Table of Contents
- Overview
- East-West vs. North-South: Key Traffic Patterns
- NSX-T 4.x Architecture Explained
- Traffic Flow Diagrams
- Real-World Production Use Cases
- Traffic Path Deep Dives
- East-West Flow
- North-South Flow
- Best Practices for Design and Operations
- Troubleshooting Framework for NSX-T Traffic
- PowerShell & Python: Traffic Tracing and Automation
- Summary: Takeaways for Network Pros
Overview
Previous in the NSX-T Series:
Dynamic Groups and Tagging in NSX-T: Policy-Driven Network Security
Explore how dynamic groups and tagging drive microsegmentation and security automation in NSX-T. Includes YAML policy templates, Python automation, and real-world tagging strategies.
East-West vs. North-South: Key Traffic Patterns
- East-West Traffic:
Stays within the datacenter (for example, VM-to-VM, service-to-service). - North-South Traffic:
Enters or exits the virtual data center—connecting workloads to external users, clouds, or the internet.
| Traffic Type | Example | Scope |
|---|---|---|
| East-West | App server → DB server | Internal |
| North-South | User’s laptop → Web VM | External/Internal |
NSX-T 4.x Architecture Explained
- NSX Manager: Centralized API and management.
- Transport Nodes: ESXi/KVM hosts running NSX agents.
- Edge Nodes: North-south gateways.
- Tier-0 / Tier-1 Gateways: Routing boundaries.
- Distributed Firewall (DFW): Policy at every VNIC.
VMware NSX-T 4.x redefines data center networking. To secure, monitor, and automate at scale, engineers must understand the distinct paths of east-west (internal) and north-south (datacenter ingress/egress) traffic. This article delivers deep technical detail, production-proven advice, and fully-importable network diagrams—plus PowerShell and Python code for live traffic tracing.
- East-west: Routed/firewalled on the host, never hairpins to an edge node.
- North-south: Routed through Tier-0 on an Edge Node—applies NAT, firewall, advanced services.
Traffic Flow Diagrams
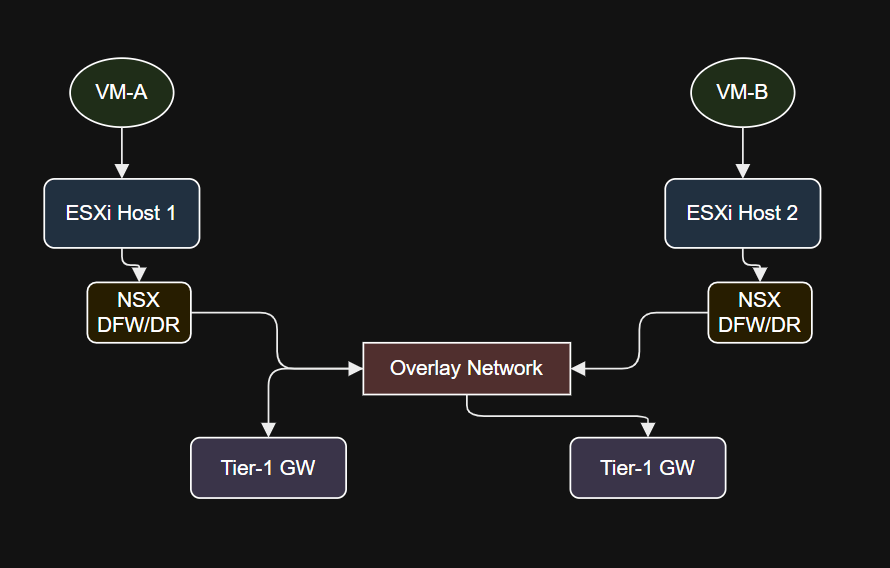
East-West Traffic
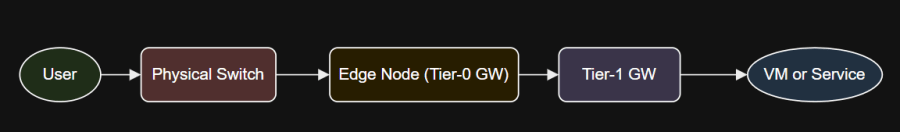
North-South Traffic
Real-World Production Use Cases
Enterprise Application Segmentation
- East-West: Microsegmentation for regulatory compliance, lateral movement prevention.
- North-South: NAT, DDoS, and public API access via Tier-0.
Multi-Tenant Cloud Services
- East-West: Tenant isolation with L2/L3 overlays and dynamic groups.
- North-South: Edge isolation, internet control per tenant.
Hybrid Cloud Extension
- East-West: NSX-T to NSX Cloud for seamless mobility.
- North-South: Secure egress, VPN, or Direct Connect at Tier-0.
Traffic Path Deep Dives
East-West Traffic: Deep Dive
- Example: VM-A (10.10.1.10, Host-1) → VM-B (10.10.2.20, Host-2), both on overlay segments.
- Flow:
- VM-A sends packet.
- DFW (egress) applies policy.
- DR routes locally.
- GENEVE overlay encapsulation to Host-2.
- DFW/DR on Host-2 applies, packet to VM-B.
North-South Traffic: Deep Dive
- Example: VM-C (192.168.10.5) to internet.
- Flow:
- DFW on VM-C (egress).
- Routed up to Tier-1, then to Tier-0 Edge Node.
- NAT/firewall as needed at Tier-0.
- Exits to physical network.
Best Practices for Design and Operations
- Microsegmentation: Enforce DFW on all internal flows, not just perimeters.
- Gateway Tiering: Tier-0 for north-south, Tier-1 for distributed east-west and service chains.
- Avoid Hairpinning: Use distributed routing.
- Edge Cluster Sizing: Right-size for external throughput.
- Full Telemetry: Enable Traceflow and flow monitoring.
Troubleshooting Framework for NSX-T Traffic
- Symptom Analysis:
- Flow logs, firewall counters, topology validation.
- Logical Validation:
- Segments/VLANs, Tier-1/Tier-0 status.
- DFW & Edge Policy Checks:
- Rule hit counts, NAT, route tables.
- Tool Leverage:
- GUI: Flow monitoring, DFW logs.
- CLI:
get logical-routers get logical-router <UUID> route-table
- Packet Tracing:
- Traceflow and port mirroring.
PowerShell & Python: Traffic Tracing and Automation
PowerShell Example: East-West Connectivity
Disclaimer: The views expressed in this article are those of the author and do not represent the opinions of VMwware, my employer or any affiliated organization. Always refer to the official VMWare documentation before production deployment.
Python Example: North-South Path Trace
import requests
from requests.auth import HTTPBasicAuth$SourceVM = "VM-A"
$DestIP = "10.10.2.20"
Test-Connection -ComputerName $DestIP -Count 4url = f"https://{nsx_manager}/api/v1/logical-routers"
resp = requests.get(url, auth=HTTPBasicAuth(username, password), verify=False)
for lr in resp.json().get('results', []):
if lr['router_type'] == 'TIER0':
print(f"Tier-0: {lr['display_name']}")
rt_url = f"https://{nsx_manager}/api/v1/logical-routers/{lr['id']}/routing-table"
rt_resp = requests.get(rt_url, auth=HTTPBasicAuth(username, password), verify=False)
print(rt_resp.json())
Traffic Handling: