CrowdStrike Falcon Scores Perfect 100% in SE Labs’ Most Challenging Ransomware Test
SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…

SE Labs employed both direct attacks and deep attacks. Test results and the feedback of third-party…
– System Security Manager, Services (non-Government) IndustryThe truest assessment of the Falcon platform comes from the…
Traditional security tools were never built to protect AI assets across domains or the new AI…
Unsupported operating systems have historically become adversary targets. The longer a system remains unsupported, the more…
The fundamental shift we’re seeing is moving security professionals from operators to orchestrators. Today, we have…
With Pangea, CrowdStrike will extend this protection into the interaction layer of AI to secure how…
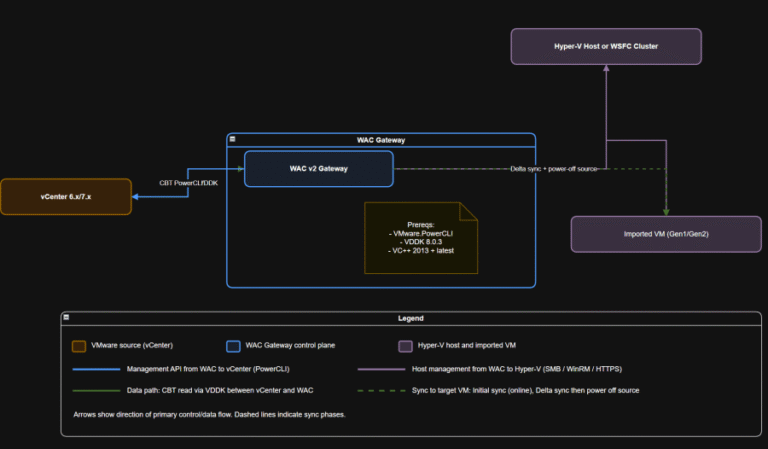
Compliance checkpoints (examples) Why this matters Bridge strategy: If you are standardizing on Windows Server and…
Why Falcon Exposure Management Stands Out Partner Ecosystem: Our strong ecosystem and extensibility make it easier…

These tactics are part of a broader shift. As adversaries increasingly rely on unmanaged infrastructure to…

The real-world assessments conducted by respected testing authorities such as AV-Comparatives help ensure the Falcon platform…
“CrowdStrike Falcon is excellent at detecting anomalous activity where traditional antivirus is otherwise incapable of detecting…
The aforementioned processes would likely take weeks or even months when totaling hundreds of terabytes and…
1. Initial Entry and Exploitation After gaining initial access, the adversary moved laterally through the network…
CrowdStrike pioneered the concept of adversary-focused cybersecurity because it’s the most effective way to defend organizations…
Adversaries may tamper with organizations’ infrastructure to facilitate data exfiltration. Some examples include:It is essential to…