Introduction
resource legacyDns 'Microsoft.Network/privateDnsZones@2020-06-01' = {
name: 'legacy.local'
location: 'global'
}Diagram:
- Hard-coded static IPs
- Manual DNS or HOSTS file entries
- Application-layer dependencies on specific ports
- Rigid firewall rules
- Lack of support for dynamic addressing or name resolution
# Allow TCP 1433 for SQL legacy app
New-AzLocalNetworkSecurityRuleConfig -Name "AllowSQL1433" -Protocol "Tcp" -Direction "Inbound" -Priority 100 `
-SourceAddressPrefix "*" -SourcePortRange "*" -DestinationAddressPrefix "*" -DestinationPortRange "1433" -Access "Allow"
B. Port Forwarding via SDN Load Balancer
Modernizing legacy workloads with Azure Local SDN demands creative workarounds, automation, and careful planning. By leveraging SDN IP reservations, NAT overlays, custom DNS, and explicit port handling, network architects and sysadmins can shape robust, cloud-aligned networks even for the most stubborn legacy applications. These approaches reduce risk, streamline migrations, and set the foundation for future cloud-native evolution.
Solutions
A. Preserving Original IPs in Azure Local SDN
#image_title
PowerShell Example:
PowerShell Example:
PowerShell Example:
PowerShell Example:
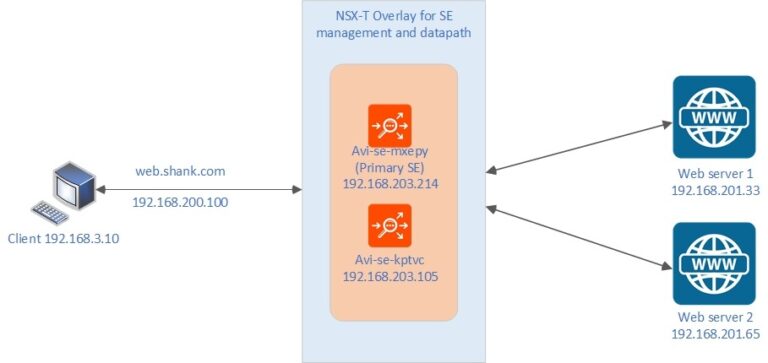
Diagram:
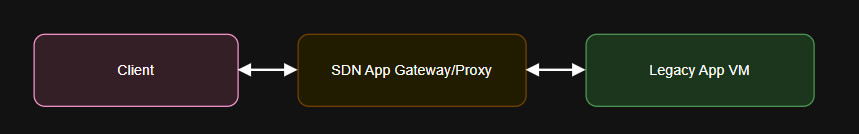
5. Automating Workarounds with PowerShell, Bicep, and JSON
- Use ARM/Bicep templates to create SDN subnets, NSGs, and static IP pools matching legacy needs.
- Automate host file, DNS, and firewall rule injection via PowerShell DSC or VM extensions.
- Leverage SDN APIs for bulk changes.
Define explicit NSG rules to allow only the required legacy ports.
$vmList = Get-AzVM -ResourceGroupName "LegacyRG"
foreach ($vm in $vmList) {
Invoke-AzVMRunCommand -ResourceGroupName $vm.ResourceGroupName -VMName $vm.Name -CommandId 'RunPowerShellScript' -ScriptPath 'Update-Hosts.ps1'
}
Disclaimer: The views expressed in this article are those of the author and do not represent the opinions of Microsoft, my employer or any affiliated organization. Always refer to the official Microsoft documentation before production deployment.
- Reserved those same IPs in Azure Local SDN’s static IP pools
- Used PowerShell scripts to automate reservation and network attachment
- Updated DNS and firewall rules to map to SDN-assigned resources
Post-Migration:
Case Study 2: Manufacturing Plant App With Legacy Port Dependencies
Post-Migration:
7. Comparison Table: Legacy vs SDN Approaches
| Challenge | Legacy On-Prem Solution | Azure Local SDN Solution |
|---|---|---|
| Hard-coded IPs | Manual static IP | IP reservation, NAT overlays |
| Static DNS | HOSTS file or static server | Private DNS zones, host file injection |
| Static ports | Manual firewall, open port | NSG, SLB, App Gateway rules |
| Rigid config | Siloed network, manual management | Automated policy, scripted enforcement |
| Change resistance | Manual edits, high outage risk | Automated scripts, minimal downtime |
8. Checklists for Migration
# Reserve a specific IP for a VM NIC
$ipPool = Get-SdnIpPool -Name "LegacySubnet"
$staticIP = "10.10.10.50"
Add-SdnIpReservation -IpPool $ipPool -IpAddress $staticIP -ResourceId "/subscriptions/xxxx/resourceGroups/LegacyRG/providers/Microsoft.Network/virtualNetworks/LegacyVNet"
B. Network Address Translation (NAT) Overlays
#image_title
- Script IP reservations in Azure Local SDN
- Implement custom DNS solutions as needed
- Create NSG/SLB rules for static ports
{
"name": "legacyStaticRoute",
"properties": {
"addressPrefix": "10.10.10.50/32",
"nextHopType": "VirtualAppliance",
"nextHopIpAddress": "10.1.2.5"
}
}
3. DNS Workarounds for Non-Compliant Applications
Challenge
Applications reference fixed IP addresses, either in code, configuration, or third-party integrations.
PowerShell Example: