How to Enable AI Agents in ONLYOFFICE Desktop Editors on Linux
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
In this article, you will discover the best software tools powered by AI that you can…
In this guide, we feature some of the best Linux distributions that you can install on…
Christoph Bausewein is Assistant General Counsel for Data Protection and Policy at CrowdStrike.This creates a new…
Precise device access: Security teams can allow, restrict, or block removable media based on device attributes,…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…
Organizations are under pressure to protect more devices, users, and distributed workloads than ever — while…
Traditional security tools were never built to protect AI assets across domains or the new AI…
Consider document processing scenarios: An employee asks an AI to summarize a quarterly report, not realizing…

Apple iWork is Apple’s suite of office applications, similar to Microsoft Office or Google Docs, consisting…
Despite the revolutionary agentic delivery mechanism used to achieve groundbreaking speed and scale in this attack,…
Gone are the days when Skype was the go-to VoIP tool for every chat, call, or…
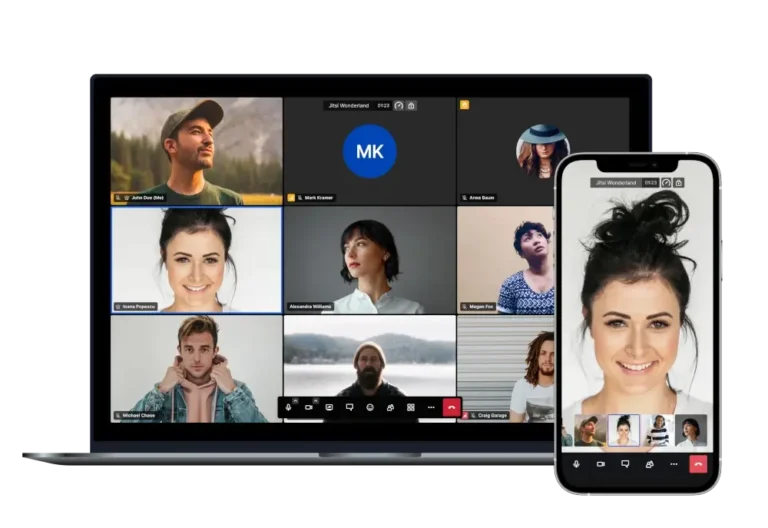
There’s no doubt that Skype was once one of the most popular instant messaging and video…
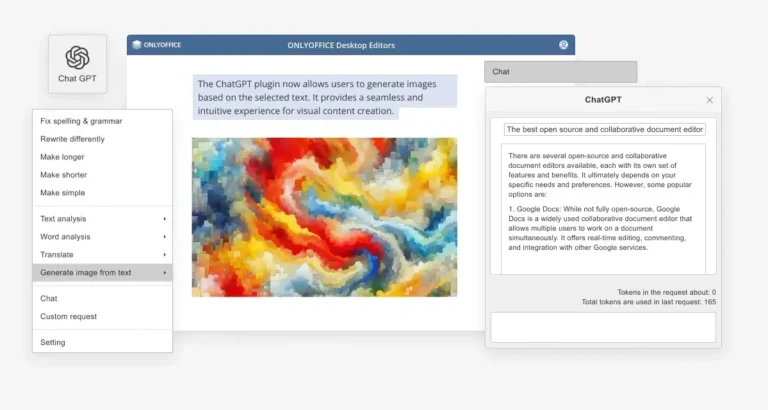
Linux is an open-source operating system whose use is increasing these days as a result of…
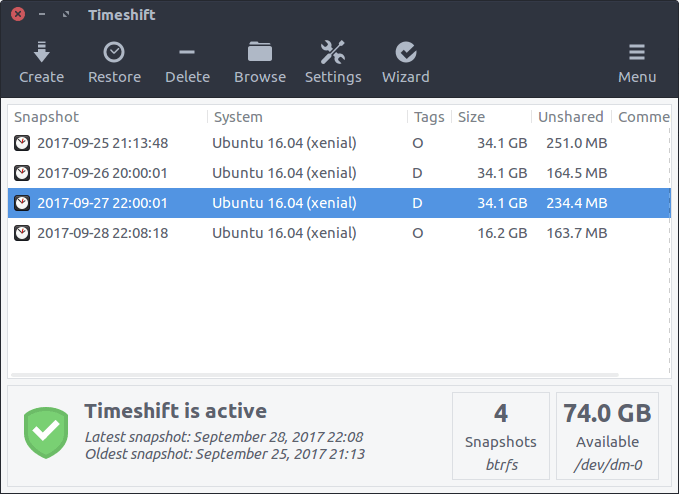
It isn’t easy to figure out which of the many Linux apps out there are actually…