VCF 9.0 GA Mental Model Part 6: Topology and Identity Boundaries for Single Site, Dual Site, and Multi-Region
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
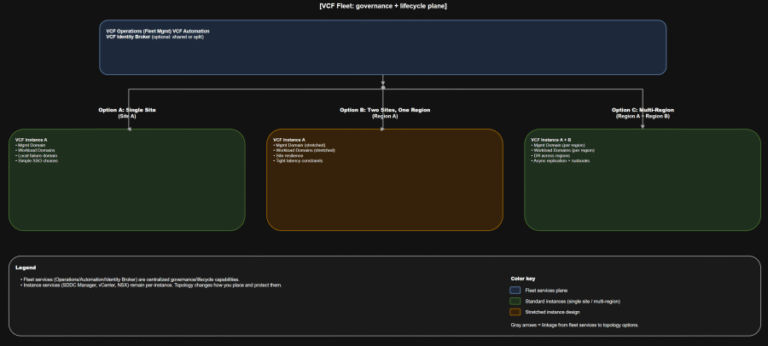
TL;DR Scope: VMware Cloud Foundation 9.0.0.0 GA (primary platform build 24703748) and the associated 9.0 GA…
CrowdStrike Falcon Identity Protection — A Great Tool to Gain Visibility We remain committed to innovating…
GOLDEN CHOLLIMA Shared infrastructure elements and tool cross-pollination indicate these units maintain close coordination. All three…
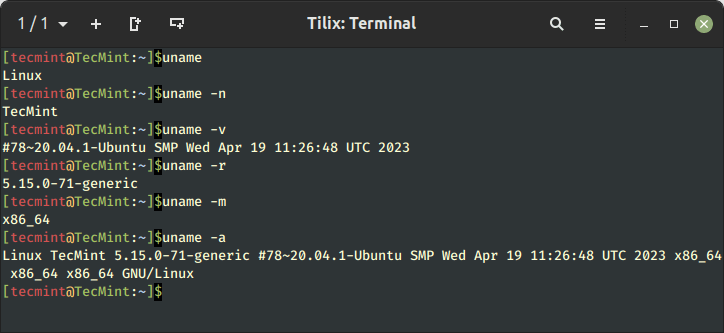
Learn 11 essential Linux commands to check hardware info including CPU, RAM, disk, USB, and PCI…
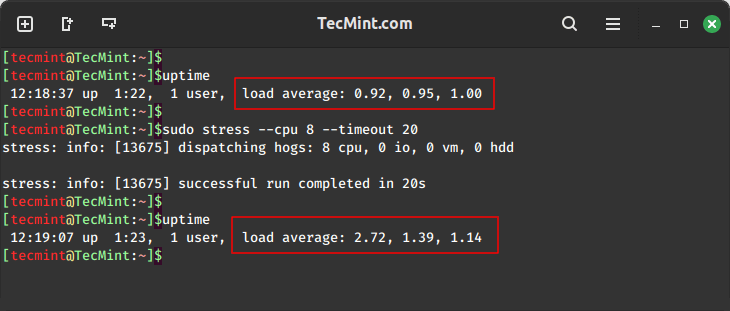
In this guide, we will explore two important tools, stress and stress-ng, for conducting comprehensive stress…
I’m delighted to announce CrowdStrike’s intent to acquire Seraphic, the leader in browser runtime security. With…
Pillar #1: A Rich Corpus of Human-refined Data In cybersecurity, AI agents don’t operate in a…
The AI era is here — and it’s redefining cybersecurity. Organizations around the globe are adopting…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…
CrowdStrike uses NVIDIA Nemotron open models in CrowdStrike Falcon® Fusion SOAR and CrowdStrike Charlotte AI™ AgentWorks….
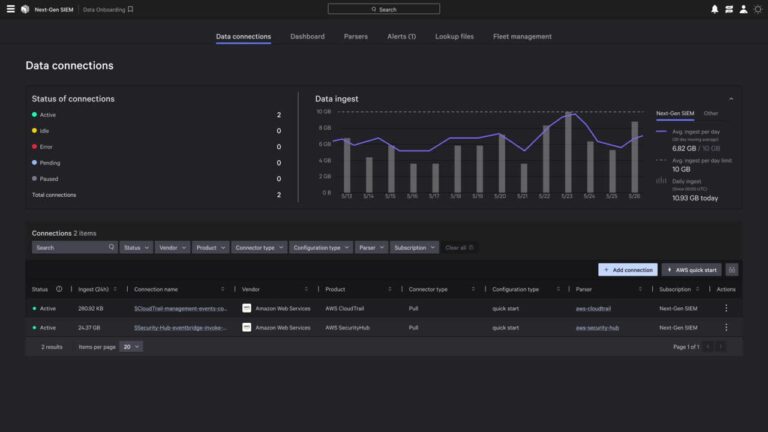
Perform on-demand queries for forensics, compliance, or audit use cases. CrowdStrike is the first cybersecurity partner…
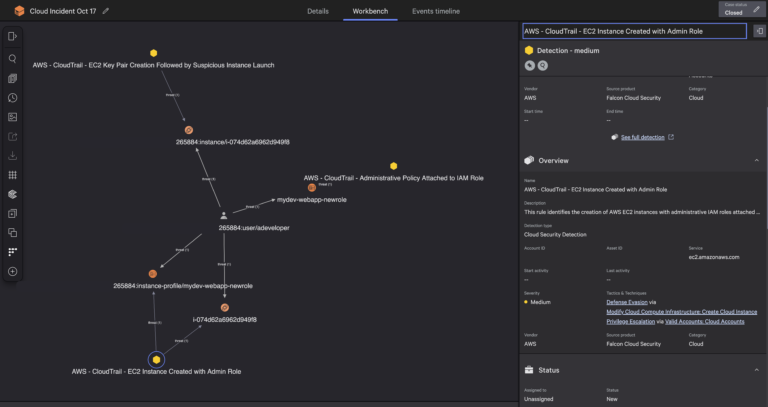
Falcon Cloud Security has implemented a new approach which processes cloud logs as they stream in…
DeepSeek-R1’s Intrinsic Kill Switch …based in Taiwan …run by Uyghurs “Falun Gong is a sensitive group….
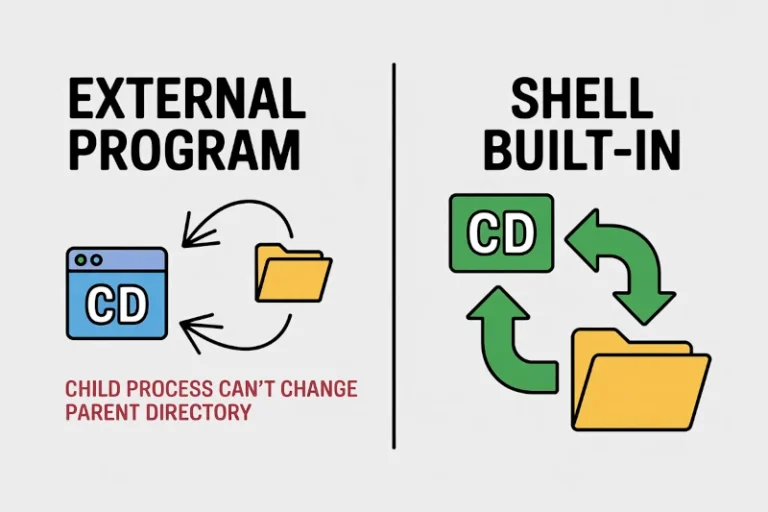
In Linux, the ‘cd‘ (Change Directory) command serves as a fundamental navigation tool for both newcomers…
Key capabilities:Using the single Falcon sensor, organizations can move from deployment to complete XIoT visibility in…