Introduction
Workflow 2: Telemedicine Visit
Table of Contents
- Executive Overview
- Healthcare Security Challenges
- Solution Architecture Overview
- HIPAA Technical Safeguards: Key Requirements
- Azure Local and SDN for Secure Healthcare Networks
- Entra: Modern Identity and Access Control
- Real-World Scenario: Patient Data Access & Clinician Workflows
- Mapping to HIPAA Safeguards
- Lessons Learned & Best Practices
- Conclusion
1. Executive Overview
Healthcare security is a journey, not a destination. By combining Azure Local, SDN, and Entra, healthcare organizations can deliver secure, modern clinician experiences while demonstrating technical HIPAA compliance. The flexibility of hybrid and fully local designs lets you balance privacy, security, and agility, no matter how requirements evolve.
- Patient health information (PHI) remains protected at rest and in transit
- Only authorized clinicians access the right data, at the right time, from anywhere
- Security controls are automated, audited, and aligned with HIPAA requirements
2. Healthcare Security Challenges
# Create a secure VNet for EMR workloads
New-AzVirtualNetwork -Name 'EMR-VNet' -ResourceGroupName 'Healthcare' -Location 'local' -AddressPrefix '10.10.10.0/24'#image_title
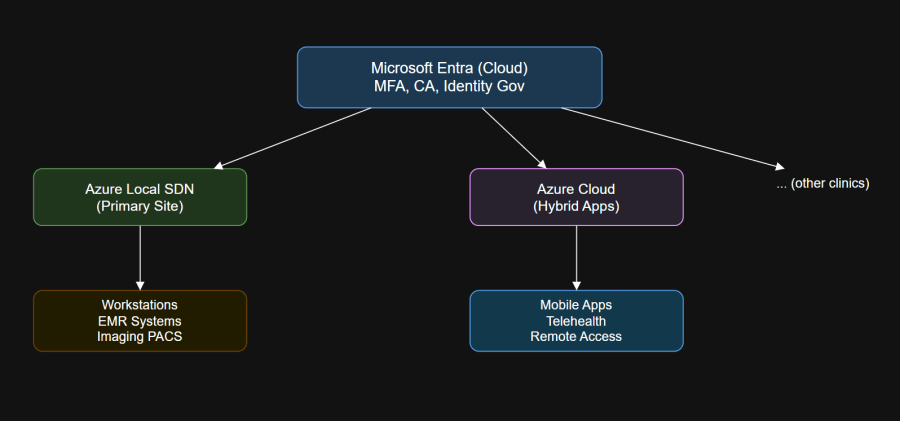
High-Level Components:
- Azure Local (Azure Stack HCI): Provides private, on-prem cloud capability for sensitive workloads and local data residency.
- SDN Express: Delivers software-defined microsegmentation, dynamic network isolation, and secure gateways for hybrid connectivity.
- Microsoft Entra (ID, Conditional Access, Identity Governance): Unifies identity management, supports zero trust principles, and delivers advanced authentication and compliance automation.
HIPAA mandates several technical controls to protect PHI. The most relevant for this architecture include:
4. HIPAA Technical Safeguards: Key Requirements
All access to PHI requires at least two factors—something users know and something they have.
- Access Control (§164.312(a)): Only authorized users may access ePHI.
- Audit Controls (§164.312(b)): Systems must record and monitor access.
- Integrity Controls (§164.312(c)): Protect against improper data alteration.
- Authentication (§164.312(d)): Verify identities before access.
- Transmission Security (§164.312(e)): Guard ePHI against unauthorized transmission.
5. Azure Local and SDN for Secure Healthcare Networks
a. Network Microsegmentation
SDN Express enables granular segmentation of network traffic. Each clinical application, device group, or department is assigned to a separate virtual network segment.
- Example: EMR servers are isolated from research data, radiology imaging, and IoT devices.
- Benefit: If an endpoint is compromised, lateral movement is blocked by default.
Healthcare organizations face enormous pressure to protect patient data while supporting efficient clinician workflows. Compliance requirements like HIPAA, growing cybersecurity risks, and hybrid work models make secure access design both vital and complex. In this case study, we explore how a modern healthcare provider leverages Azure Local, Software-Defined Networking (SDN), and Microsoft Entra to build a robust, HIPAA-aligned architecture for secure patient data access and seamless clinician experiences.
Policies enforce risk-based access, evaluating user role, device compliance, location, and sign-in risk.Architecture Diagram:Sample PowerShell for SDN Microsegmentation:
b. Secure Remote Access
- Site-to-site VPNs or Azure SDN Gateways connect remote clinics and authorized third-party providers.
- Point-to-site VPN allows clinicians to connect from home or mobile using strong authentication.
6. Entra: Modern Identity and Access Control
a. Multi-Factor Authentication (MFA)
A regional healthcare provider needed to modernize its clinical systems to support secure remote access, mobile charting, and telemedicine, all while reducing data breach risk and maintaining HIPAA compliance. By adopting Azure Local (Azure Stack HCI), SDN Express, and Microsoft Entra, the organization created an environment where:
- Example: Clinician signs in using a password and a mobile authentication prompt.
b. Conditional Access
The solution combines hybrid and fully local Azure infrastructure, advanced network segmentation, and modern identity governance.
- Example: Clinicians can access EMR from hospital subnets without extra challenge, but require step-up authentication from outside locations.
c. Identity Governance
- Access Reviews: Periodic checks ensure only current staff retain access.
- Privileged Identity Management: Elevation of admin rights is just-in-time and requires approval.
- Audit Trails: Every access and change is logged, mapped to user identity.
Disclaimer: The views expressed in this article are those of the author and do not represent the opinions of Microsoft, my employer or any affiliated organization. Always refer to the official Microsoft documentation before production deployment.
{
"conditions": {
"users": {"include": ["ClinicianGroup"]},
"locations": {"exclude": ["HospitalSubnets"]},
"clientAppTypes": ["All"]
},
"controls": {"mfa": true}
}
7. Real-World Scenario: Patient Data Access & Clinician Workflows
Workflow 3: Role Change & Identity Governance
- Patient initiates a telehealth session using a secure app connected to Azure Local.
- Session traffic is segmented by SDN Express, preventing other network traffic from interfering.
- Clinician accesses patient charts and imaging, with audit logs tracking each step.
# Allow RDP/SSH only from secure jumpboxes, block all other inbound
- Staff member changes departments.
- Entra triggers an automated access review. Non-required roles are removed.
- Access rights to previous systems (e.g., research data) are revoked.
- All changes are logged for audit readiness.
8. Mapping Solution to HIPAA Safeguards
| HIPAA Safeguard | Azure Local/SDN/Entra Implementation |
|---|---|
| Access Control | Role-based, conditional access, segmented networks |
| Audit Controls | Entra logs, SDN logs, Power Automate reporting |
| Integrity Controls | NSG rules, data validation, privileged identity mgmt |
| Authentication | MFA, device compliance, JIT admin elevation |
| Transmission Security | Encrypted SDN flows, VPN, TLS for app access |
9. Lessons Learned & Best Practices
- Automate Everything: Use PowerShell, ARM/Bicep, and Entra workflows to standardize and monitor access.
- Least Privilege by Default: Only grant the minimum required access, then layer monitoring on top.
- Continuously Review Access: Use Entra identity governance features to avoid “zombie accounts.”
- Document and Audit: Routinely export logs and configuration for HIPAA readiness.
- Plan for Hybrid: Blend cloud and local to meet strict data residency and uptime requirements.
10. Conclusion
Healthcare networks are high-value targets due to sensitive data and complex workflows. Key security and compliance challenges include:
#image_title