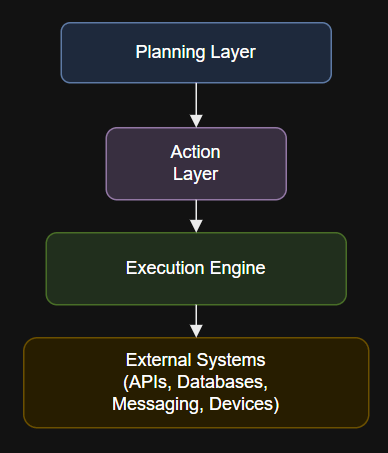
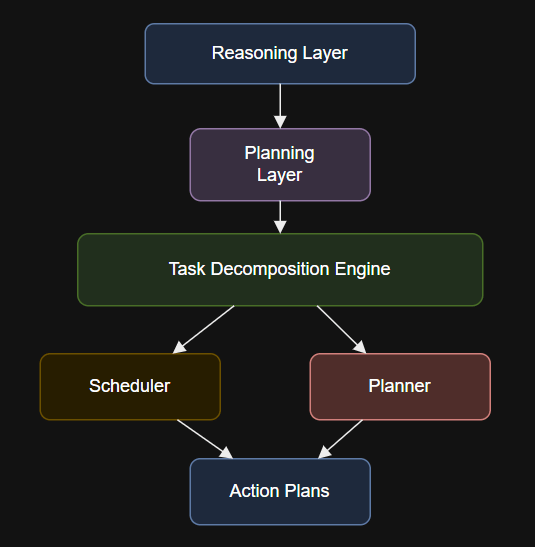
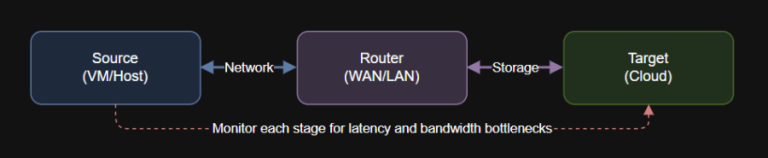
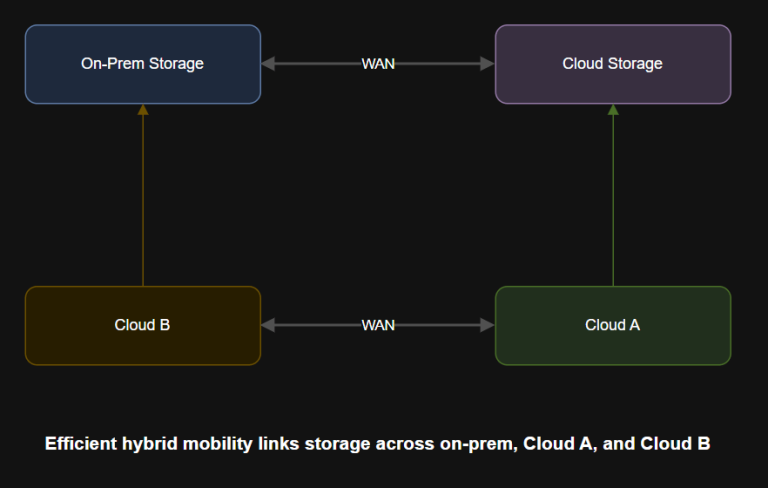
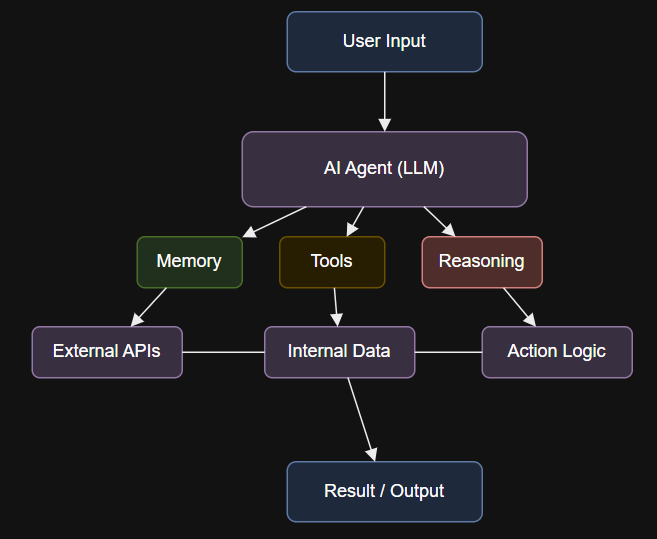
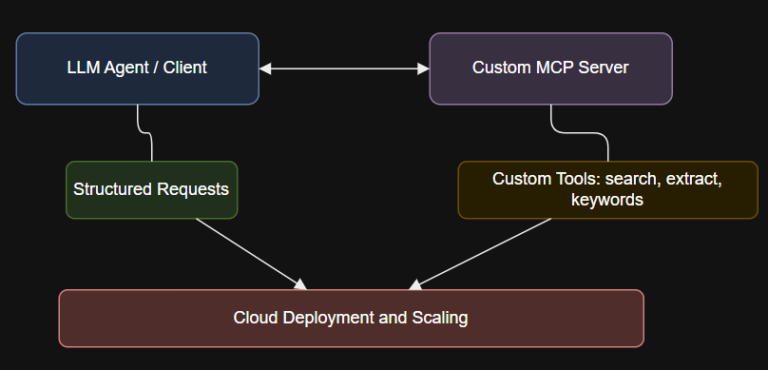
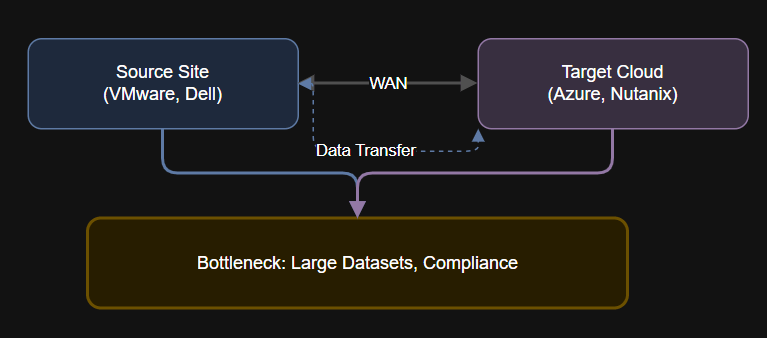
7 layers of agentic AI – Action Layer
Introduction @app.task(bind=True, max_retries=3)def execute_api_action(self, endpoint, payload):try:response = requests.post(endpoint, json=payload, timeout=10)response.raise_for_status()return {“status”: “success”, “response”: response.json()}except Exception as…