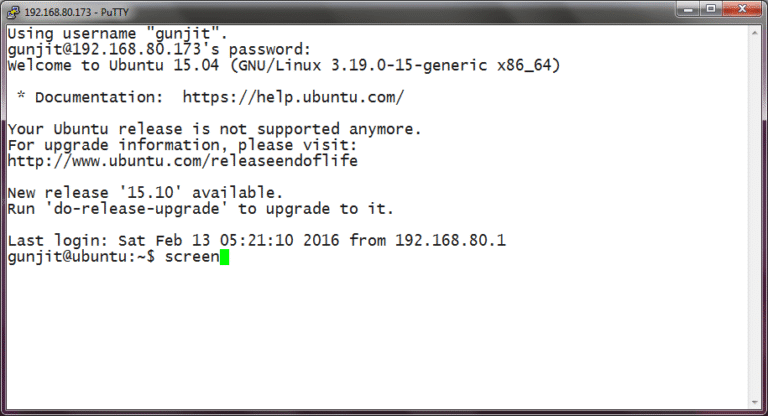
SSH or Secure Shell in simple terms is a way by which a person can remotely…
Why Modern Ecommerce Design Matters for 2026 As we move into 2026, modern ecommerce design is…
Identity has become a key battleground of modern cybersecurity. In 2024, 79% of CrowdStrike detections were…
WARP PANDA demonstrates a high level of stealth and almost certainly focuses on maintaining persistent, long-term,…
There are two basic types of prompt injection attacks: Understanding Prompt Injection Employee BYO AI adoption…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…

When someone visits your website, their browser and your server exchange information back and forth. Without…
CrowdStrike uses NVIDIA Nemotron open models in CrowdStrike Falcon® Fusion SOAR and CrowdStrike Charlotte AI™ AgentWorks….
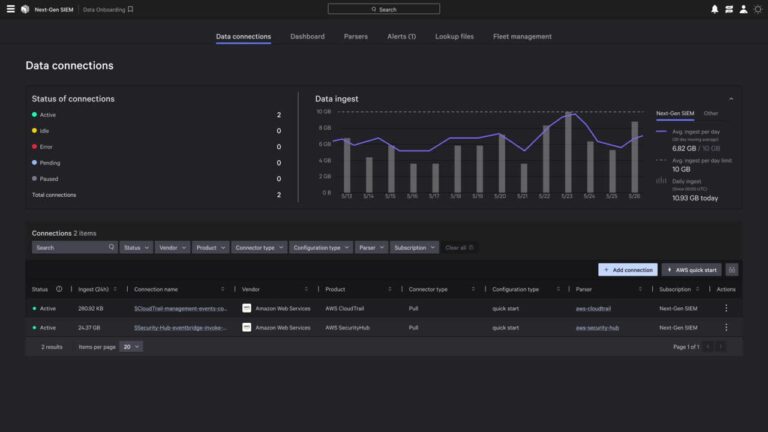
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…
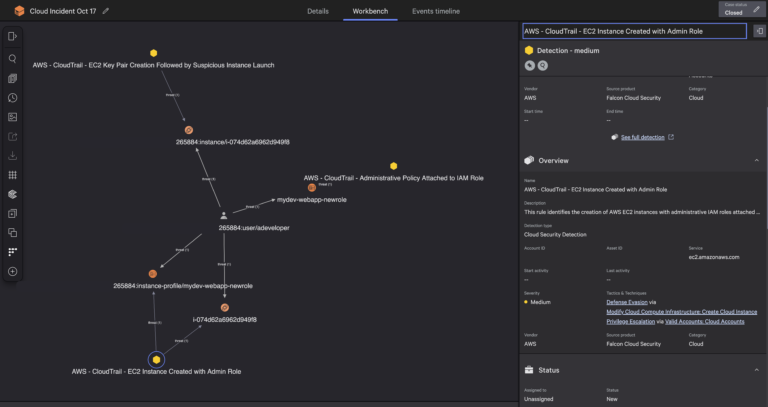
Falcon Cloud Security has implemented a new approach which processes cloud logs as they stream in…