How to Fix “rm: cannot remove ‘file’: Device or Resource Busy” in Linux
If you’ve ever tried to delete a file or directory in Linux using the rm command…

If you’ve ever tried to delete a file or directory in Linux using the rm command…
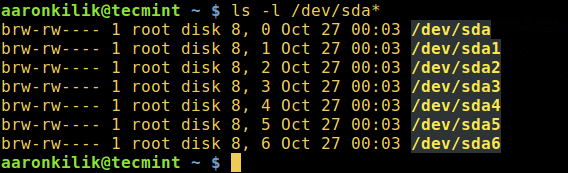
As a newbie, one of the many things you should master in Linux is identifying the…
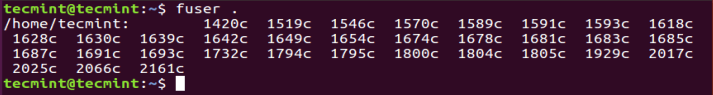
One of the most important tasks in Linux systems administration is process management, which involves several…
Securing cloud environments at runtime is no easy feat. Unlike traditional infrastructure, cloud workloads are dynamic,…
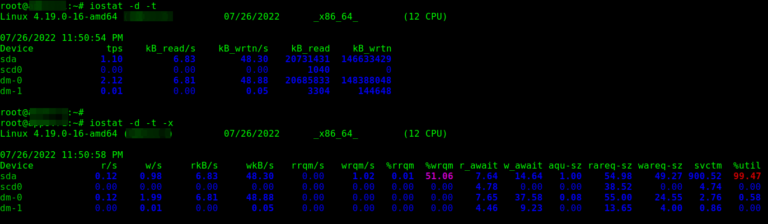
Brief: In this guide, we will discuss the best tools for monitoring and debugging disk I/O…
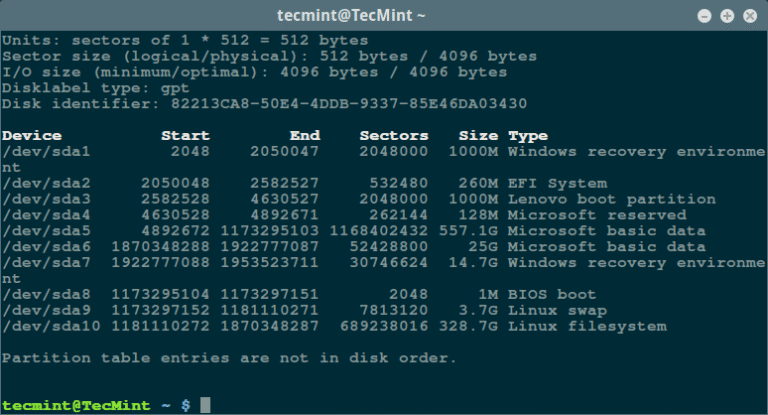
Let’s start by defining a bad sector/bad block, it is a section on a disk drive…
Our Red Teaming AI agent is a guardian of our security’s unseen vulnerabilities. With “instincts” honed…
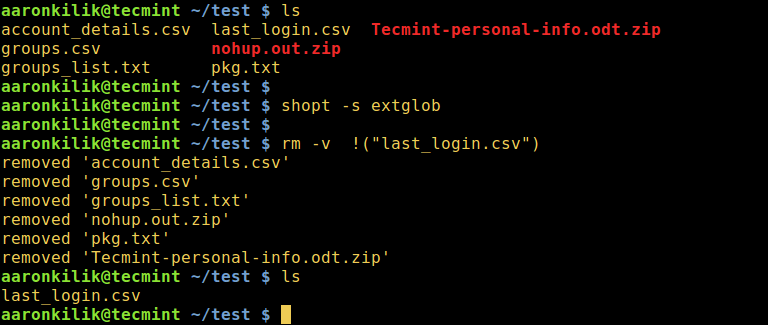
Sometimes, you may find yourself in a situation where you need to delete all files in…
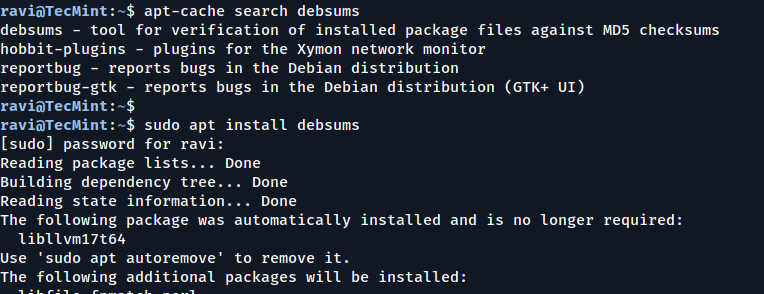
Have you ever wondered why a given binary or package installed on your system does not…
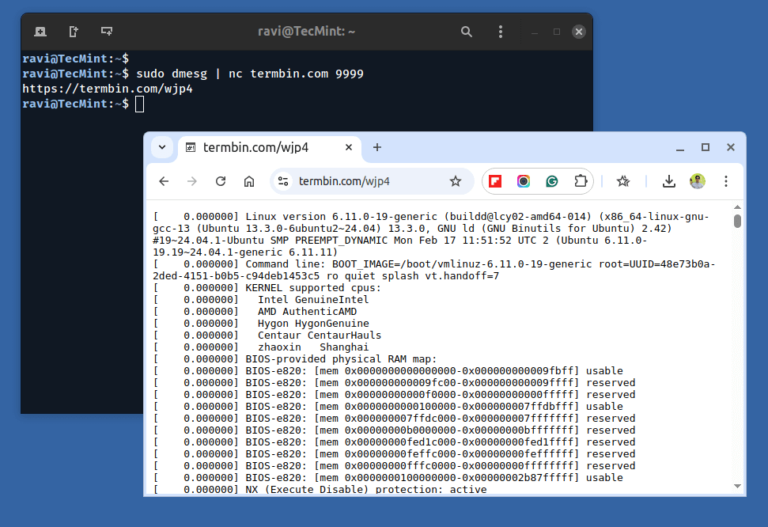
In the world of troubleshooting and collaborative debugging, sharing command-line output and error logs is an…
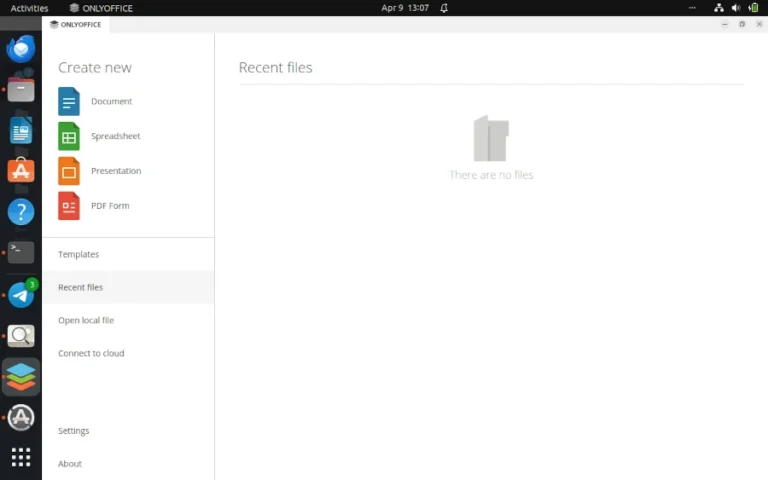
If you want to edit your documents, spreadsheets, and presentations using an AI model locally deployed…
In 2025, consumers trust influencers’ recommendations almost as much as they trust friends and family, making…
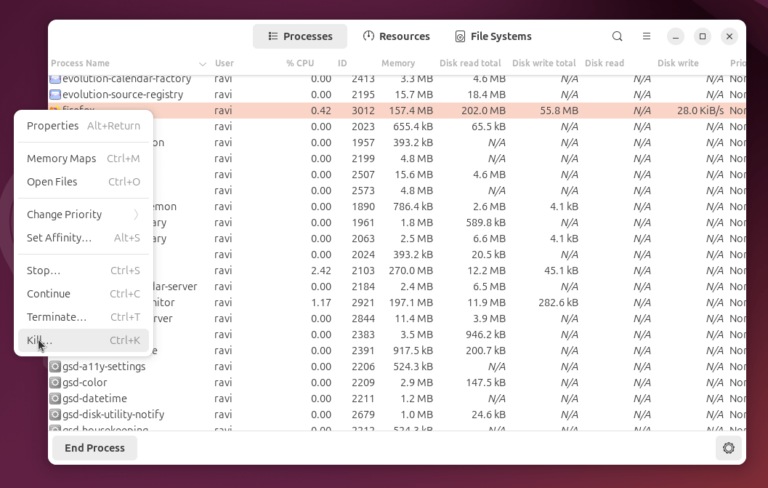
When your Ubuntu system suddenly freezes, it can be very frustrating, especially if you’re working on…
Strong cloud security is critical amid the accelerated adoption of cloud infrastructure and rapid pace of…
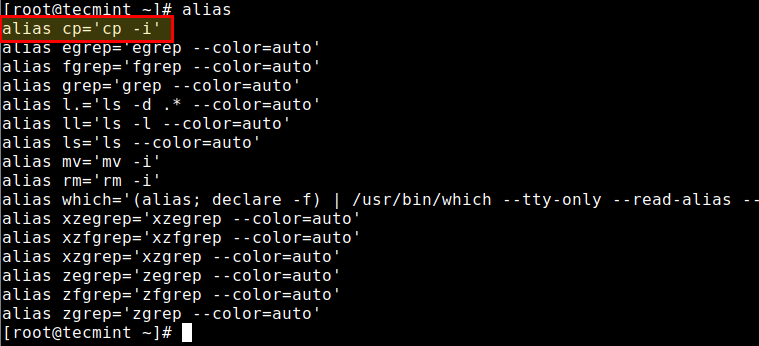
The cp command (short for copy) is one of the most commonly used commands in Linux…