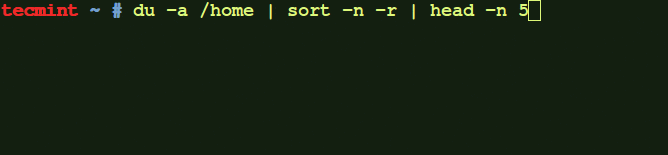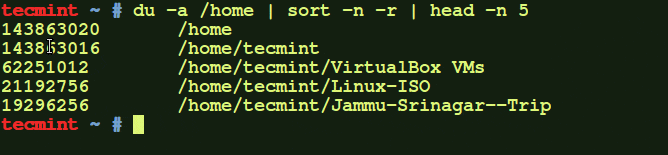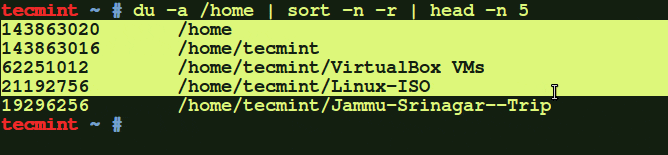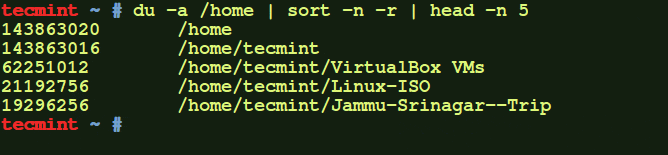
Figure 2. Monitor the movement of data through web applications to protect your sensitive data
CrowdStrike Falcon enhances data security with its advanced encryption capabilities. It ensures that data, whether at rest or in transit, remains encrypted and secure. Falcon’s encryption management integrates seamlessly with Google Cloud’s native encryption services.
Implementing continuous monitoring helps prioritize risks by identifying and mitigating the most significant threats, strengthening the overall security posture of your cloud environment.
1. Implement Strong Identity and Access Management
CrowdStrike Falcon integrates with Google Cloud IAM to provide real-time monitoring and alerts on suspicious activities. Its AI-driven insights help quickly identify and mitigate IAM-related risks.
Cloud network segmentation is a strategy that partitions a cloud environment into smaller, isolated zones, each with its own security policies, controls and access rights based on resource sensitivity, criticality and access needs. This approach helps organizations minimize the attack surface and enhances security.
- Principle of least privilege (POLP): Grant users the minimum level of access necessary for their roles. Periodic evaluations should be planned to reduce access levels when they are no longer necessary.
- Multi Factor authentication (MFA): Best MFA practices add an extra layer of security. Implement session time limits, enforce robust password policies and require regular password changes. Verify that MFA connections originate from a trusted source or IP range.
- Regular audits: Conduct periodic reviews of IAM policies and permissions to detect and correct anomalies.
CrowdStrike Falcon integration:
Google Cloud’s BeyondCorp shifts access controls from the network perimeter to individual users, enabling secure work from virtually any location without a traditional VPN. It integrates with Falcon Zero Trust Assessment, allowing joint customers to create and enforce granular access policies to applications using CrowdStrike’s unique risk signals. The integration enables seamless sharing of telemetry and data between the two security platforms, helping maintain the highest levels of security across a customer’s entire cloud or hybrid environment.
Google Cloud’s BeyondCorp shifts access controls from the network perimeter to individual users, enabling secure work from virtually any location without a traditional VPN. It integrates with Falcon Zero Trust Assessment, allowing joint customers to create and enforce granular access policies to applications using CrowdStrike’s unique risk signals. The integration enables seamless sharing of telemetry and data between the two security platforms, helping maintain the highest levels of security across a customer’s entire cloud or hybrid environment.
Google Cloud’s BeyondCorp shifts access controls from the network perimeter to individual users, enabling secure work from virtually any location without a traditional VPN. It integrates with Falcon Zero Trust Assessment, allowing joint customers to create and enforce granular access policies to applications using CrowdStrike’s unique risk signals. The integration enables seamless sharing of telemetry and data between the two security platforms, helping maintain the highest levels of security across a customer’s entire cloud or hybrid environment.
Google Cloud’s BeyondCorp shifts access controls from the network perimeter to individual users, enabling secure work from virtually any location without a traditional VPN. It integrates with Falcon Zero Trust Assessment, allowing joint customers to create and enforce granular access policies to applications using CrowdStrike’s unique risk signals. The integration enables seamless sharing of telemetry and data between the two security platforms, helping maintain the highest levels of security across a customer’s entire cloud or hybrid environment.
CrowdStrike Falcon integration:
Falcon Cloud Security: The Natural Fit for Google Cloud Users
Key benefits of CrowdStrike Falcon:
Figure 3. Simplify cloud security with a centralized view of risky misconfigurations
- Seamless integration: Easily integrates with Google Cloud services.
- AI-driven threat detection: Leverages artificial intelligence to detect and respond to threats in real time.
- Comprehensive protection: Offers end-to-end security, from IAM and network security to data encryption and compliance.
Key strategies include: