February 2026 Patch Tuesday: Six Zero-Days Among 59 CVEs Patched
Actively Exploited Zero-Day Vulnerability in Windows Remote Desktop The vulnerability allows local attackers with no privileges…
Actively Exploited Zero-Day Vulnerability in Windows Remote Desktop The vulnerability allows local attackers with no privileges…

– System Engineer, IT Services “Overall, it’s been a valuable and eye-opening experience. The tool has helped…
Expert Agents: Native AI Reasoning Across the Falcon Platform Effective threat triage requires correlating evidence across…
Actively Exploited Zero-Day Vulnerability in Windows Desktop Window Manager CVE-2026-20955 and CVE-2026-20957 are Critical remote code…
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI…
Zero-Day Vulnerability in Windows Cloud Files Mini Filter Driver The CrowdStrike Falcon platform regularly collects and…
The outcomes that matter most — speed, accuracy, cost, and real-time risk reduction — can only…
Zero-Day Vulnerability in Windows Kernel When successfully exploited, attackers can gain SYSTEM privileges by winning a…

These reports include:With Falcon Cloud Security data correlated in Falcon Next-Gen SIEM, teams can detect cross-domain…
Coerced Authentication The initial reconnaissance and setup phase requires minimal resources but careful planning. The attack…
This isn’t just about saving time. It’s about enabling every stakeholder to see, understand, and act…
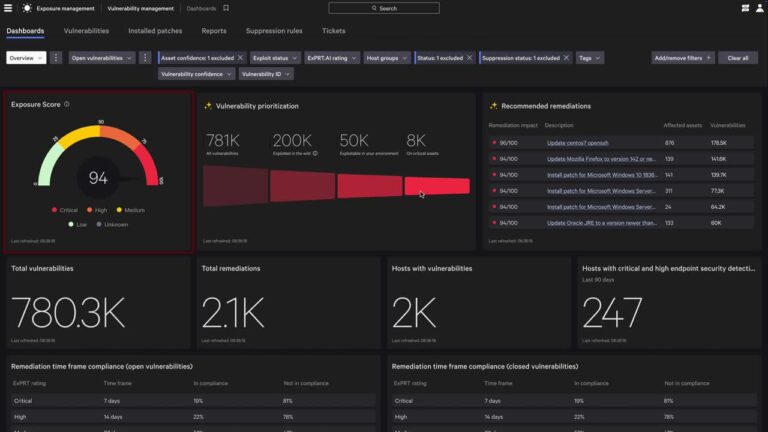
ExPRT.AI is trained to rank vulnerabilities based on how likely they are to be exploited in…

Unauthorized use of RMM tools has become especially dangerous: Throughout 2024, eCrime actors frequently used RMM…
Windows 10 End of Support Is Here There is evidence of active exploitation in the wild…
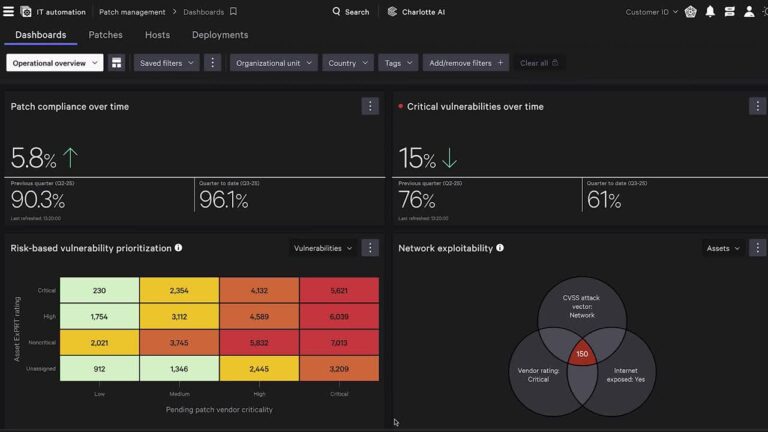
Traditional vulnerability management is broken. Security teams rely on one set of tools to find vulnerabilities;…