How to Automate Daily Linux Health Checks with a Bash Script + Cron
Managing Linux servers daily can be fun and stressful, especially when you’re dealing with unexpected downtimes…
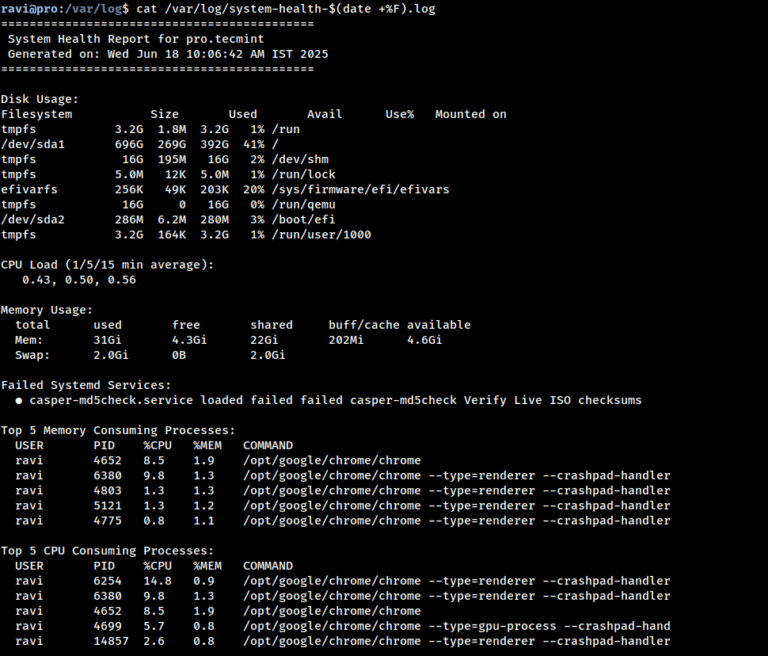
Managing Linux servers daily can be fun and stressful, especially when you’re dealing with unexpected downtimes…
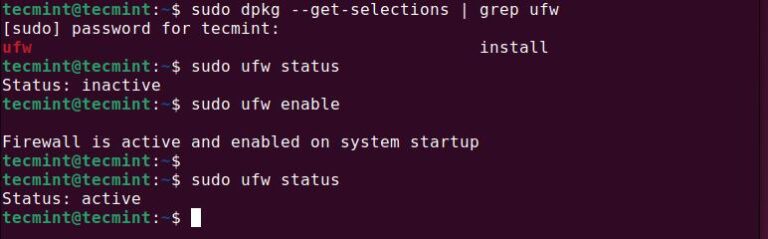
Since computers are connected to each other, services are growing rapidly, with examples such as email,…
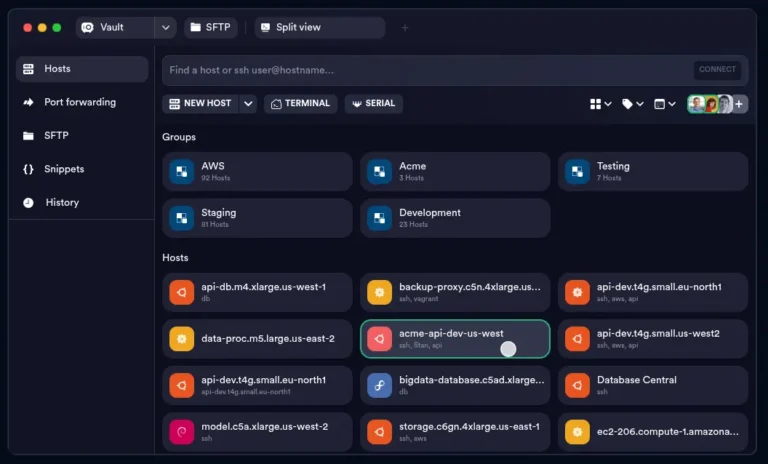
If you’re a Linux user, managing remote servers or networked devices via SSH (Secure Shell) is…

When setting up an Ubuntu server for production, securing the system is crucial to ensure its…
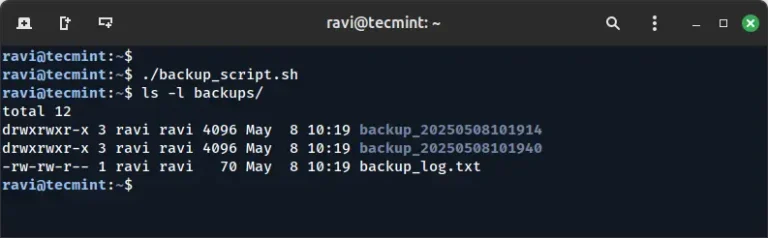
On a Linux system, having regular backups is critical to protect your data, keep it safe,…
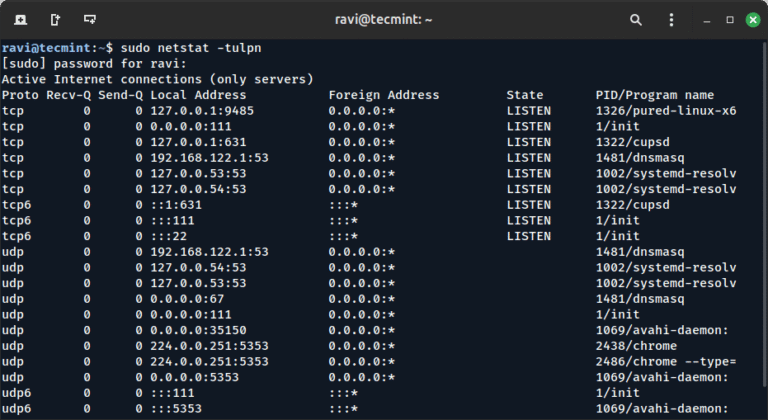
If you’re preparing for a networking, Linux system administration, DevOps, or cybersecurity interview, understanding network ports…
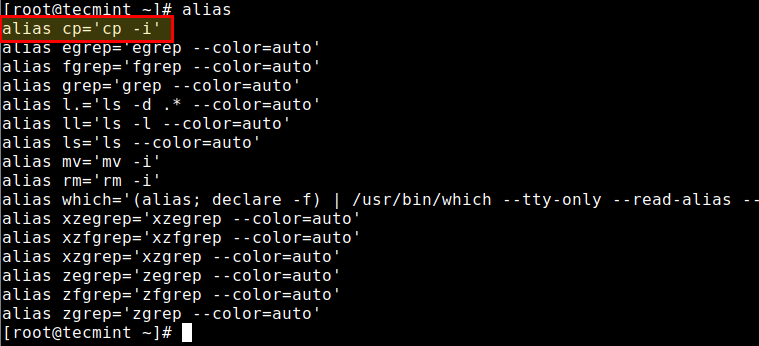
The cp command (short for copy) is one of the most commonly used commands in Linux…
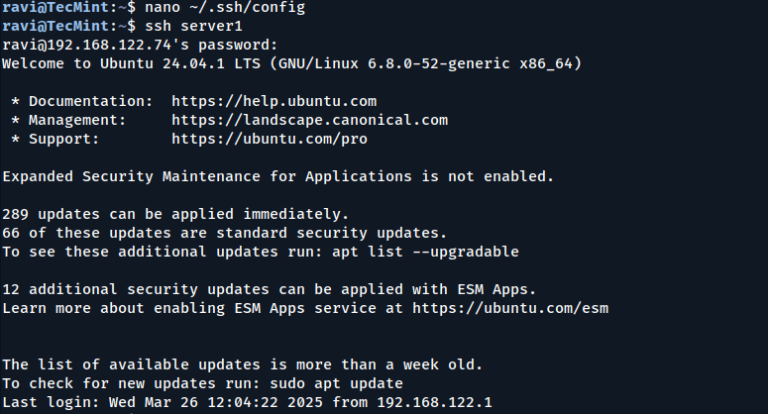
If you use Linux or manage remote servers (like cloud servers on AWS, DigitalOcean, or even…
1. Initial Entry and Exploitation After gaining initial access, the adversary moved laterally through the network…

Linux is a powerful and reliable operating system, but even seasoned users encounter unexpected problems. Whether…
Adversaries may tamper with organizations’ infrastructure to facilitate data exfiltration. Some examples include:It is essential to…
Setting up your first Linux server might feel overwhelming at first, especially if you’re new to…

Synchronizing files between Linux and Windows can seem challenging, especially if you’re not familiar with the…

When managing a web server, it’s crucial to ensure that your data is safe and can…

Linux is the backbone of many machine learning (ML) workflows. With its powerful command-line interface, Linux…