CrowdStrike to Acquire SGNL to Secure Every Identity in the AI Era
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
SGNL provides the runtime access enforcement layer that sits between modern identity providers and the SaaS…
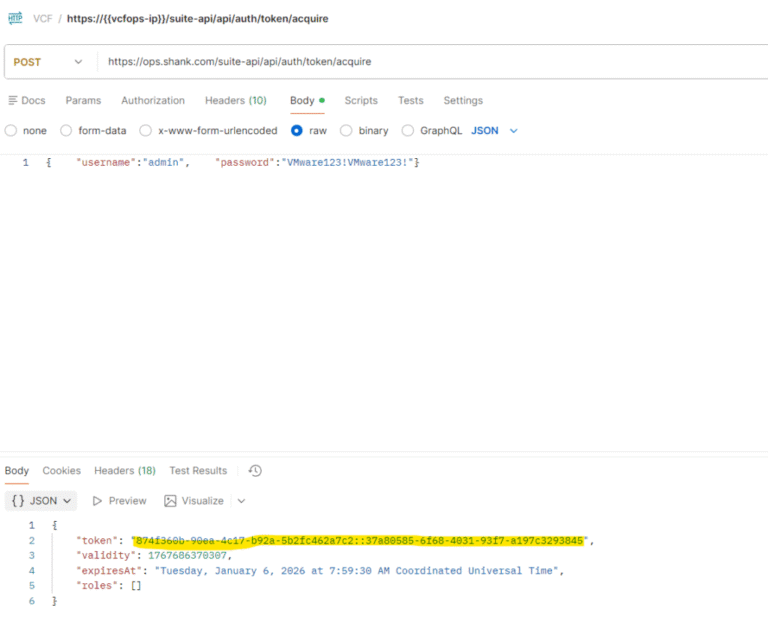
January 7, 2026 Authentication Failure: VCF SSO Broken vCenter vIDB Service Unavailable The Issue? It is…
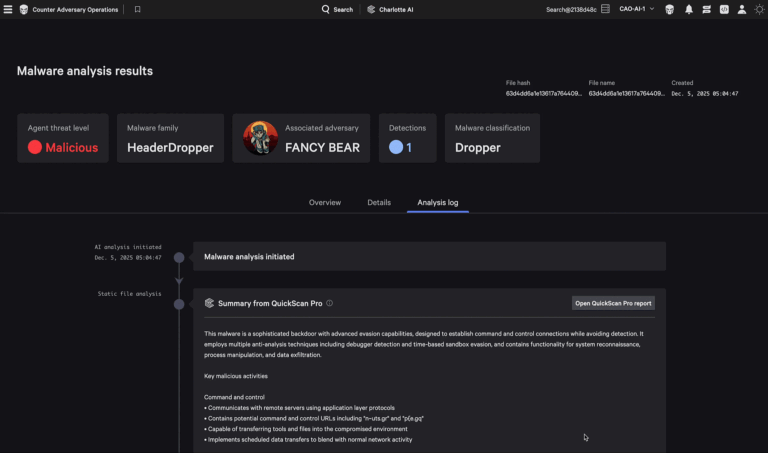
Under the Hood: How It Works Step 3: Dynamic behavioral analysis Step 5: Similar sample identification…
Rather than manually annotating thousands of queries (an expensive and time-consuming process), we leveraged NVIDIA NeMo…
These content packs span multiple categories including application resilience, file discovery, Linux device control, and asset…
In this article, we will go through the various steps to install the constituent packages in…
With the cluster infrastructure in place through the Vertex Training Cluster, we configured Slurm, the industry-standard…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
The AI era is here — and it’s redefining cybersecurity. Organizations around the globe are adopting…
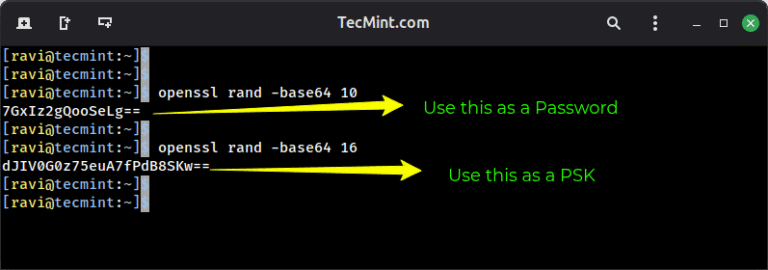
There are so many benefits of using a VPN (Virtual Private Network), some of which include…
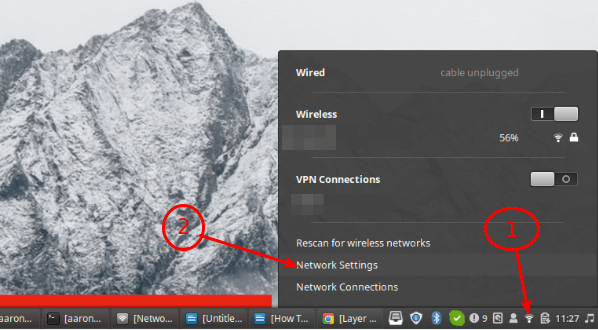
L2TP (which stands for Layer 2 Tunneling Protocol) is a tunneling protocol designed to support virtual…
Organizations are under pressure to protect more devices, users, and distributed workloads than ever — while…
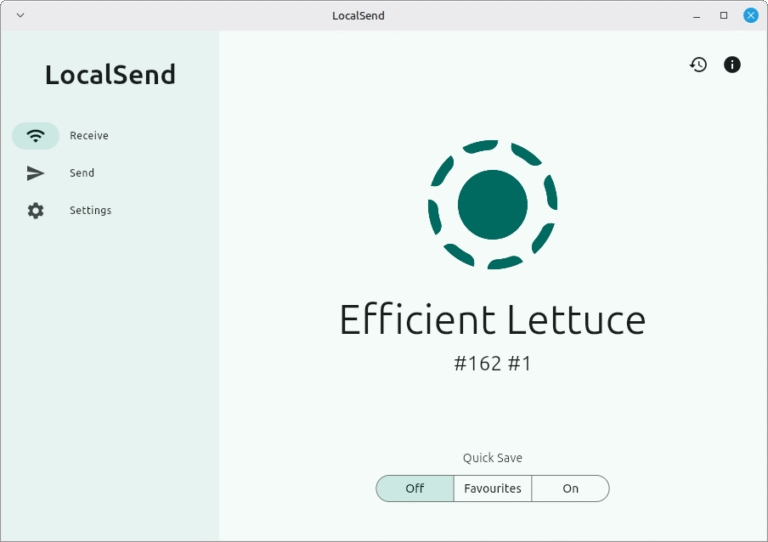
One of the most important uses of a network is for file sharing purposes, and there…
Traditional security tools were never built to protect AI assets across domains or the new AI…
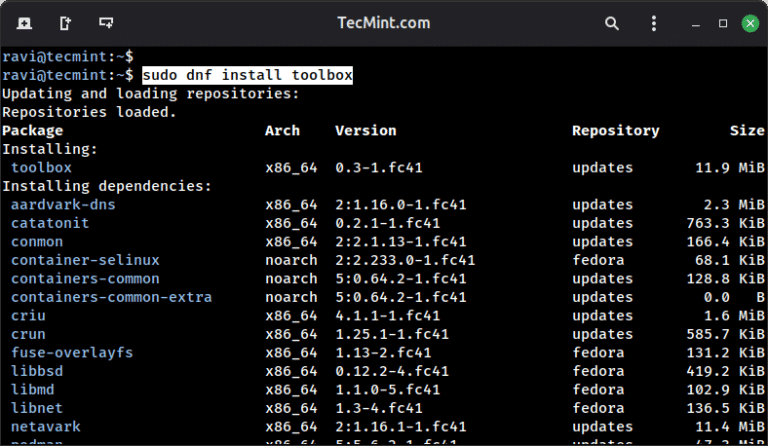
Modern Linux development has moved beyond the traditional approach of installing everything directly on your system….