VCF 9.0 GA Mental Model Part 6: Topology and Identity Boundaries for Single Site, Dual Site, and Multi-Region
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
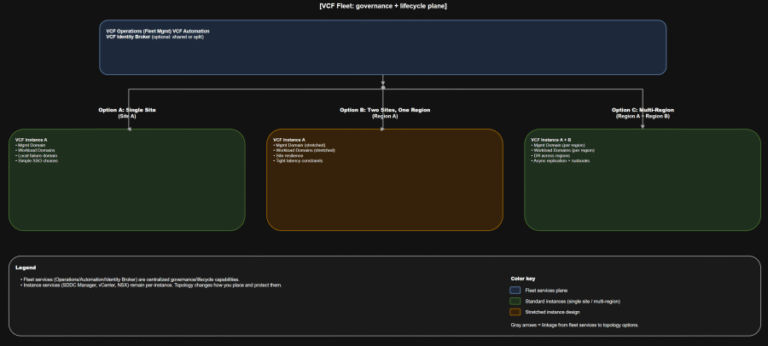
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
As an example, consider a legitimate send_email tool that’s been thoroughly reviewed. An attacker publishes a…
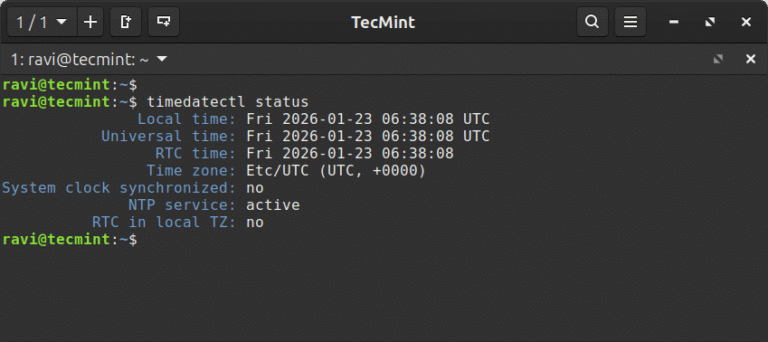
In this article, learn how to set time, timezone, and synchronize your Linux system clock with…
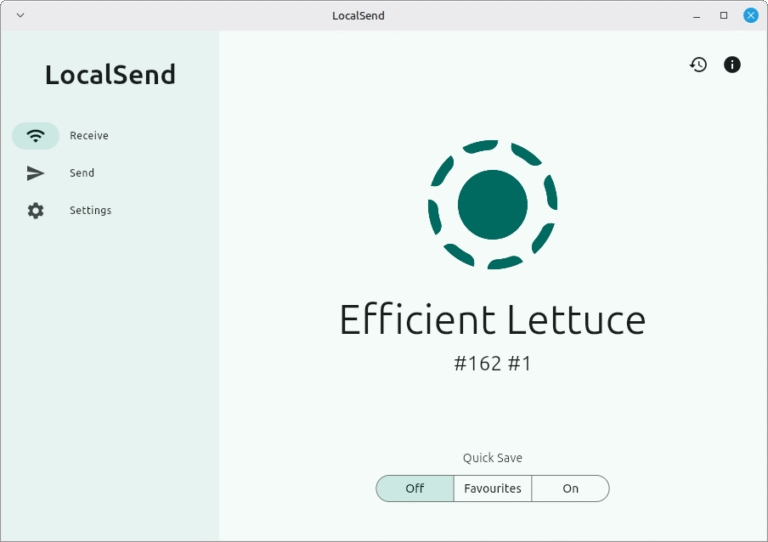
One of the most important uses of a network is for file sharing purposes, and there…
WARP PANDA demonstrates a high level of stealth and almost certainly focuses on maintaining persistent, long-term,…
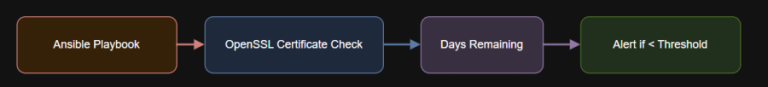
Introduction – name: Convert expiry date to epochset_fact:cert_expiry_date: “{{ cert_expiry_raw.stdout | trim }}”cert_expiry_epoch: “{{ cert_expiry_date |…