15 Useful “ifconfig” Commands to Configure Network Interface in Linux
In this article, you will learn how to list, configure, enable, disable, and troubleshoot network interfaces…

In this article, you will learn how to list, configure, enable, disable, and troubleshoot network interfaces…
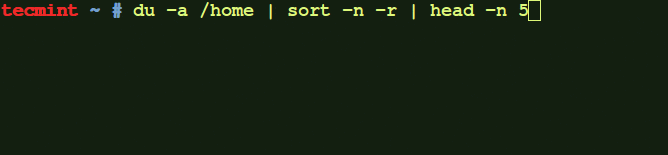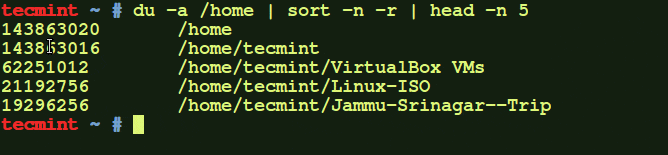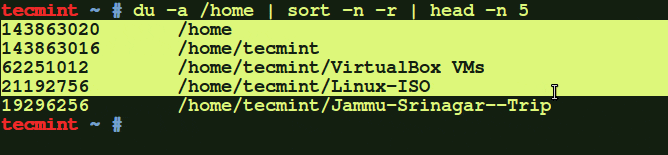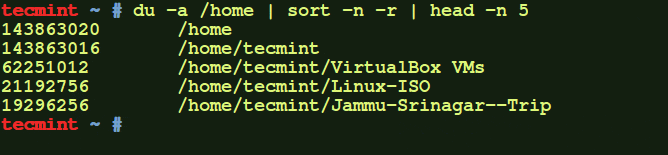
As a Linux administrator, you must periodically check which files and folders are consuming more disk…
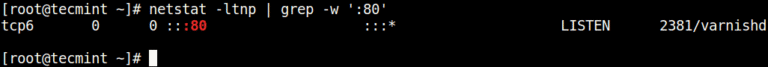
In this article, you will learn how to find which process or service is listening on…
In this article, you will learn how to use the Linux column command to format text…
Learn how to enable and configure AI agents in ONLYOFFICE Desktop Editors to automate document editing,…
In this guide, we feature some of the best Linux distributions that you can install on…
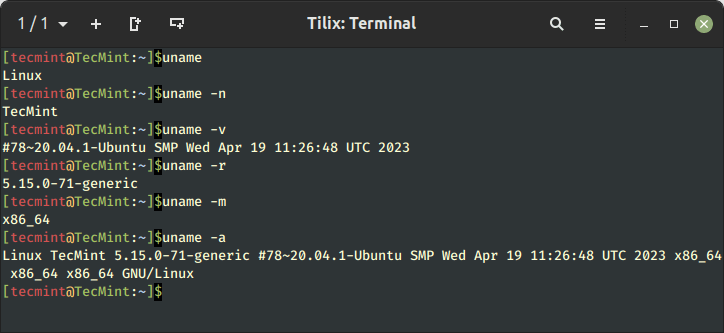
Learn 11 essential Linux commands to check hardware info including CPU, RAM, disk, USB, and PCI…
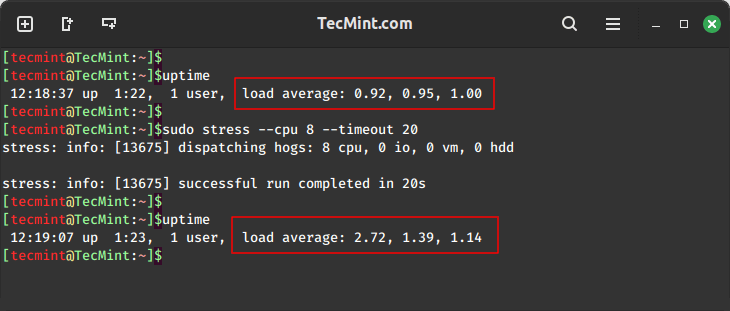
In this guide, we will explore two important tools, stress and stress-ng, for conducting comprehensive stress…
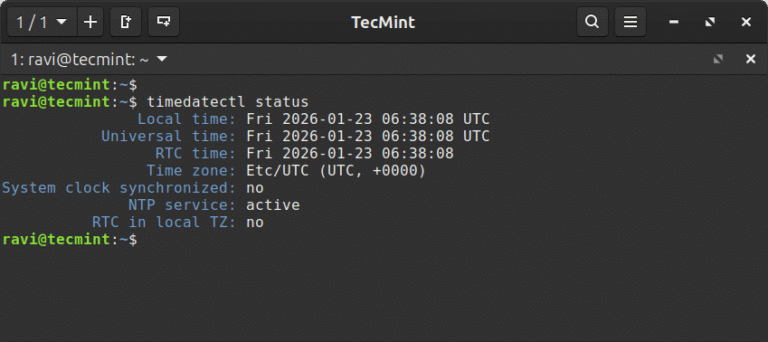
In this article, learn how to set time, timezone, and synchronize your Linux system clock with…

In this article, we show you how to encrypt files with GPG in Linux, generate key…
Updated: This article has been refreshed to cover the latest ways to edit documents on Ubuntu…
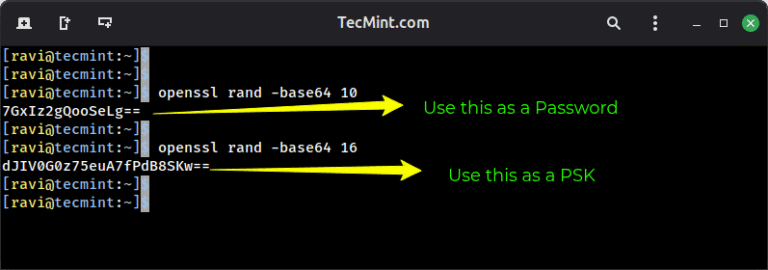
There are so many benefits of using a VPN (Virtual Private Network), some of which include…
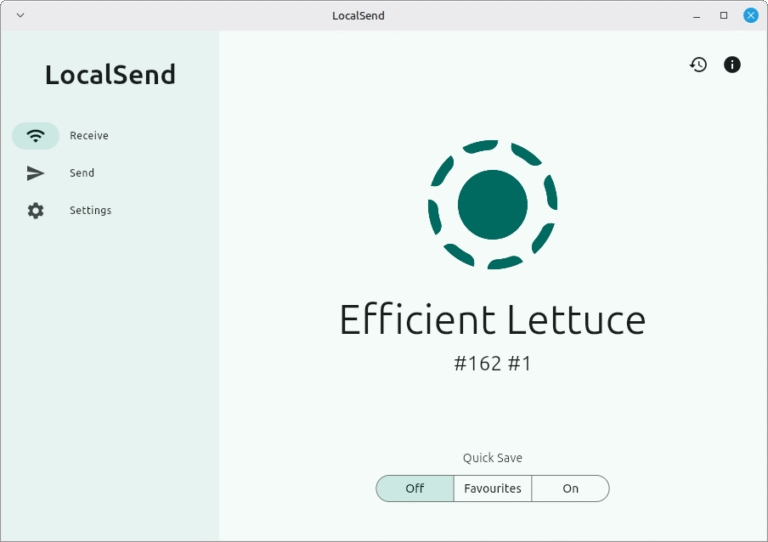
One of the most important uses of a network is for file sharing purposes, and there…

When most people think about operating systems, they picture Windows laptops or MacBooks, but here’s what’s…

When someone visits your website, their browser and your server exchange information back and forth. Without…