VCF 9.0 GA Mental Model Part 6: Topology and Identity Boundaries for Single Site, Dual Site, and Multi-Region
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
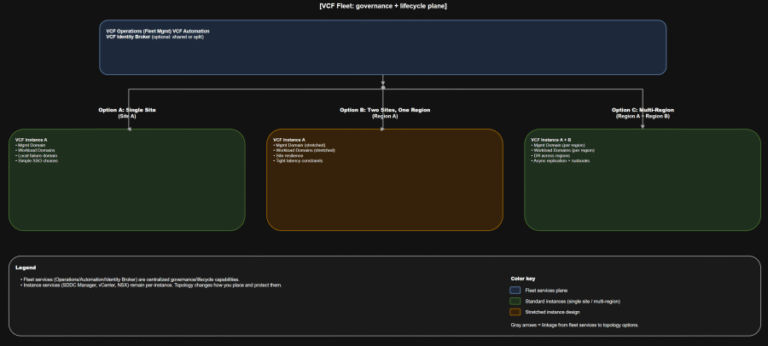
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
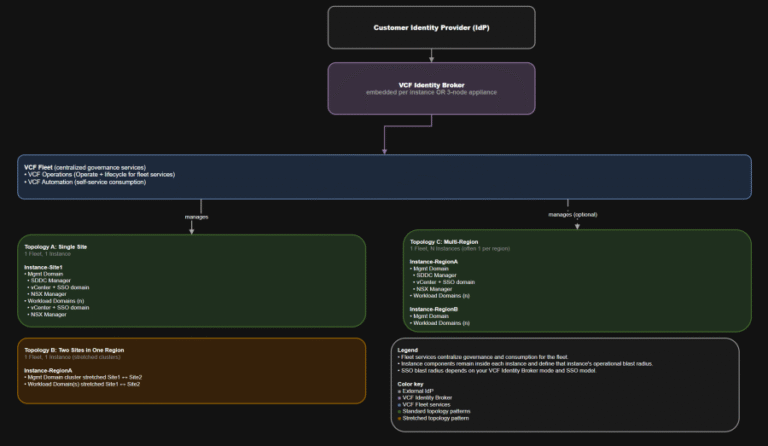
TL;DR This post targets VCF 9.0 GA only: VCF 9.0 (17 JUN 2025) build 24755599, with…
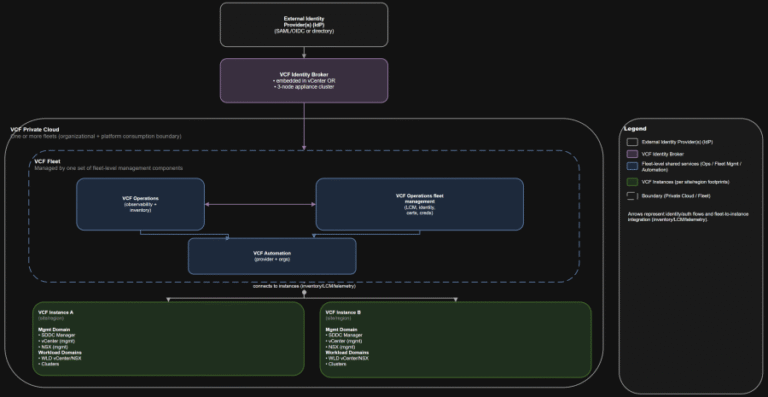
TL;DR Practical implication: if fleet services are impaired, governance and workflows degrade, but the instance-level control…
Indirect prompt injection significantly amplifies this risk by allowing adversaries to influence OpenClaw’s behavior through data…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
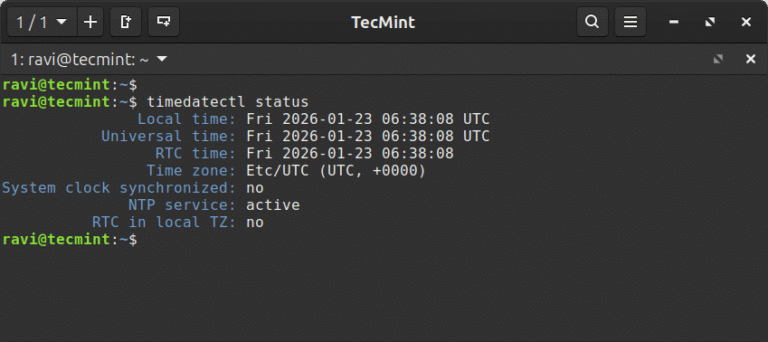
In this article, learn how to set time, timezone, and synchronize your Linux system clock with…
Types of AI Tool Poisoning Attacks Consider a scenario where an attacker publishes a tool with…
Rather than manually annotating thousands of queries (an expensive and time-consuming process), we leveraged NVIDIA NeMo…
With the cluster infrastructure in place through the Vertex Training Cluster, we configured Slurm, the industry-standard…
There are two basic types of prompt injection attacks: Understanding Prompt Injection Employee BYO AI adoption…

When someone visits your website, their browser and your server exchange information back and forth. Without…
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…

The “404 Not Found” error during upgrade occurs when your system attempts to download packages from…
While these agents can expedite individual tasks, their ultimate potential is realized when they operate in…